Bleepingcomputer posted: "Reports are coming in from multiple security researchers and security firms about increased activity from one of the groups spreading the Locky ransomware.
These spam waves have started on September 18 and are pushing the new Locky ransomware variant that encrypts files with the .ykcol extension, which was also released on the same day.
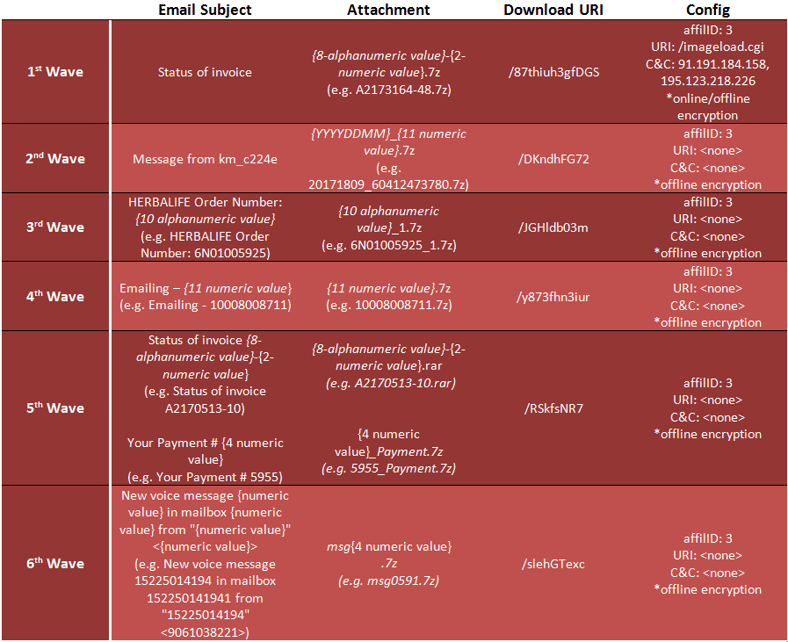
Six big spam waves detected
Six big spam waves pushing the Locky ykcol version were seen in the past few days. Locky versions distributed by these spam waves have embedded the #3 affiliate ID, belonging to the same group that was also busy pushing Locky spam at the start of the month.
These Locky spam waves have been seen by Fortinet (authors of the graph breakdown below)
The spam waves had an immediate impact on submissions from infected users on ID-Ransomware, a service that lets users identify the type of ransomware that infected their PC. Security researcher Derrick Farmer also noted that recent versions of Locky ykcol returned to asking victims to pay a ransom demand of 0.5 Bitcoin (~$1,800) after initial versions spotted on September 18 asked for 0.25 Bitcoin (~$900).
Bleeping Computer understands that at the time of writing, the increased spam activity from Locky affiliate ID #3 is still ongoing. There is no known method of breaking Locky encryption, so users are advised to be careful when downloading and running attachments, or clicking on links in emails from unknown senders.
Get the most informative and complete ransomware hostage rescue manual.
This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.
PS: Technically speaking, your users are the new DMZ, and you have to create a human firewall. Effective security awareness training really is a must these days. Find out how affordable this is and be pleasantly surprised.
Related Pages: Ransomware





