
The Scarab ransomware strain is updated again and spreads via Necurs botnet in a massive 12.5 million campaign, mostly targeting .com domains.
Scarab was spotted June 2017 for the first time, appending the .scarab file extension to the files. Later it was updated and started using .scorpio suffix to make files inaccessible.
The current campaign is spreading a third updated version of the ransomware which in order to prevent users from using third-party recovery tools, deletes Shadow Volume Copies and other default Windows recovery features.
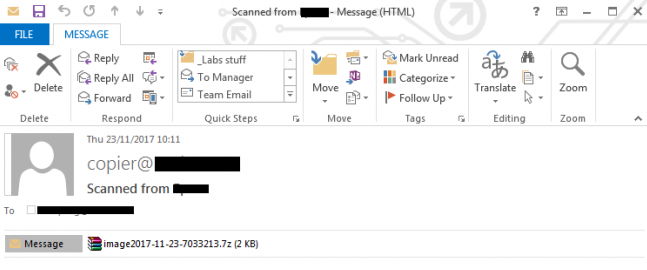
Although this cybercrime gang is smaller, they are pros in social engineering and know the successful tactics to manipulate people into opening a malicious attachment. Currently, Scarab’s payload is included into the emails with fake images of scanned documents and have subject lines like:
- Scanned from Lexmark,
- Scanned from Epson,
- Scanned from HP,
- Scanned from Canon.
Here is the screen shot:
Unusually, the note does not specify the amount being demanded, instead simply stating that "the price depends on how fast you write to us". This note is also automatically opened by the malware after execution.
I strongly suggest you get a quote for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP, because your filters never catch all of it. Get a quote now and you will be pleasantly surprised.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO, KnowBe4, Inc






