 Think Before You Click On Random Google Doc Invitation Links
Think Before You Click On Random Google Doc Invitation Links
A very convincing Google Docs phishing scheme raced through the internet yesterday, looking like it came from someone you know. It was almost spreading as fast as a real computer worm, but this was driven by social engineering the end-users instead. Looks like a million people fell for it in less than an hour. Google fixed it very fast though.
If an end-user clicked the link, it asked for access permissions to their Gmail account which actual Google Docs links would not need. But this granted permissions to a malicious third-party web app that was simply named “Google Docs,” which gave phishers access to the user's email and address book, and then spammed everyone in their contacts with the same link to that bogus Google Docs file. They, in turn, email everyone in their contacts, and so on like a human-powered computer worm. All of them include the same email address @mailinator.com. Here is how it looked:
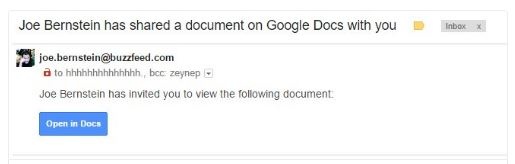
Social Engineering Tricks User To Give Access To Malicious Third Party App
The difference between this and your run-of-the-mill credentials phishing scheme is that this attack doesn’t just take the user to a bogus Google page and collects their password — a red flag something the user could see by checking the page URL. It works within Google’s system, but takes advantage of the fact that you can create a non-Google web app with a misleading name. Here’s what the permissions screen looks like, for example:
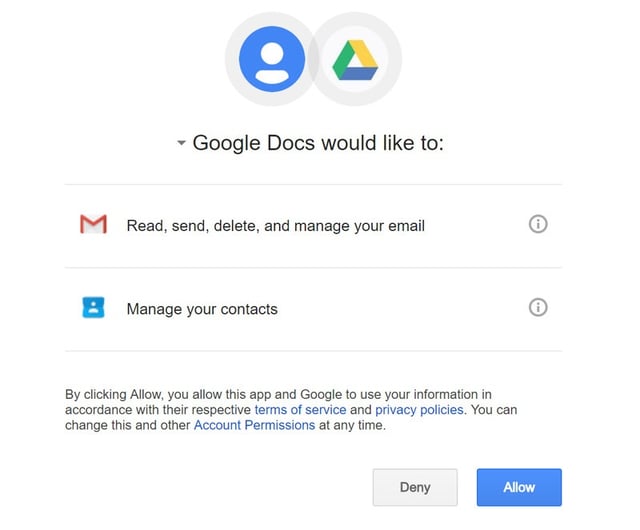 If a user clicked Allow, their account has already sent spam messages to the people in their address book. But they can revoke future access through Google’s “Connected Apps and Sites” page; where it will appear as “Google Docs.”
If a user clicked Allow, their account has already sent spam messages to the people in their address book. But they can revoke future access through Google’s “Connected Apps and Sites” page; where it will appear as “Google Docs.”
Google said in a statement that they responded to the attack with a combination of automatic and manual actions and disabled the accounts where the hack originated: “We’ve pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail.” but Google did not specify yet where the attack came from and said the attack "affected fewer than 0.1% of Gmail users." Which means about 1 million.
"We were able to stop the campaign within approximately one hour," the statement added. "While contact information was accessed and used by the campaign, our investigations show that no other data was exposed."
If a user tries to click on the link to the suspicious Google Doc now, they will see a screen saying "We're sorry...but your computer or network may be sending automated queries. To protect our users, we can't process your request right now." Here is a blow-by-blow on Reddit.
Obviously, an end-user who was trained to spot social engineering red flags like this would have thought before they clicked.
I strongly suggest you get a quote for new-school security awareness training for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP. If you don't, the bad guys will, because your filters never catch all of it. Get a quote now and you will be pleasantly surprised.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO, KnowBe4, Inc






