By Eric Howes, KnowBe4 Principal Lab Researcher.
This Monday morning many of our customers came in to work to find a rather rude surprise lurking in their inboxes: a massive Cerber ransomware campaign delivered through somewhat unusual phishing emails. Cerber is a sophisticated ransomware strain first seen back in March. It has undergone constant development since its debut "in the wild."
Cerber is also noteworthy inasmuch it is distributed via a Ransomware-as-a-Service (RaaS) model -- meaning, your users could encounter Cerber campaigns being run by a number of malicious actors through a variety of attack vectors.
Although Cerber campaigns have been growing in size for several months now, the month of September was marked by several sharp spikes in Cerber activity, as documented by malware researchers. Monday 10/3/2016 saw the largest spike yet.
The Phish
We noticed a large volume of Cerber ransomware phishing emails (forwarded to us by customers via the Phish Alert Button) starting early Monday.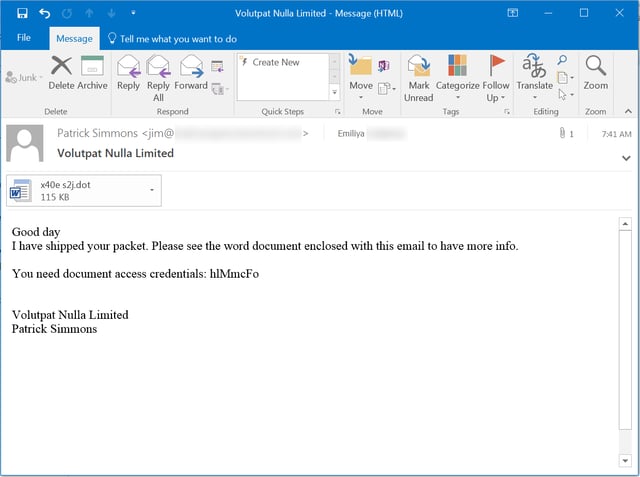
These malicious emails were noteworthy for several reasons. First, the emails used a series of different, yet remarkably similar Subject: lines and social engineering hooks. Among the Subject: lines we observed:
Subject: Egestas Associates
Subject: Ac Libero Nec PC
Subject: Velit Eu Sem Corp.
Subject: Metus In Lorem Inc.
Subject: In Corp.
Subject: Massa Quisque Institute
Subject: Scelerisque Neque Sed Consulting
Subject: Torquent Limited
Subject: Luctus Ipsum Leo Ltd
The social engineering hooks in the email bodies were all small variations on the same basic claim:
I finally sent your pack. Please see the document provided with this email to view more details.
I finally sent your package. Please see the file given below to get more details.
I finally sent your packet. Please open the report provided with this email to view more information.
I finally shipped your order. Please open the file given with this email to have more info.
I finally shipped your pack. Please check the doc file provided with this email to have more info.
I have finally shipped your packet. Please check the statement attached below to view more information.
I have finally shipped your pack. Please check the document provided here to have more details.
I have sent your pack. Please check the statement given below to get more info.
I have shipped your package. Please open the doc file provided with this email to view more info.
Most remarkable, however, was the attached Word document, a password-protected .DOT (Word doc template) file. Users who opened the the attachment were prompted to enter a password, which had been provided in the email body (see the example phishing email above).
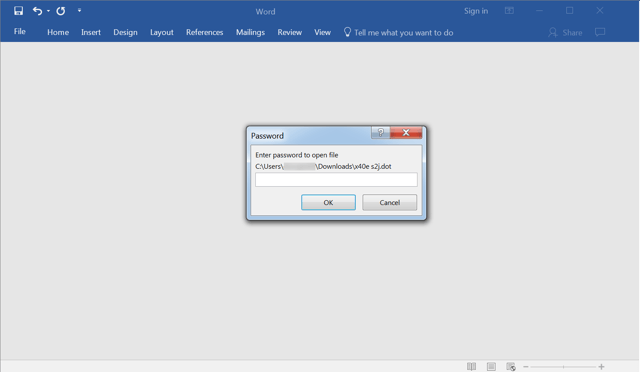
Password-protecting the Word document accomplished two things for the bad guys. Not only did this password-protection scheme encrypt the embedded malicious macro, thus foiling easy detection by anti-virus scan engines, it also lent the user experience an air of additional security, reinforcing the sense amongst gullible users that the document they were handling was in fact safe.
We suspect the bad guys reckoned the advantages gained from this document protection scheme would more than off-set the loss of potential victims (the more required clicks you throw in front of users, the fewer of them will see the process through to the end). In fact, AV detections for the password-protected .DOT files that we checked on VirusTotal were non-existent. Even 24 hours later detections among major AV engines remains sparse.
Users who successfully unlocked the document were then confronted with a screen prompting them to click the yellow security warning bar (a standard Office security feature) just under the main menu bar to enable the malicious macro embedded in the document.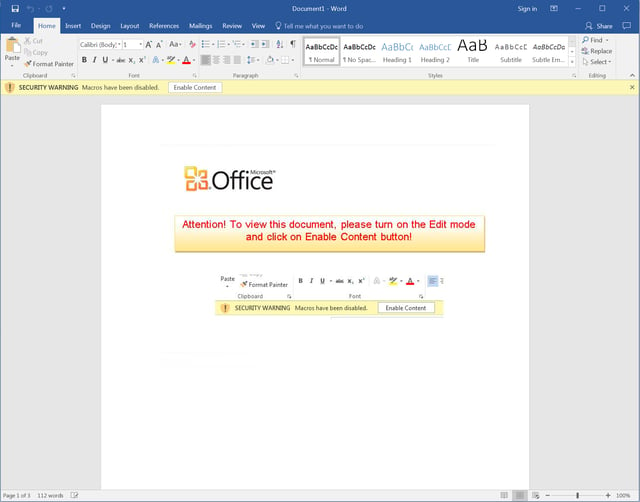
This screen is not only fairly typical of other macro warning screens we've encountered with malicious phishing attachments but one that has been used with previous Cerber phishing campaigns.
Users who stubbornly plow on and enable macros in the malicious document will quickly see files on their PCs encrypted after the malicious macro pulls down Cerber from a remote server. On one of our test machines the Windows Explorer shell itself crashed, leaving only a ransom note on the desktop.
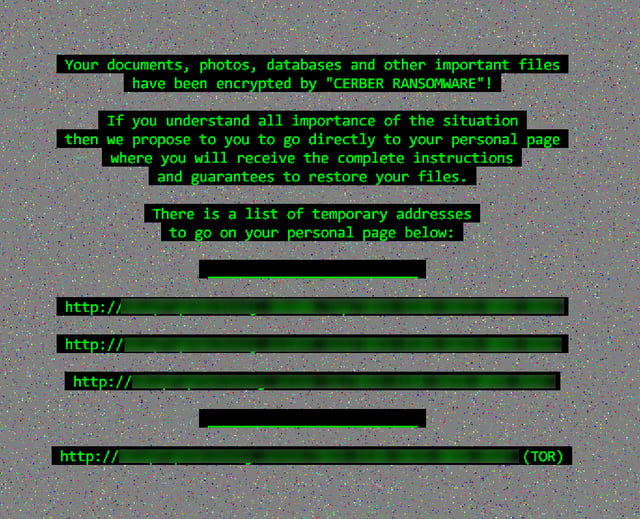
The Cerber Bitcoin payment page is the same one used by this ransomware variant for the past few months, though victims must now navigate a captcha process that was added back in August to defeat a free decryptor developed by Check Point. 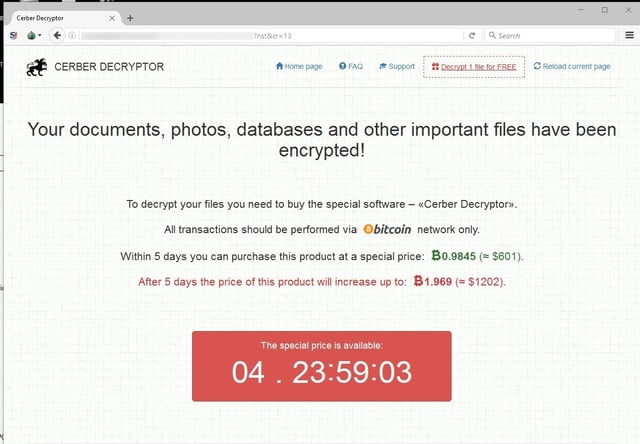
The ransom demanded in our test case was just shy of 1 BTC (~$600 USD), with the amount increasing to approximately 2 BTC after five days.
The Campaign
This Cerber campaign caught the attention of a number of malware researchers online. The folks at MalwareTechBlog began calling attention to the remarkable size of the campaign early in the morning.
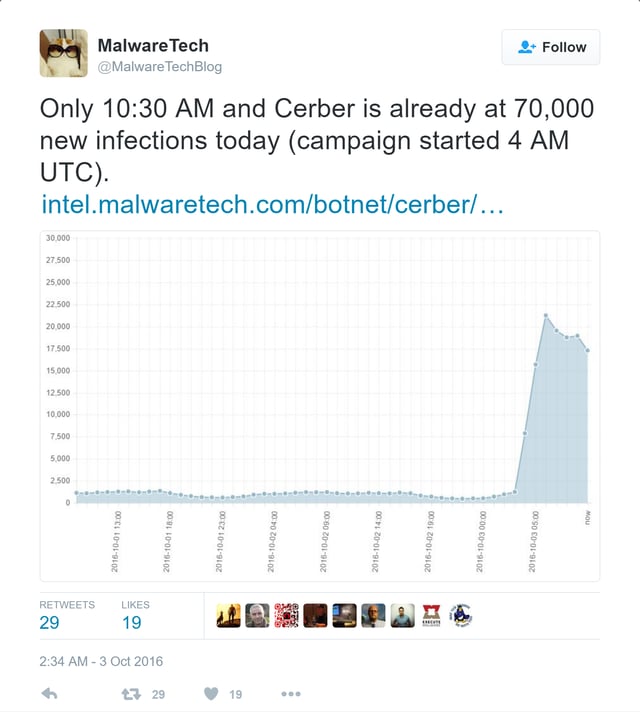
By the end of the day it was apparent that the ongoing campaign far exceeded any of the earlier spikes in Cerber infestations documented by MalwareTech over the preceding few weeks in September.
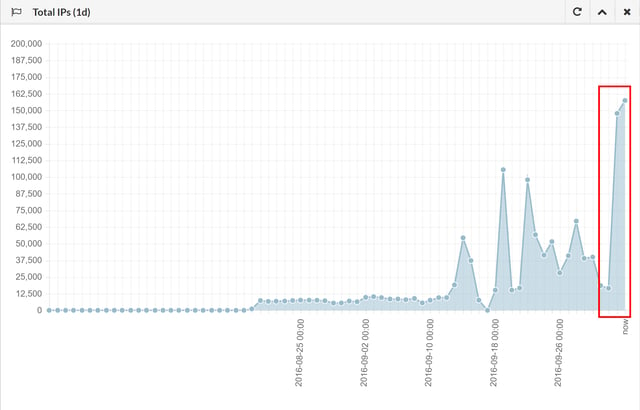
Given that Cerber is distributed through a Ransomware-as-a-Service (RaaS) model, we cannot definitively say that this eye-opening phishing campaign is the primary factor driving that rather large spike in infestations. Cerber has been distributed through several other attack vectors in recent months, including exploit kits used in conjunction with malvertising campaigns. It is most certainly a significant contributing factor, though.
The Consequences
Cerber is a textbook example of the relentless innovation that we are seeing from malicious actors. Introduced just over six months ago, this ransomware strain has undergone continuous development to harden its malcode against detection, expand its malicious functionality, and defeat attempts to provide victims with free decryptors. Distributed via multiple attack vectors by a collection of malicious actors, Cerber is precisely the kind of threat designed to land in your users' inboxes undetected, making your Monday mornings even more unpleasant than they already are.
Your overburdened (and under-appreciated) IT staff cannot and should not have to face these kinds of Monday mornings alone. They need allies. And that means getting your employees trained to spot new, malicious threats lurking in their inboxes, even when the bad guys are using new tricks designed to social engineer your users into clicking through apparently "safe" or "secure" attachments and opening your network to a costly and highly disruptive ransomware attack.
See this new-school security awareness training platform yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




