I mentioned a few months ago that I expected something like this, but it has materialized faster than I expected.
The worm has the capability to hijack MS-Outlook and send emails with itself attached. It uses social engineering to infect other users. The Dyre malware was specifically developed to steal money out of online bank accounts and uses an I2P address to stay anonymous and mask the location of the Control & Command server.
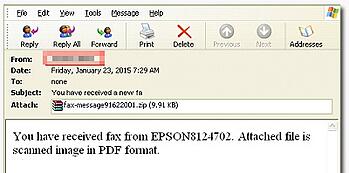
This new variant spreads itself via phishing emails which have a "fax-attachment" that the user needs to open. It claims that a package was not delivered, and tricks the user to open the attachment. But opening the attachment infects the workstation and installs a worm which sends itself via the user's Outlook to other email addresses specified by the C&C server. At this point in time it does not use the user's Outlook contact list like worms used to do in the past.
After the emails have been sent, the worm deletes itself to further obfuscate being discovered and disassembled. Trend Micro has a highly technical write-up with pictures of the infection chain.
If this type of attachment makes it though your spam filters and your users open it, your organization can now be used as an infection vector to spread this worm anywhere in the world, using email address targets that the C&C servers specify. This is a potential legal liability that needs to be taken into account when your organization implements security awareness training.
Find out how affordable this is for your organization today.





