If you're working the trenches in your organization's IT department, then one of your more consistently annoying headaches involves passwords. Users and their passwords are the ongoing drama that keep you and your staff entertained day in and day out.
If your users resemble those at most other organizations, then you know they routinely choose epically bad passwords (i.e., the kind the never fail to appear in just about every data breach dump known to god and man); they love recycling those oldies but goldies; and, no matter what sage advice or password management tools you offer them, they always seem to forget them.
Well, there is good news on that front. The bad guys are here to help!
You see, malicious actors feel your pain. And they know your users almost as well as you do. So, they've decided to step into the breach (pun intended) and help you and your users address all your password management problems.
The advice they're offering your users is fairly simple and straightforward. Can you guess what it is?
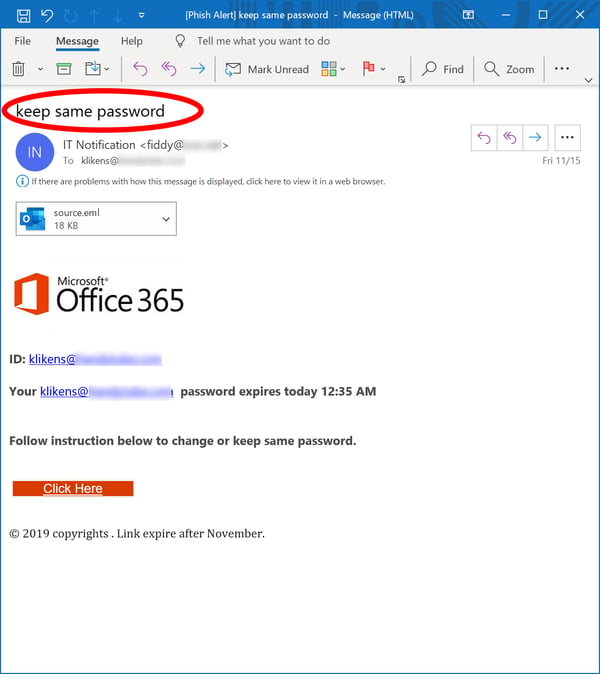
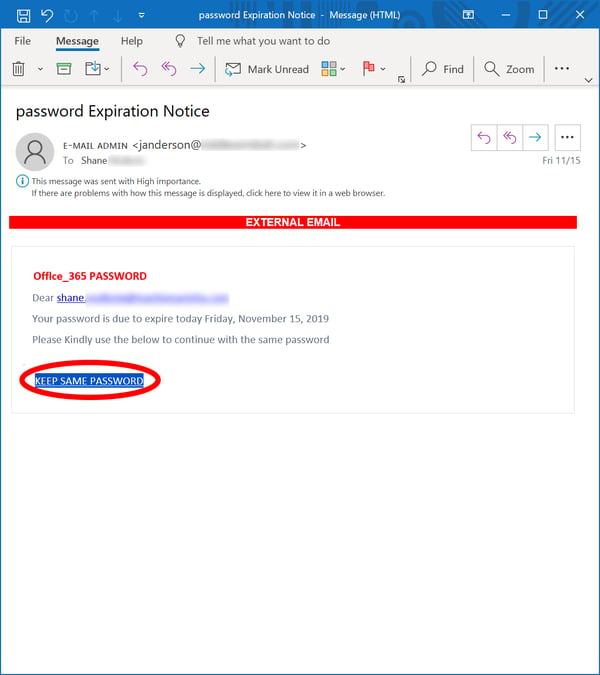
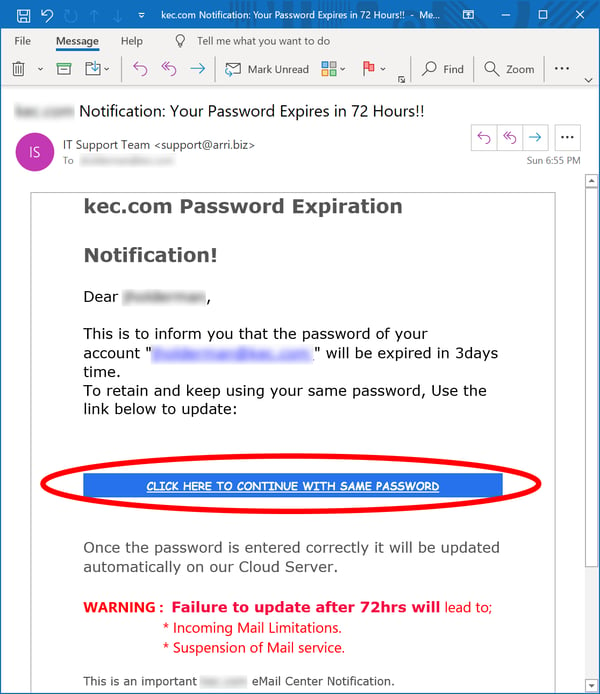
Yeah, you sort of already knew it was going to be that one, didn't you? It's what most of your users want to do. It's what all too many of your users are already doing and have been doing for years. And the bad guys have figured out that one of the easier ways to get your users to cough up login credentials to your network is to simply give them what they want.
It's a simple, powerful social engineering strategy almost guaranteed to work with a significant percentage of any organization's workforce. Why? Let us count the ways.
- Password management really is a PITA -- for both you and them. Why should they pay any mind to that pesky IT person when emails like the above are offering to let them do what they want and keep their lives simple?
- It's a safe bet that many of your users really have no idea what emails from their own organization look like -- not even routine password reset notifications and prompts that they've seen time and again.
- Finally, all too many users either don't get it -- with "it" being good security practices -- or simply do not care.
Phishing emails using this particular social engineering trick ought to be easy to spot. If your users have even a basic understanding of good practices, they should recognize that no IT organization worth its salt is going to offer to let them keep re-using old passwords. Doing so pretty much defeats the entire point of periodically prompting users to change their passwords in the first place.
The question is: are your users security savvy? Do they know and understand good password practices? Have they been trained to spot obvious phishing emails such as the ones exhibited above? And how many of them have taken the bad guys' advice to heart and continue to recycle old passwords -- even those that have already been compromised in a data breach (and were likely never very secure to begin with)?
Why not find out? Like right now.
First, test your users to find out just how many of them are vulnerable to the kinds of phishing emails that are undoubtedly already landing in their inboxes. Then, use two free tools to figure out how just many of your users are currently using compromised or just plain weak passwords. Finally, explore all the different ways that New-school Security Awareness Training can get your users up to speed on how to spot and stop phishing attacks.
Don't fight the user/password battle alone. Real help is available for you and your users. And it offers a much better strategy for handling the problem then letting malicious actors do it for you.
 Here's how it works:
Here's how it works:




