 Unless you recently beamed down from Mars, you are undoubtedly aware that election season is upon us in the United States. Indeed, the upcoming U.S. Presidential Election is currently competing for eyeballs with the ongoing COVID-19 public health crisis in news stories as well as social media. To say these are turbulent times would be an understatement.
Unless you recently beamed down from Mars, you are undoubtedly aware that election season is upon us in the United States. Indeed, the upcoming U.S. Presidential Election is currently competing for eyeballs with the ongoing COVID-19 public health crisis in news stories as well as social media. To say these are turbulent times would be an understatement.
Malicious actors are certainly aware of it, judging from an email that was reported to us yesterday by a customer using the Phish Alert Button (PAB).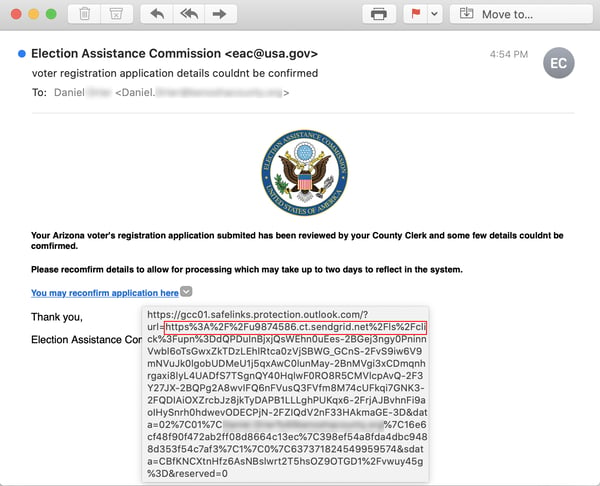
The social engineering tactic being used here is a classic one in which email recipients are told of a problem with one of their accounts (usually a bank account) and are then offered a link to fix or redress the problem.
Although the email itself claims to have been sent by the U.S. Election Assistance Commission, the link in the email sends users to a web page that spoofs ServiceArizona -- part of the state government of Arizona -- complete with images pulled directly from the state's official site.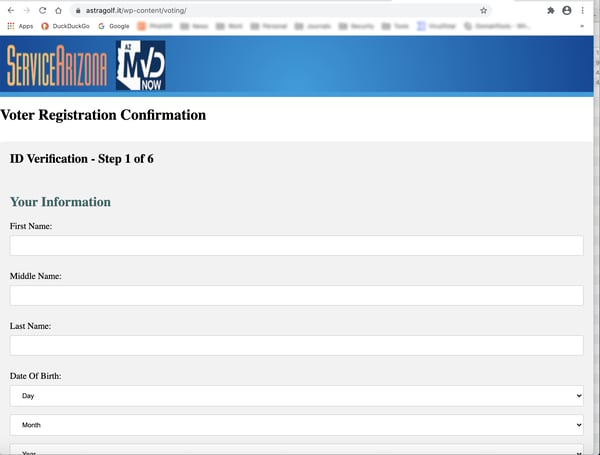
Arizona, it should be noted, is considered a potentially important swing state in the upcoming U.S. Presidential Election. The state also happens to be hosting a hotly contested election for one of the state's two U.S. Senate seats.
Also of interest here is the fact that the email was sent through Sendgrid -- undoubtedly via a compromised account -- which suggests this phish could have been delivered to a large number of email addresses. (Sendgrid, a widely used email service provider, is currently battling a significant problem with compromised accounts that have been exploited by malicious actors to deliver large volumes of phishing emails.)
Curiously, the copy of the email we received was submitted by a customer in Kenosha County, WI -- a locality that has been in the news recently due to widely reported civil unrest in the area. Moreover, like Arizona, Wisconsin is expected to play an important role in the upcoming election.
The spoofed web page consists of a web form requesting a variety of personal data, including:
- name
- date of birth
- mailing address
- email address
- Social Security Number (SSN)
- driver's license information
The web page was taken down within hours after we first accessed it.
An Open Question
What remains unknown at this point is the intent or purpose behind this phish. The data requested could very well be used for identity theft. It is certainly not unknown for malicious actors to solicit such data via phishing emails from unwitting users in order to support a variety of fraudulent endeavors.
Given the election angle, though, we cannot ignore the possibility that this phish may be part of an attempt by parties unknown to intervene in the election, either by seeding confusion and chaos in the election process or engaging in some form of election fraud.
Although we judge it more likely that this phish is being used to fuel identity theft and related acts of fraud, the fact that the email solicits such personal data through the guise of verifying voter registration data is concerning.
Conclusion
Whatever the intent behind this particular phishing attack, it should serve as a reminder that human beings -- users, employees, citizens, and voters -- are "soft targets" for malicious actors. This is especially true in turbulent times such as the present -- when fear, confusion, and doubt are surging in the run-up to a historic election that just happens to fall in the middle of a catastrophic pandemic.
When humans are the target there is no time to lose in stepping your users and employees through New-school Security Awareness Training and testing them regularly with simulated phishing emails modeled on the malicious emails already landing in their inboxes.
 Here's how it works:
Here's how it works:
