Frances Zelazny, Vice President of BioCatch, gave a recent Tech Republic interview to share some insight into how hackers can access your passwords. It's familiar but worth reviewing, since the social engineering tricks don't go out of style.
Zelazny explains what, besides using common free tools like Burp Suite and John the Ripper for brute forcing, sometimes hackers just guess. With limits on the digits in a password, and by enlisting the aid of an automated system, within seconds they often find themselves able to gain access.
More involved methods like phishing aren't high tech, but they're very effective in tricking people into giving up their credentials. A hacker might, for example, pose as an account owner calling a help desk for assistance with a password reset.
Often the help desk will send a link in an email to an address the caller supplies. It can be even simpler: credentials are also often available as a commodity on the dark web for as little as 50 cents.
Zelazny noted that possibly the easiest way hackers can gain data is to call victims, and "pretexting" they're trying to verify information already on file. In most cases the victim will tell the hacker everything they want to know.
In both personal and business relations—and security—training is essential, stressing the importance of vigilance when it comes to divulging confidential personal information. Tech Republic has the story: https://www.techrepublic.com/article/heres-what-happens-during-a-social-engineering-cyber-attack/
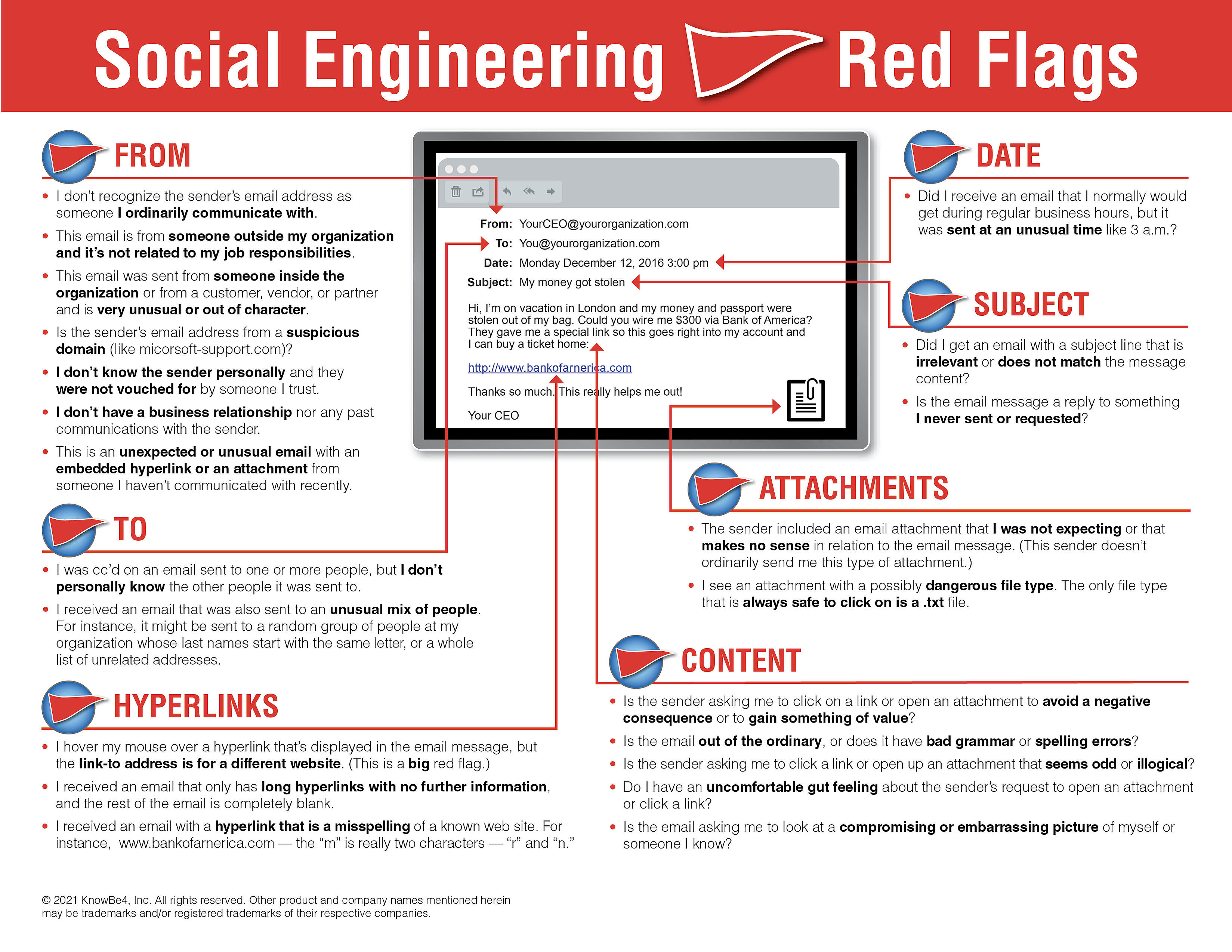
We recommend EVERYONE to review the 22 social engineering red flags to watch out for in any email. It might be a good idea to print out this PDF and pass it along to family, friends, and coworkers. Remember to always think before you click!