Our friend Larry Abrams at Bleepingcomputer wrote August 9th: "Through a large malspam campaign, Locky is back and currently being heavily distributed worldwide.
While Locky was at one point considered the largest distributed ransomware, over time it became much more common to see other ransomware such as Cerber, Spora, and now even GlobeImposter.
While it is too soon to tell if this is just another brief surge or an attempt to become a large player again, what we do know is that this particular campaign is strong with a wide distribution.
Today, security researcher Racco42 discovered a new Locky malspam campaign that was pushing a new Locky variant that appends the .diablo6 extension. This campaign is being distributed through spam emails that contain subject lines similar to E [date] (random_numer).docx. For example, E 2017-08-09 (698).docx. The message body simply states "Files attached. Thanks".
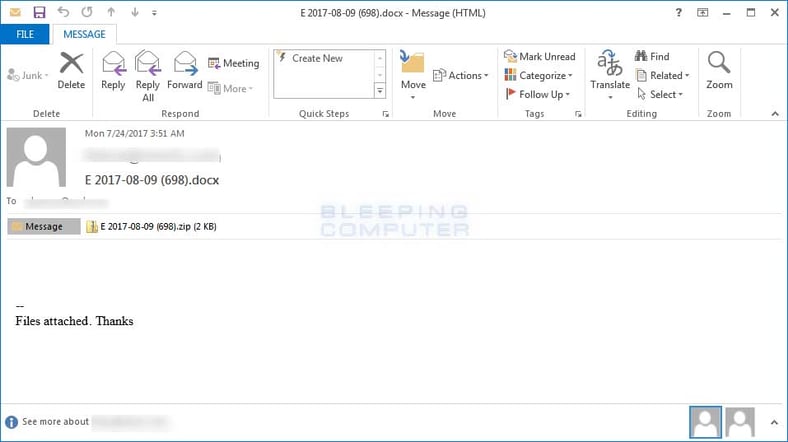
These emails have ZIP file attached that use the same name as the subject line, which contain a VBS downloader script. This script will contain one or more URLs that the script will use to download the Locky ransomware executable to the %Temp% folder and then execute it.
At the time of this writing, the Locky Decryptor TOR payment site has the ransom set to .49 BTC or approximately $1,600 USD, and the encrypted files cannot be recovered, unless you can pull them out of your Shadow Volume Copies, as the Locky code has some bugs and sometimes fails to delete these." Even more technical detail at Bleepingcomputer.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




