Security company Bromium put out a press release asking publicly: "Large Enterprises Spend Nearly $300K Per Year On Security Education, So Why Are Endpoint Attacks More Successful Than Ever?"
Oooh, I like this one! It is so full of holes I don't know where to start... :-D
Here is what they said: "CUPERTINO, Calif., Sept. 14, 2017 (GLOBE NEWSWIRE) -- Bromium®, Inc., the pioneer and leader in virtualization-based enterprise security that stops advanced malware attacks, today released new research which found the cost of security education for large enterprises is at an all-time-high of $290,033* per year per organization, and that user education is rocketing up the CIO’s priority list. Yet despite those investments, the end user remains the greatest risk to the organization’s security from targeted zero-day and nation state threats to common ransomware and phishing attacks.
"The research is based on a survey of 500 CIOs from large enterprises in the US (200), UK (200) and Germany (100). Key research findings include:
- 99 percent of CIOs see users as ‘the last line of defense’ against hackers. This means the burden of securing the enterprise has shifted to user education and often stringent policies and procedures that limit teams’ ability to get work done and puts a tremendous amount of personal responsibility on the end user.
- Based on an average of seven hours of cybersecurity training per employee, large enterprises waste $290,000 per year.
- Skilled employees in HR, legal, IT and risk departments spend an additional 276 hours a year helping to arrange and deliver in-house training.
- Most businesses (90 percent) have used external consultants for over three days (27 hours) a year to review and advise on security policies and procedures.
- 94 percent of CIOs have pushed for increased investment in user education following recent headlines around phishing and ransomware.
Allright, let's address these points and have some fun!
- 99 percent of CIO correctly see users as the "last line of defense" because all in-place security systems (all filters) have failed and the threat sits in the end-user's inbox. In all of its roughly 25 years, endpoint security (antivirus) has not been able to effectively protect workstations and is in fact getting worse. The correct thing to blame is antivirus, and Bromium should position against that, not end-user training.
- A whopping 7 hours of training? Where did that number come from? What are they doing all that time? It's totally unreal. Employees in organizations that use KnowBe4 for awareness training spends about 1-2 hours a year max, and often much less than that. They spend maybe 2 seconds to think before they click when they spot some red flags in emails, that's all.
- "Skilled employees in HR, legal, IT and risk departments spend an additional 276 hours a year helping to arrange and deliver in-house training"... Really? This type of employee costs about 80 bucks an hour, so that means $22,080 in costs. You can outsource your whole 2,000-user awareness training program to KnowBe4 for less than that.
- "Most businesses (90 percent) have used external consultants for over three days (27 hours) a year to review and advise on security policies and procedures." Now you are talking about real waste, That type of advice comes free, provided by your KnowBe4 Customer Success rep who helps you with your onboarding process as part of the service.
- "94 percent of CIOs have pushed for increased investment in user education following recent headlines around phishing and ransomware." For good reason! A recent Gartner analysis shows this is the #1 thing CIOs are pushing for. Why? All existing security layers are bypassed by social engineering and no software can protect against that, despite what Bromium's PR claims.
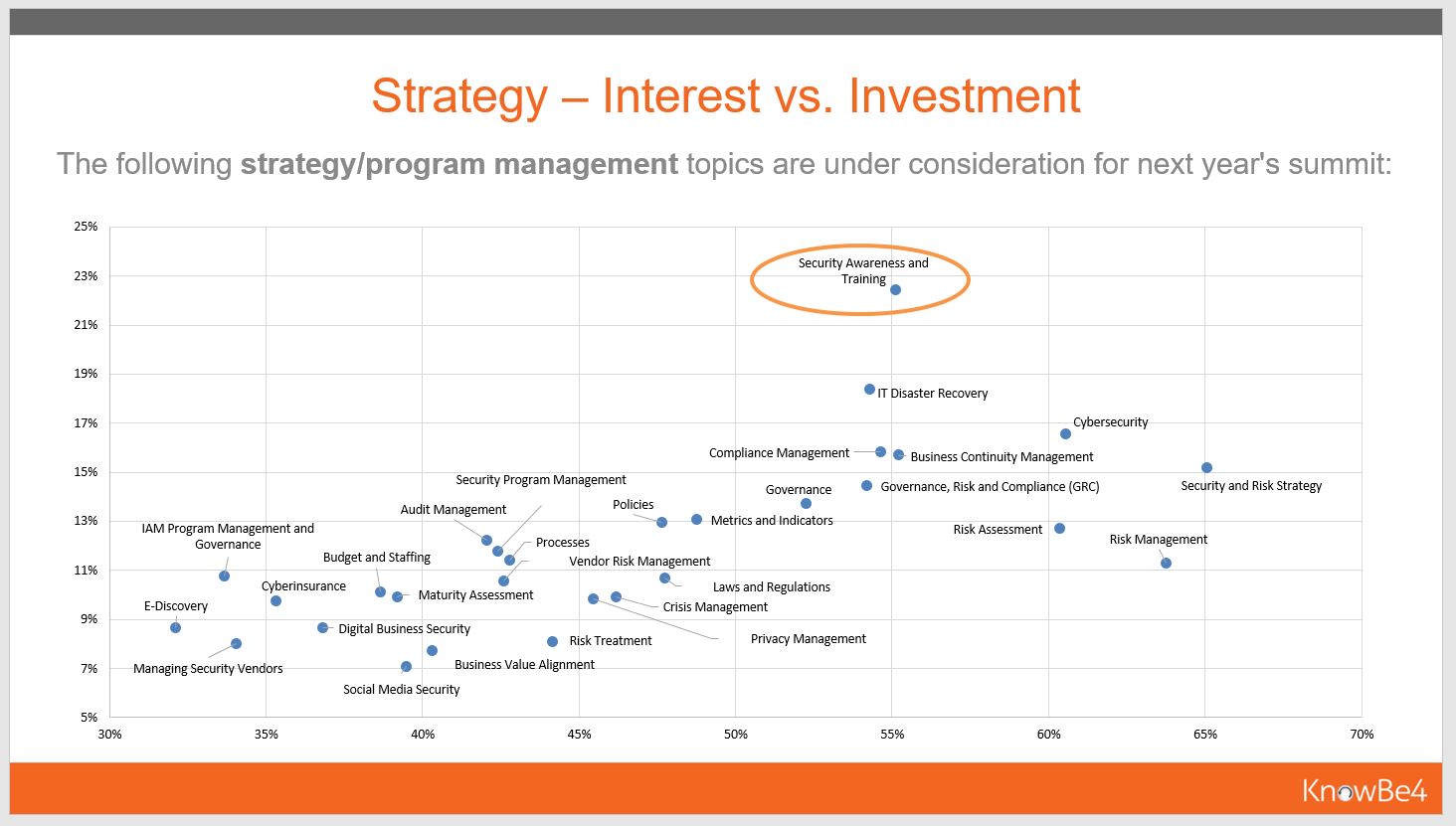
Here is a graph of what Gartner indicates are CIO and CSO strategy versus investment interests. You can also download this as a PPT file.
Simon Crosby, CTO for Bromium lent himself for this PR fluff and was quoted saying: “While end users are often the easiest target for hackers, the idea that they should be ‘the last line of defense’ for a business is simply ridiculous. The fact is, most employees are focused on getting their jobs done, and any training will go out the window if a deadline is looming,”
Our comment: That is exactly the attitude that has made social engineering so successful. It's the faulty fixed idea that you "cannot patch a stupid user". Well, guess what, with the right training... you can to a very large degree. Thousands of KnowBe4 customer show this year after year.
And then comes the most hair-raising statement of the release: “Insanity is doing the same thing over and over again and expecting different results, yet this is exactly what businesses are doing by piling time and money into education.”
With that statement, they just alienated 99% of the CIOs out there. Umm, aren't these the people you are selling to? Moreover, it implicitly assumes that training does not work. Nothing could be farther from the truth. KnowBe4 is growing so fast because our customers tell their friends in IT that it really works and is surprisingly affordable.
I'm not copying the whole release. You can have a good chuckle and read it here. They also explain who did the research and how they did their (faulty) math. Very entertaining.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
For instance, KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




