KnowBe4 has been warning against "CEO Fraud" emails for a few months now, the FBI also calls them "Business Email Compromise" (BEC). I had been hoping we would get one of these ourselves, and lo and behold, we received one of these phishing schemes ourselves last week. It was spoofed "from our CTO" Alin Irimie to our Financial Controller Alanna Cormier. Here is how it looked in gmail, after she clicked on Reply.
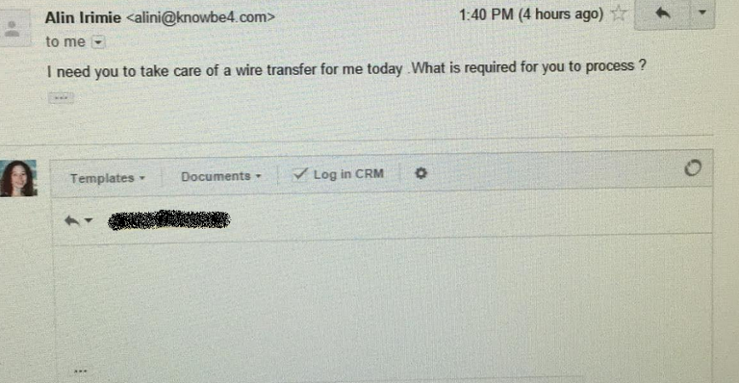
Since we send millions of simulated phishing to our 2,000 enterprise customers every year, we like to think we know what we are doing, so we decided to have some fun with these scammers.
The attacker must have only done some superficial research about us, because he did identify our CTO and our Controller. If he would have spent 2 minutes more, and looked at what we do, he might have changed his mind!
When we had a look at the headers it was clear that this was a clear attempt at wire fraud.
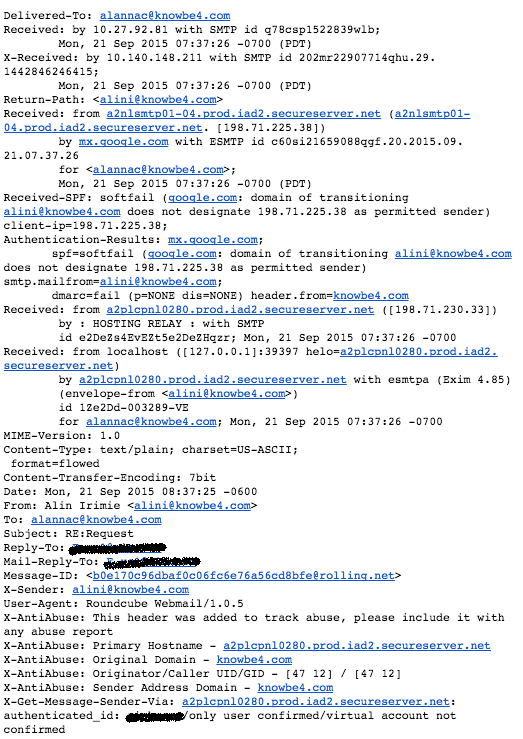
The headers seem to indicate that they signed up for a hosting account with Godaddy to get access to a mail delivery system and then hacked an open source web mail client (RoundCube), to easily spoof email headers.
They route the mail from their local RoundCube email client through Godaddy... and pick up the replied to emails on AOL. We asked our controller Alanna to reply back and to simply ask "how much and where to?" We got an immediate reply with bank wire information, which you see here:

The bank and the routing number are real, but the company, name and address are all false. We asked Alanna to send him another email with apologies she was late, and if "Alin" would be OK if we sent it a bit later. The hacker answered right away that was OK but it would be preferable if we could do it today. Yeah, sure.
We were very interested in knowing more, so we decided to phish back the scammer and send them an email that we thought they would fall for and get his IP address. This is how our PST Creation console looks. It's simple, has everything you need and nothing you don't.
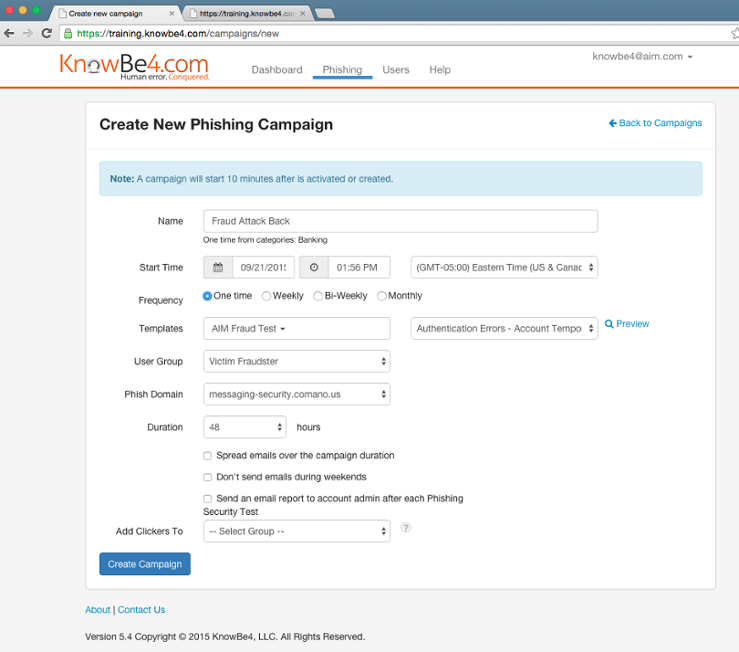
Since he was using AOL for his scam emails we thought it would be fun to phish him back with what you see below, it would certainly make him worried!
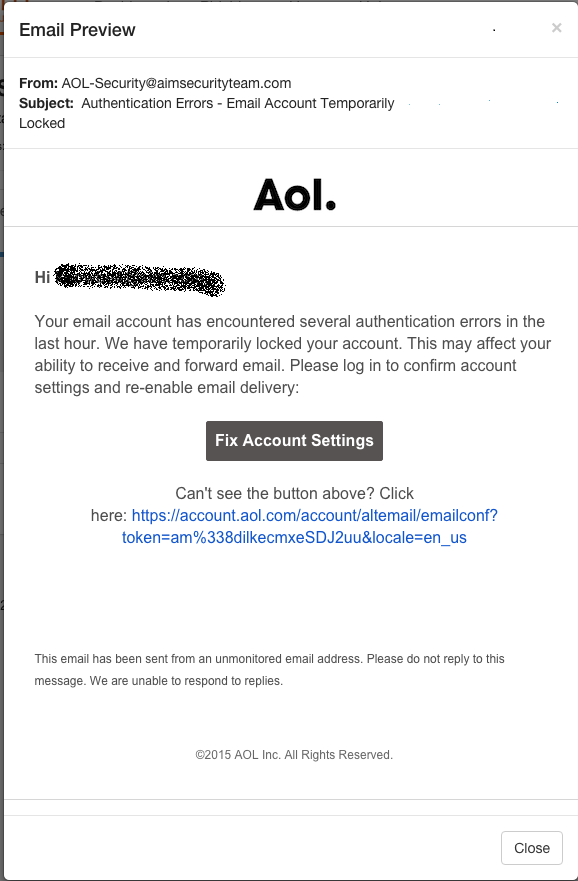
The landing page was scraped from AOL and this is where we dropped the criminal.

Well, the bad guy got scammed back!
He immediately logged in and that is how we obtained his IP address. Here is how our platform shows if someone clicks on a link or enters data:
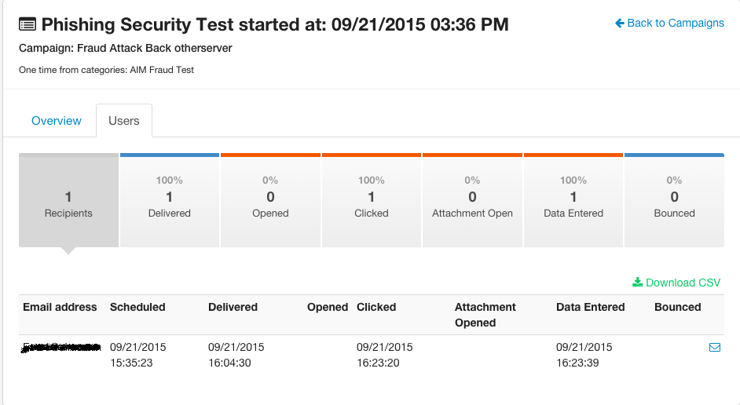
At this point we reported the scammer to the AOL security team and the FBI's Internet Crime Complaint Center (IC3).
The damage these cyber criminals do is astounding. The FBI has reported hundreds of millions of damage. About one third of people immediately spot the fraud, about one third is confused, ask a question and ultimately do not transfer, and about one third report back to the scammer and tell him that the transfer has been made. One fraudster can get up to 250,000 in fraudulent transfers done per month.
- The most advanced antivirus did not stop this attack.
- Firewalls did not stop this attack.
- Spam filters on the workstation and the email server did not stop this attack.
- Two-Factor authentication did not stop this attack.
- Intrusion Detection and/or Intrusion Prevention did not stop this attack.
- Secure Web Applications did not stop this attack.
- Encryption of data at rest and in flight did not stop this attack.
Alanna Cormier, Knowbe4's Financial Controller received Kevin Mitnick Security Awareness Training and stopped this attack.
You have to deploy defense-in-depth which has as its outer layer the very important points of Policy, Procedures & Awareness.
As you can see, it is extremely important to train employees against social engineering attacks like these, they are very costly when the hacker gets wire transfers out of the country. Effective security awareness training that combined interactive training and frequent simulated phishing attacks is a must these days. Find out how affordable this is today and be pleasantly surprised.





