A new version of the KillDisk disk-wiping malware has hit companies in the financial sector in Latin America, Trend Micro reported yesterday.
Just like previous versions, KillDisk purposely deleted files but included a ransom note in an attempt to fool victims that they've been infected with ransomware and not a malicious disk wiper known to be used in many past cyber-espionage operations.
KillDisk —from disk wiper to faux ransomware
On the infosec scene, KillDisk is one of the most infamous malware families around. The malware was developed and used primarily by a Russian cyber-espionage group known as Telebots.
This is the same group that created the Sandworm malware that attacked industrial equipment in the US, the BlackEnergy malware that was used in attacks against Ukraine's power grid, and the NotPetya ransomware that hit many companies in June 2017.
As with campaigns attributed to BlackEnergy group, the attackers are using spear-phishing emails with Microsoft Excel documents containing malicious macros as their main means of spreading infection.
KillDisk was initially developed as a disk-wiping malware that was deployed in the later stages of an infection so attackers could use it to hide their tracks by wiping disks and destroying forensic evidence.
This was KillDisk's main purpose when it was used together with the BlackEnergy malware during Telebots' attacks on the Ukrainian power grid in December 2015 and December 2016.
By the end of 2016, KillDisk received a facelift and started posing as ransomware in attacks against Ukrainian banks. A Linux variant was also discovered soon after, also used against the same targets.
New KillDisk attacks
Now, Trend Micro is reporting of new KillDisk attacks. The company says it detected a new version, but the changes are minimal from past attacks.
The ransom note is still there, as well as the disk-wiping functions. The only thing that's changed are the targets, with KillDisk being deployed on the networks of Latin American financial firms, far away from the previous Ukrainian targets where the malware was spotted for the past three years.
For the time being, Trend Micro did not say if these newer attacks were carried out by the TeleBots crew, or by some copycats trying to fool forensics investigators and throw investigators off their trail.
Few changes from previous versions
But just like in previous attacks, researchers also noted that KillDisk was not the primary malware deployed by intruders.
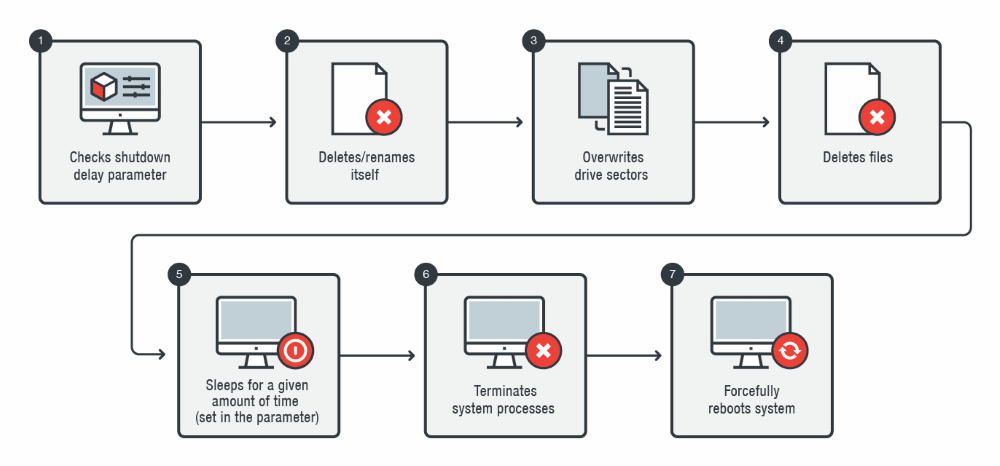
"This KillDisk variant looks like it is intentionally dropped by another process/attacker," researchers said. "Its file path is hardcoded in the malware (c:\windows\dimens.exe), which means that it is tightly coupled with its installer or is a part of a bigger package."
Researchers did not say what was the primary payload just yet. Nonetheless, they went into more details regarding the mode of operation of this particular KillDisk variant. There is more technical detail at Bleepingcomputer, the source of this story.
Free Ransomware Simulator Tool
How vulnerable is your network against a ransomware attack?
Bad guys are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 infection scenarios and show you if a workstation is vulnerable to infection.





