 Antivirus company Kaspersky has been monitoring ransomware pretty much from the get-go. Not surprising, as they are in Moscow and the main ransomware malware developers are Russian as well.
Antivirus company Kaspersky has been monitoring ransomware pretty much from the get-go. Not surprising, as they are in Moscow and the main ransomware malware developers are Russian as well.
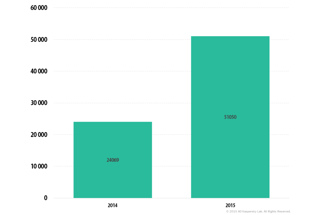
The amount of ransomware doubled from 2014 to 2015, they detected 24,000 infections in 2014, which went up to 50,000 infections the year after. According to Kaspersky, the real amount of infections is much higher, as their numbers are based on signatures and heuristics only. They also stated that there are two possible reasons that ransomware infections in organizations doubled.
- Attackers are able to extort more money from organizations as opposed to single individuals
- Organizations have a higher rate of payment, because the infections may have hit servers which causes very expensive downtime, with whole departments sitting on their hands.
They said: "One of the most interesting developments of 2015 in this realm has been the emergence of the first Linux encryption malware (Kaspersky Lab products detect it as the verdict ‘Trojan-Ransom.Linux.Cryptor’), which targets websites, including online stores. The cybercriminals exploited vulnerabilities in web applications to gain access to websites, and then uploaded a malicious program to the sites that encrypted the server data. In the majority of cases, this brought the site down. The cybercriminals demanded a ransom of one bitcoin to restore the site. Around 2,000 websites are estimated to have been infected. Given the popularity of *nix servers in the business environment, it is reasonable to assume that next year there may be more ransomware attacks against non-Windows platforms."
It is not hard to extrapolate that ransomware infections will again double in 2016.
The four ransomware infection vectors sorted by frequency:
- Phishing email with infected attachment
- Phishing email with malicious URL
- User clicks on infected ad
- User visits infected website
By far the most used vector at the moment is phishing emails that have a zipped attachment that claims to be the resume of a girl. Open it up and unzip it, and a page opens up with a link to another zipped file which contains the payload. This tactic bypasses all antivirus engines and relies on social engineering your end user.
What To Do About It
Obviously things like having recent backups, excellent patching discipline and good filters at the network edge are a given. IBM recently suggested the following mitigation actions: "Organizations will remain only as strong as their weakest link. Proactive end-user education and security awareness training continue to be critical in helping prevent incidents like the one described in this advisory.
- Train employees on security best practices and how to report suspicious activity.
- Consider conducting periodic mock-phishing exercises where employees receive emails or attachments that simulate malicious behavior. Metrics can be captured on how many potential incidents would have happened had the exercise been a real attack. Use these findings as a way to discuss the growing security threats with employees.
- Offer security training to employees to help understand threats and measures they can take to protect the organization.
- Provide regular reminders to employees on phishing and spam campaigns and that they shouldn’t open suspicious attachments or links from both work and personal emails.
- Train employees in charge of corporate banking to never provide banking credentials to anyone. The banks will never ask for this information.
We could not agree more. New school security awareness training which combines web-based on-demand training by a social engineering expert, combined with frequent simulated phishing attacks is a must these days to protect your organization against these kinds of attacks. Find out how affordable this is today:





