A recent Ivanti report shows cybersecurity practitioners getting more focused on the threat landscape, but defenders may need to hone their attention to focus on the right threats.
Ivanti just released their State of Cybersecurity Preparedness Series – 2023 report. It is one of the better cybersecurity reports. They surveyed over 6500 cybersecurity professionals and office workers in October 2022, so it’s a pretty big sample size as far as cybersecurity reports go. All their conclusions seem spot on, including the biggest predicted threats in 2023 (shown here from their report):
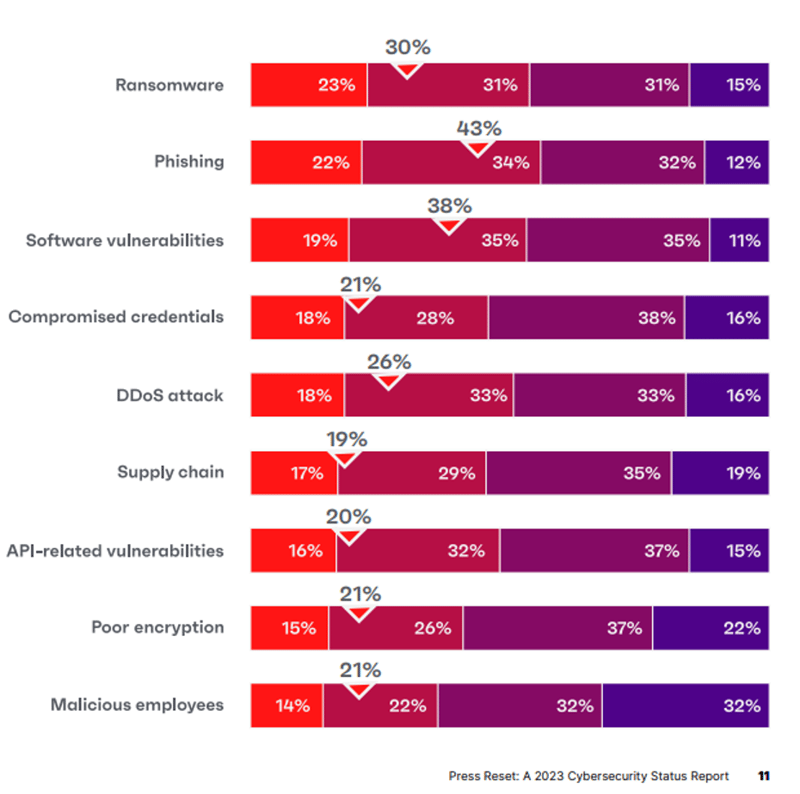
I think it is safe to say that cybersecurity practitioners are very worried about all those topics led by:
- Ransomware
- Phishing
- Unpatched software
- Compromised Credentials
Anyone who has been in cybersecurity for any length of time knows these issues are the top issues of our time. There are plenty of ways an organization can be compromised and Ivanti lists more, but these four threats worry responders more than any other.
Separating Attacks and Outcomes
However, both ransomware and compromised credentials are outcomes of attacks, not attack methods. This report, like many, many other cybersecurity reports, mixes up the root causes of attacks with the outcomes from various attack methods.
For example, how does most ransomware get inside a victim’s environment? Most often from social engineering and unpatched software. How are a users’ passwords compromised? Usually phishing. Ransomware and stolen credentials are outcomes of different attack methods. If I want to stop ransomware and stolen credentials, I could do no better than to mitigate social engineering and unpatched software. And the bonus from better doing those two things is that it stops the vast majority of attacks from hackers and malware, not just ransomware and social engineering.
Ivanti’s report admits as much, writing: “When comparing actual attacks companies have experienced, phishing and software vulnerabilities outpace other risks by multiples."
If you’re a defender, it’s very important to focus more on mitigating root causes over and above outcomes although a lot of space is devoted to discussing the latter while neglecting the former. Here’s why you shouldn’t fall into the same trap.
If you want to stop someone from breaking into your house repeatedly, you need to figure out how criminals could or are breaking into your house and then strengthen your house’s defenses to stop the break-ins. It is very important when deciding where to spend your housing defense dollars to figure out how most criminals could and would break into your house. There are lots of ways to break into houses including through the: doors, windows, walls, garages, roofs, basements, chimneys, etc.
The key to being an efficient defender is figuring out how most criminals break into houses (i.e., usually doors and windows) and making sure those items are secured best and first. Spending your money on fixing a possible criminal entryway that is rarely used by criminals before focusing on the more likely to-be-used entry points is essentially wasting money and increasing your personal risk. Similar concept with computer security.
To best and most efficiently stop hacking and malware you need to mitigate the initial root exploit methods that allow them to exploit devices and networks. Here are the 13 initial root cause exploits that allow hackers and malware into devices and environments:
- Social Engineering
- Programming Bug (patch available or not available)
- Authentication Attack
- Malicious Instructions/Scripting
- Human Error/Misconfiguration
- Eavesdropping/MitM
- Side Channel/Information Leak
- Brute Force/Computational
- Data Malformation
- Network Traffic Malformation
- Insider Attack
- 3rd Party Reliance Issue (supply chain/vendor/partner/etc.)
- Physical Attack
There are no hacker or malware attacks that haven’t used one of these methods to break in and gain initial foothold access. These are the primary root causes that defenders must focus on in order to most efficiently reduce cybersecurity risk. Don’t confuse attack methods with outcomes.
Step one of any data-driven defense plan is to figure out all the possible ways hackers and malware could break into your device or environment. That list is directly above. Step two is to figure out which of those initial root access attack methods are more likely to be used by hackers and malware than others.
The first two are easy: social engineering and unpatched software. Social engineering and unpatched software have been the top two most used methods for hacking and malware since the beginning of computers. They will likely be the top two initial root access methods for hackers and malware for decades to come. Although unpatched software was sometimes the most popular attack method for hackers and malware in the 1990’s and early 2000’s, social engineering was used from the very beginnings of computers and has been the number one attack method since the mid- to late-2000’s. Then vendors started including auto-patching functionality with every program they released.
Since then, social engineering has been the number one hacker and malware attack method by far, with many resources saying social engineering is involved in over 90% of all successful data breaches. Here are some related links:
- 70% to 90% of All Malicious Breaches are Due to Social Engineering and Phishing Attacks
- Cyber Security Breaches Survey 2022
- Phishing Attacks Increase by 54% as Initial Attack Vector for Access and Extortion Attacks
- 2022 Global State of Security Report
- Q1 2022 Threat Landscape: Threat Actors Target Email for Access and Extortion
- Why Phishing Is Still the Top Attack Method
- X-Force 2022 Insights: An Expanding OT Threat Landscape
Social engineering is even the top reason why ransomware is successful.
Ivant’s report says, “More than 1 in 3 leaders— people like CEOs, VPs and directors—have fallen victim to phishing scams.”
It is OK to focus on mitigating every cybersecurity threat as long as you do your first and best job at mitigating the top threats, which at this time is social engineering and unpatched software.
Most organizations are doing the best job they can using policies and technical defenses. Where most organizations could improve is by doing aggressive security awareness training. This means educating employees and co-workers about the biggest threats they face and how to handle and report them, at least once a month. That training should include simulated phishing test to determine who needs more training or less training to keep the organization as safe as is practical.
The average organization only does employee training once a year, often only to comply with various regulations. That’s not enough. Our data shows that training once a year has almost no effect on an organization’s cybersecurity risk. Risk doesn’t start to come down significantly until training and simulated phishing happens at least once a quarter and the real risk reduction benefits don’t happen until the cadence is monthly.
Ivant’s latest report rightly shows concern from phishing threats. Just make sure to approach it rigorously and give it attention it deserves. Your company’s cyber safety depends on it.
 The ModStore Preview includes:
The ModStore Preview includes:




