 New data shows just how frequently remote users are accessing risky web content that would normally be blocked by firewalls and other network monitoring solutions.
New data shows just how frequently remote users are accessing risky web content that would normally be blocked by firewalls and other network monitoring solutions.
You still have some material portion of your workforce working remotely (or you wouldn’t be reading this article). And, it’s probably a safe guess that you propped them up to work from home rather quickly, without truly getting around to the part where you secure their home working environment as strongly as it would be if they worked at the office, right?
You’re not alone – but that doesn’t really make it any better; if your remote employees are unprotected, your organization and its data are at risk. So, just how much should you be concerned about remote cybersecurity now that your workforce seems to be productive?
New data from perimeter security vendor NetMotion shows just how exposed remote employees are to potentially malicious web content. According to the report, remote employees:
- Encounter 8 potentially malicious URLs daily
- Visit 1 malware site daily and 1 phishing domain every 3 days
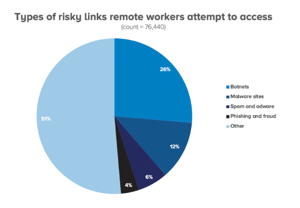
- 26% of risky sites visited were related to botnets
In addition, the volume of attempted clicks on potentially malicious URLs has increased 50% between the middle of the pandemic (mid-May to mid-June) and January of this year.
According to NetMotion, the lack of preventative and protective security in place is likely to blame. With 65% of organizations allowing employees to access managed applications from personal devices, this is a volatile combination.
Organizations need both a layered security strategy in place, and user enrollment in continual Security Awareness Training. When it comes right down to it, users are choosing to click these risky URLs. Proper education on social engineering attacks, phishing tactics, and more that commonly are used to trick users can make the difference between a user unknowingly falling for a scam and one that easily spots the questionable, suspicious, or malicious web content.
 Here's how it's done:
Here's how it's done:




