By Eric Howes, KnowBe4 Principal Lab Researcher. Not content just to make tax season even more miserable than it already is, malicious actors are increasingly maneuvering to capitalize on benefits election/enrollment season as well.
The bad guys are still learning, though. That means the benefits-themed phishing emails we've seen are not nearly as polished and convincing as malicious tax-themed phishing emails have become in recent years.
That said, you and your users need to be aware of the benefits enrollment phishes that have been reported to us by customers using the Phish Alert Button (PAB) over the past several weeks, most of which are front doors to credentials phishes.
The Bad
One of the more prevalent benefits-themed phishing emails we've encountered is very short -- one line short, in fact.
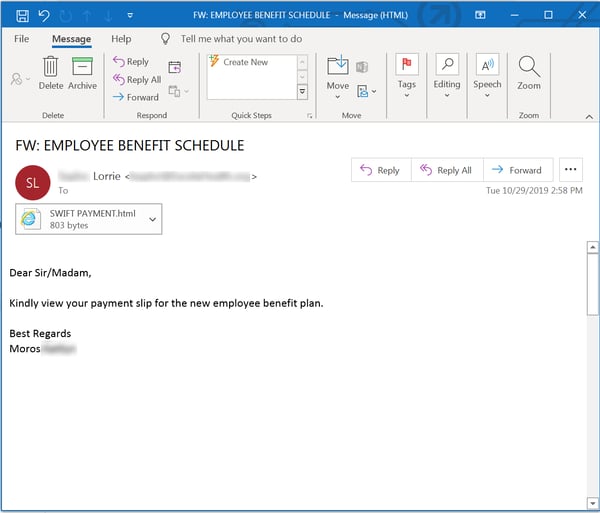
The other phish we've had reported in good numbers is a bit more expansive, stretching out to three short paragraphs.
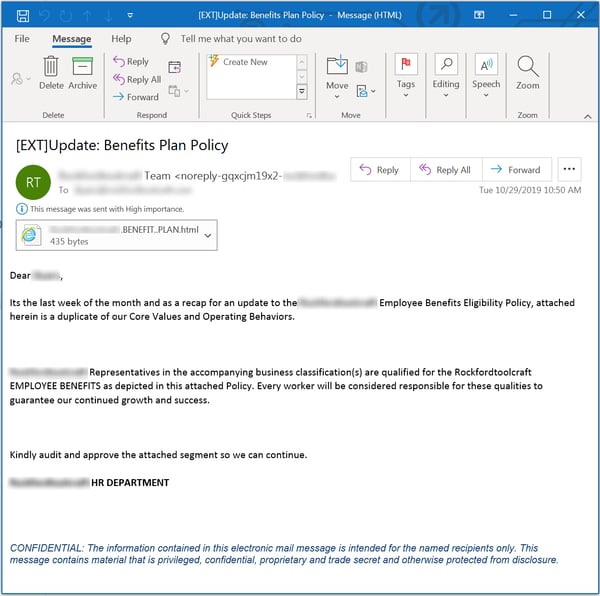
Neither is especially impressive or convincing. And if these emails strike you as vaguely familiar, you're not mistaken to think so. In fact, both are rather thin retreads of earlier phishing emails that have been making the rounds for the better part of a year. And neither of them started their digital lives as benefits enrollment phishes.
What these two wayward phishes tell us, however, is that the bad guys are focused on exploiting the benefits enrollment season -- which has become a thing in the United States over the past 5-10 years -- even if they don't fully understand it or have a well-designed plan to leverage it for the purposes of fraud.
The (Semi) Good
Another pair of phishing emails, though not nearly as prevalent as the two just above, are a bit more polished, if only for the reason that they seem more carefully designed to hue to the spirit of the "season."
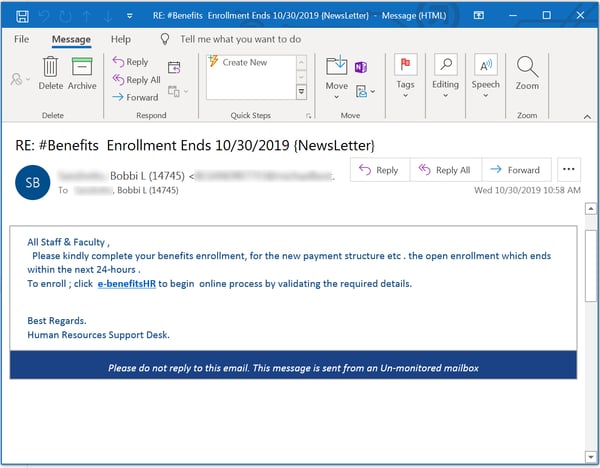
The first one straightforwardly prods users to click a malicious link after warning that the enrollment process closes within 24 hours.
The second is a bit more polished, leading off with the kind of bland corporate language users will have come to expect from this kind of email. It even gives users a preview of what's involved in the enrollment or elections process.
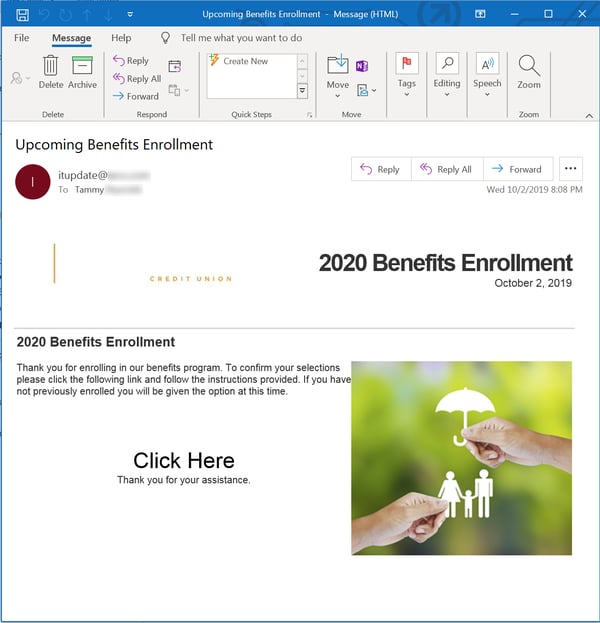
Of course, some users may be left wondering why this email hails from the IT department and not HR. Give the bad guys time, though. They will get these little kinks worked out.
The Creative
The fifth benefits-themed phishing email we've seen lately takes a different angle, though. One thing we know the bad guys have picked up on over the years is the mania for employee surveys among U.S.-based companies. So, why not a benefits survey?
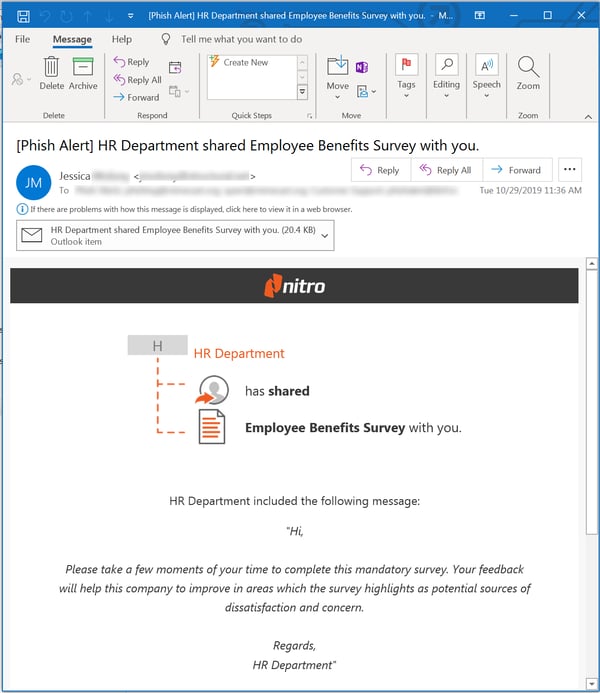
Your users undoubtedly have some definite opinions about your organization's benefits package. This malicious email gives them an opportunity to share those opinions -- by simply opening a malicious attachment.
Conclusion
As we have noted numerous times in this space, the bad guys are always learning. And we expect the benefits enrollment phishes your users might encounter will be getting more polished, more sophisticated, and much more dangerous. (And wait until they figure out there are Health Savings Accounts that can be plundered.)
One thing we anticipate the bad guys will do is spoof this email, which is a legitimate email inviting recipients to enroll in an ACA (aka "Obamacare") health plan.
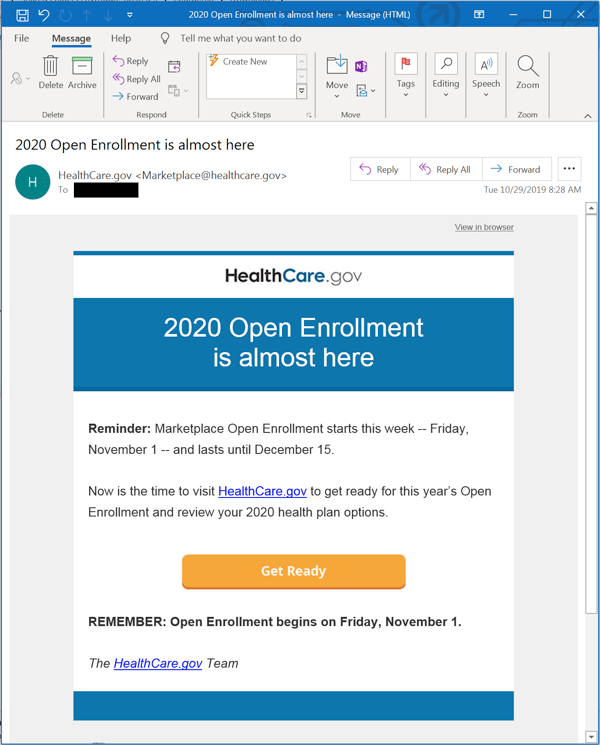
Although this email uses a URL shortener for the money link, it does actually take users to HealthCare.gov (the official ACA web site). That minor detail, of course, can be "fixed" by malicious actors looking to re-purpose this email.
Most of your employees care a great about their benefits packages. Make sure they're signing up for one of your own organization's health care plans and not one of bad guys' schemes to blow past the organization's last line of defense.
 Here's how it works:
Here's how it works:




