 By Laura DiDio
By Laura DiDio
There is no such thing as a 100% fully secure environment. And there never will be.
Security is not static; it is an ongoing work in progress. Organizations must be ever-vigilant and assume responsibility for their system and network security.
The ongoing and increasingly pernicious spate of cyber attacks – Ransomware, DDoS, Phishing, Bots, Trojans and targeted corporate espionage and malware, all underscore the need for heightened security and security awareness training.
Corporations, C-level executives, IT and security administrators and end users need to be aware of, proactively identify and thwart the innumerable potential existing security risks.
An overwhelming 80% majority of survey participants indicated that the “carelessness of end users” poses the biggest threat to organizational security. This far outpaces the 57% who cited malware infections as the largest potential security problem
In the Digital Age of cloud computing, the Internet of Things (IoT), mobility and Bring Your Own Device (BYOD) threats are everywhere. The attack vector is potentially limitless. It encompasses the Network Edge/Perimeter, the data center, applications, data transmission and networking mechanisms along with every piece of company owned equipment and end user-owned devices. IT departments are hard pressed to keep pace with career-hackers and ever-more efficient and deadly targeted cyber hacks.
Companies from SMBs with one to 100 users, to the largest multinational institutions with over 100,000 employees must recognize and repel future threats before they can inflict damage that results in lost revenue, lost or stolen data and raises the company’s risk of litigation.
In order for organizations to be cognizant of the myriad security threats and safeguard their data, they must implement the appropriate security measures and devote the necessary time, money and resources to provide their end users and the appropriate IT administrators and security professionals with adequate Security Awareness Training.
It is imperative that companies and their IT departments take a proactive approach to securing and safeguarding their corporate data and assets.
Security is a 50-50 proposition between technology and the human element which involves implementing strong, effective computing security policies.
In Part One of a two-part article, we outline the Top 10 business and procedural must-do steps organizations should take to safeguard all aspects of the corporate ecosystem and mitigate risk. Part Two, which will appear in the next issue of CyberheistNews will detail the Top 10 list of technology safeguards businesses should install to protect their data assets.
Top 10 Business Steps to Defend Against Cyber Security Threats
1. Good Housekeeping: Take Inventory. Know what people, devices and applications are on your network. That includes the various versions of software your users have installed on their myriad desktops, notebooks, tablets and smart phones.
Twenty-five years ago in the early 1990s, Before the Internet (BI) businesses used to brag about the longevity and reliability of their servers and network operating systems. It was considered a badge of honor if an IT administrator discovered a forgotten Novell Netware 3.x or 4.x server running in a closet that hadn’t been rebooted in nine or 10 years.
Nowadays, ignorance is not bliss. Today, ignorance, forgetfulness and sloppiness, along with a host of overlooked configuration errors that unwittingly give opportunistic hackers carte blanche to exploit your network could disaster and leave corporation’s data assets unprotected.
It’s important to compile a list of all devices, applications, transmission mechanism and access levels for all network users (from the CEO down to office temps). Retire old and outmoded equipment or retrofit it with the latest security mechanisms.
Organizations should take inventory at least every six months and preferably on a quarterly basis. Additionally, corporations that have acquired another firm via a merger or acquisition should do a complete and thorough inventory of the acquired entity’s infrastructure before connecting it to their own. This will require close cooperation and collaboration with the acquired company’s IT department, engineers and software developers.
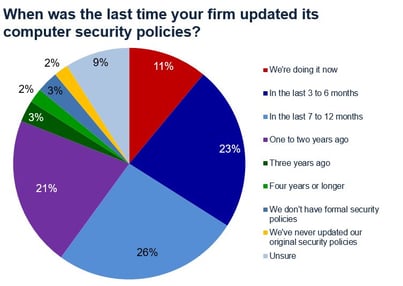 2. Regularly Review and Update Computer Security Policies. As the saying goes: “The best defense is a good offense.” The business case should always precede and drive the technological aspects of computer security. Organizations should construct and/or update existing security policies and procedures involving all aspects of the business.
2. Regularly Review and Update Computer Security Policies. As the saying goes: “The best defense is a good offense.” The business case should always precede and drive the technological aspects of computer security. Organizations should construct and/or update existing security policies and procedures involving all aspects of the business.
Security policies and procedures should reflect the current business climate and incorporate clear guidelines that reflect the latest cyber threats. The organization’s security policies should have a clear list of “Dos and Don’ts.” It should be disseminated by Human Resources to all employees via hard copy and Email. And it should also be incorporated into the onboarding training process for new employees. Businesses should treat Cyber Security with the same seriousness as they do with issues of discrimination and sexual harassment.
3. Educate All Users On Security Policies and Procedures. Everyone in the organization from the chief executive, to the IT department, application developers, knowledge workers, contract workers and office temps must be educated and adhere to the company’s computer and cyber security policies and procedures. Additionally, the IT department should regularly inform users about the latest threats via Email and hard copy.
 4. Enforce Computer/Cyber Security Policies and Procedures. No exceptions. Make it clear that the corporate cyber security rules are not made to be broken. The organization should construct a clear, concise list of the penalties associated with various infractions. These should include a sliding scale of actions the corporation may take for first, second and third infractions. Failure to comply with the corporation’s cyber security policies may involve myriad actions ranging from a warning to termination and even criminal prosecution.
4. Enforce Computer/Cyber Security Policies and Procedures. No exceptions. Make it clear that the corporate cyber security rules are not made to be broken. The organization should construct a clear, concise list of the penalties associated with various infractions. These should include a sliding scale of actions the corporation may take for first, second and third infractions. Failure to comply with the corporation’s cyber security policies may involve myriad actions ranging from a warning to termination and even criminal prosecution.
5. Construct a Cyber Security-specific Operational Level Agreement/ Response Plan. Every organization irrespective of size or vertical market should have a detailed OLA plan in place to quickly and efficiently respond to cyber attacks and cyber heists. For anyone not familiar with an OLA, it is a set of detailed policies and procedures that governs how the company’s internal stakeholders – Chief Security Officer (CISO), Chief Technology Officer (CTO), Director or VP of IT, administrators and security professionals will work together to respond to issues.
Having an OLA policy in place to respond to any security issues is crucial. The OLA agreement will detail the policies and procedures for dealing with hacks to minimize downtime, data loss and theft. Quick response to a security issue may mean the difference between thwarting a hack and suffering the consequence.
The Cyber Security OLA should establish and define the organizational chain of command; assign specific duties and responsibilities in the event of an attack, outline daily security operations and provide detailed instructions on how all the various internal stakeholders will work synergistically to respond to security issues. It should also incorporate a list of all outside third party vendors and service providers and a list of contacts at those organizations.
6. Security should be built-in. In today’s Digital Age, security cannot be practiced with 20/20 hindsight. It is the company’s responsibility to perform due diligence and work in concert with its vendors, resellers, third party ISVs and professional service providers to ensure that all new (IoT) devices and applications incorporate the latest security mechanisms. Before provisioning or deploying any device or application, the company should take great pains to ensure that they are secure by design, secure by default, secure in usage, secure in transmission and secure at rest (storage).
7. Budget Appropriately. There’s a lot of competition among the various corporate upgrade projects and individual departments to get their slice of the organization’s capital expenditure (Capex) and ongoing operational expenditure (Opex) budget. Oftentimes, security gets short shrift and loses out to other projects and stakeholders. This is especially true if the company has not yet been hit with a cyber attack or cyberheist.
The old sentiment of: “If it ain’t broke, don’t fix it,” does not apply to cyber security and in fact it could lead to disaster. We get it. Companies do not have unlimited funds. That said, there is no more important issue than security. Once again, organizations should perform due diligence involving all pertinent parties to determine a timetable and construct a budget for hiring skilled security IT staff; getting security awareness training for existing staff; hiring outside third parties to perform vulnerability testing and risk mitigation; purchasing new security software, equipment or upgrading existing devices.
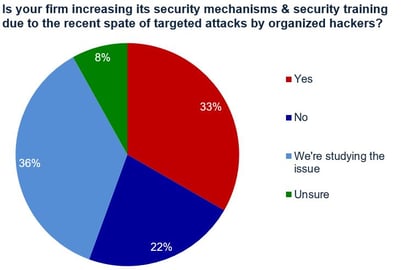
8. Deploy Security Awareness Training from the Board Room Down to the Mail Room. ITIC’s most recent Security survey found that over 40% of 600 responding organizations could not identify the type, length or severity of the cyber attacks their firms had experienced. Additionally, 11% of respondents said they were “Unsure” if their companies had suffered a hack over the last 12 months. There’s hardly a week that goes by without another new major cyber attack, Ransomware, Denial of Service, malware or other security related issue making the news. Overworked and frequently under-staffed IT and security administrators are hard pressed to keep pace with the increase in security threats. It is crucial to create a security culture that helps IT protect the network.
9. Stay Current on the latest Security Patches and Fixes. This may seem obvious but its importance cannot be overstated. The recent WannaCry pandemic is an excellent example why this is so important. Too often, companies get complacent and fail to stay abreast of the latest patches and fixes. This is a big mistake.
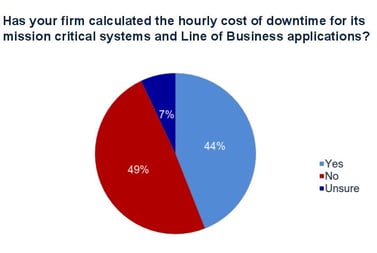
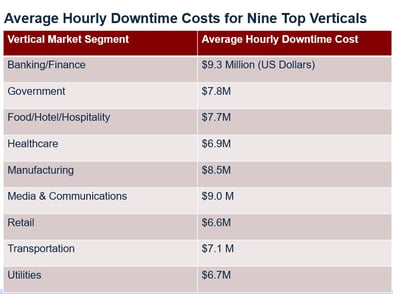 10. Calculate the Cost of Downtime Related to Cyber Attacks and Hacks. There is no better wake-up call than for the organization to calculate the monetary costs and business consequences as a result of a cyber attack. These include but are not limited to: downtime, lost, stolen, damaged/destroyed or altered data; the cost and amount of time it takes for IT perform remediation; the monetary cost of potential litigation, civil and criminal penalties; damage to the company’s reputation and brand and potential lost business as a result of the security breach or cyber heist.
10. Calculate the Cost of Downtime Related to Cyber Attacks and Hacks. There is no better wake-up call than for the organization to calculate the monetary costs and business consequences as a result of a cyber attack. These include but are not limited to: downtime, lost, stolen, damaged/destroyed or altered data; the cost and amount of time it takes for IT perform remediation; the monetary cost of potential litigation, civil and criminal penalties; damage to the company’s reputation and brand and potential lost business as a result of the security breach or cyber heist.
Ultimately the organization, the IT department and all of the end users must communicate, collaborate, cooperate and work in concert to defend their data assets.
Here is a slide deck with (PDF) the reliability and downtime costs survey - excellent ammo for IT security budget requests.
Laura DiDio is Principal of ITIC, a research and consulting firm based in the Boston area.




