Executive boards need better cyber security training, given half of C-level execs fall victim to phishing attacks, according to research conducted by security firm AlienVault. The research found that 82 per cent of IT security professionals worry that their high-ranking executives are still vulnerable to phishing scams.
Despite such concerns only 45% provide cyber security training to all their employees including the executive board, while 20% do not conduct any training and instead tackle the fallout of such cyber attacks when they occur, and rely just on their existing filters to protect employees.
(Click image for larger version)
Javvad Malik, security advocate at AlienVault, stated: “The challenge that lies here is two-fold. Firstly, most phishing scams that target execs are well-crafted and researched. Similar-looking domains are registered and execs are carefully researched. Secondly, many execs have personal assistants who manage their day-to-day operations and who are often more susceptible to social engineering techniques.”
“As such, it is important to train all users within an organization as attackers will always try to strike at the weakest links, who may not even be internal employees. CEO fraud also routinely targets third party suppliers, partners and customers, so awareness should be spread to all associated parties.
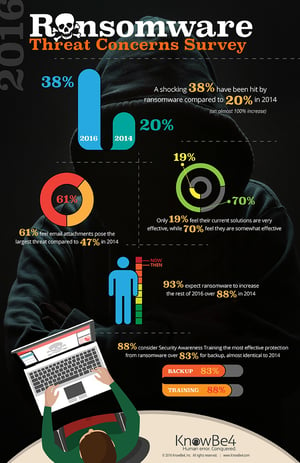
AlienVault’s research also found that 45 per cent of IT professionals thought it was likely their organization would pay the ransom demands if their network was infected by ransomware, often caused by a successful phishing attack. This is practically the same result as a recent KnowBe4 study which showed when confronted with a scenario where backups have failed and weeks of work might be lost, 42% would begin with paying the $500 ransom and hope for the best.

“It’s worrying to see how many people would consider paying up if they were infected with ransomware. Negotiating with criminals is a dangerous game that offers no guarantees, and cooperating in this way just encourages more attacks,” said Malik.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
For instance, KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser: