 We think of data breaches as taking days or weeks. But with elevated access to move laterally around the network, a cybercriminal can accomplish much in just a matter of minutes.
We think of data breaches as taking days or weeks. But with elevated access to move laterally around the network, a cybercriminal can accomplish much in just a matter of minutes.
According to some very detailed data in security vendor CrowdStrike’s 2019 Global Threat Report, The bad guys are getting really good at their craft. So much so, that the current record for going from initial endpoint compromise to “breakout” – CrowdStrikes measurement of attaining credentials and moving laterally within a network – is only a whopping 19 minutes. This was the average time attacks from the Russian Federation took. A distant second place is held by North Korea, coming in at 2 hours 20 minutes.
According to the report, initial attacks are 60% malware-based, and 40% malware-free (CrowdStrike considers when no files are written to disk, which includes direct memory injection and stolen credential attacks). Much of the breakout work is still done manually, with cybercriminals continuing to leverage native tools such as PowerShell, the command line, and WMI – which makes the 19-minute breakout time all the more impressive.
The report highlights attacks occurring across 19 different industries, making nearly every organization a target. With such sophistication and expertise demonstrated in the report, organizations need to understand the intensity and speed at which these attackers are moving – and how slowly organizations are able to detect and respond in kind.
Organizations need as strong a proactive defense as possible. This includes protecting the organizations logical perimeter – email and web, the endpoint with endpoint protection and AV, and leverage the user as the last line of defense by empowering them with Security Awareness Training.
Regardless of CrowdStrike's 60/40 split of malware-based to malware-less attacks, the majority of attacks still involved fooling the user into engaging a piece of malicious content. By continually education users with Security Awareness Training, the likelihood of success diminishes significantly.
Free Password Exposure Test
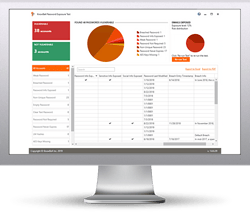 Verizon's recent Data Breach Report showed that 81% of hacking-related breaches used either stolen or weak passwords. And, a new survey from Dark Reading shows 44% of organizations say users pose the greatest threat to data security!
Verizon's recent Data Breach Report showed that 81% of hacking-related breaches used either stolen or weak passwords. And, a new survey from Dark Reading shows 44% of organizations say users pose the greatest threat to data security!
KnowBe4’s Password Exposure Test (PET) is a complimentary IT security tool that allows you to run an in-depth analysis of your organization’s hidden exposure risk associated with your users. Here's how it works:
- Checks to see if any of your organization's email addresses have been part of a data breach
- Tests against 10 types of weak password related threats associated with user accounts
- Checks against breached or weak passwords currently in use in your Active Directory
- Reports on the accounts affected and does not show/report on the actual passwords
- Just download the install, run it, get results in minutes!
Identify which users may be putting your organization at risk before the bad guys do.
Don't like to click on redirected links? Cut & Paste this link in your browser:





