 Using something as simple as an attachment with an Israel/Hamas-related filename seems to be all it takes for new social engineering attacks disguised as donation confirmations.
Using something as simple as an attachment with an Israel/Hamas-related filename seems to be all it takes for new social engineering attacks disguised as donation confirmations.
If you were to guess how many new attacks have been launched under the guise of the recent war, it’s probably more than you think. According to security researchers at CheckPoint Software, they’ve discovered over 15,000 examples of attacks using this theming.
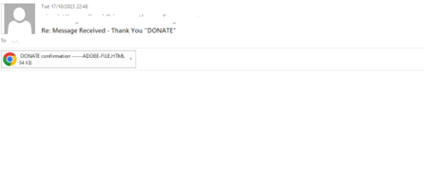
Take the example below:
Source: Avanan
While not the most sophisticated email, it’s the HTML attachment that is the clincher for this attack. According to CheckPoint, more than 50% of malicious attachments are HTML files.
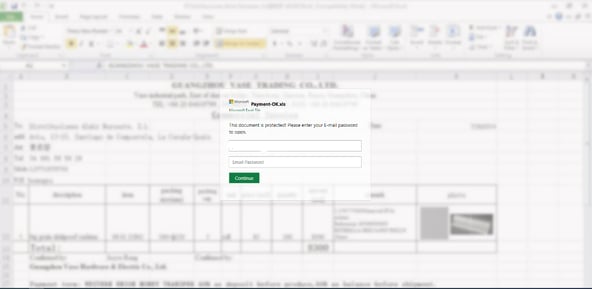
Opening the attachment reveals the following fake “locked” Excel document that requires the victim enter in their Microsoft 365 credentials:
Source: Avanan
The tactics used in this example are relatively unsophisticated and unimpressive to those that have been paying attention to the evolution of phishing attacks. But it goes to show that all it takes is a user that hasn’t yet undergone new-school security awareness training. Therefore, when your users aren’t vigilant when interacting with such attacks, they could fall for what appears to be one of the lamest modern phishing efforts I’ve seen.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




