 Is your organization’s password complexity strong enough?
Is your organization’s password complexity strong enough?
Bottom line: If you want to stop password hash cracking attacks, you need to have stronger passwords: longer and less predictable complexity.
Everyone knows you need a “strong” password to avoid successful password guessing and password hash cracking attacks. A strong password is a relative concept, but in general, means that a password is sufficiently long and/or complex enough to avoid most/all likely password guessing/cracking attacks against the systems where the password is used for the lifetime of the password or system. As password attacks evolve and improve, it takes stronger passwords to mitigate successful attacks. A password that was considered strong last year may not be considered strong this year.
Note: Many/most password attacks do not care about how strong your password is, including password social engineering, password theft, password resets, attacks against the underlying password storage database, etc.
Password guessing and password hash cracking are two different types of password attacks, and they require different password policy requirements to be mitigated. Password hash cracking requires stronger passwords to mitigate successful attacks. I will cover both now.
Password Guessing
Password guessing is when an adversary guesses at a victim’s password via an online/local login screen where the victim themselves could otherwise log in with their login name and password combination to authenticate to a program or system. The attacker can guess as many times as they like, manually or using an automated tool, but is limited by the online/local login screen invalid login mitigations, authentication processing speed and bandwidth. Common mitigations include password construction policies, account lockout policies, login attempt throttling, password expiration, checks for weak passwords, invalid login event monitoring and requiring multi-factor authentication.
If an authentication system has what we might call sufficient password attack mitigations (as mentioned above), it really does not take a very strong password to prevent successful password guessing. In practice, a normal complexity password (i.e., different capitalization required, numbers or symbols required, etc.) tend to be hard for an attacker to successfully guess at 10 characters, but we often recommend at least 12-character passwords to give some additional confidence, especially because users cannot be assured that all the systems where they authenticate will have “sufficient” password mitigations. It is very common for adversaries to find systems that do not have sufficient password mitigations and then even 10-character or longer passwords may become compromised.
So far the longest online, real-world attacker, password guessing compromise (without insider knowledge of the password’s possible construction) this author is aware of is a 10-character password, Welkom2020. It is possible that longer password guessing compromises have happened that I am not aware of and longer successes have probably been done many times by penetration testers.
Even in order for this 10-character password guessing compromise to happen, the defenders essentially had no mitigations deployed. The adversaries were able to guess at the password using an online portal accessible from the Internet over 100,000 times a day for over a year. Any login portal with almost any standard password guessing mitigation (i.e., account lockout, monitoring, etc.) enabled would have prevented this attack. But it is very common for adversaries to seek out login portals without sufficient password mitigation controls so they can guess as rapidly as allowed by the involved technologies. For example, in 2020, Akamai reported that 75% of password spray guessing attacks occurred against Application Programming Interfaces (APIs). APIs often allow or require logins and often do not have sufficient password guessing mitigations.
To summarize, a 10-character or longer password with standard complexity is usually understood to be sufficiently protective if involved only at authentication portals with standard password guessing attack mitigations. If you, as a user, cannot ensure that all involved login portals use sufficient password guessing mitigations, you need stronger (longer and/or more complex) passwords.
How strong does your password have to be to prevent password guessing attacks against login portals without sufficient password guessing mitigations? If your password is not perfectly random (like most human-creative passwords), then you need a stronger password. As indicated above, we do know that in a real-world attack, a 10-character, standard complexity password (i.e., Welkom2020) was successfully guessed, so most likely, you need more than a few characters longer than 10 characters. A 12-character PERFECTLY RANDOM password is thought to be impervious to all known password guessing or password hash cracking attacks.
Note: A sufficiently strong 8-character password is likely capable of preventing password guessing attacks on all login portals with strong password guessing controls, including detecting and preventing “password spray/stuffing” attacks, where an attacker does not guess at passwords faster than the underlying account lockout policy would allow without locking out the account.
Password Hash Cracking
Password hash cracking is where an attacker has somehow previously obtained a victim’s password hash (most passwords are usually stored in their cryptographic hash forms in today’s operating systems and many/most applications). When this occurs, the attacker can guess at the password’s hash using what is known as an offline password hash cracking attack (also commonly known as a rainbow table attack, although there are some differences) as fast as their hardware/software combination allows. This can be very fast.
How fast?
It is not unusual for a penetration tester or adversary to be able to conduct password hashing attacks at up to one trillion different guesses per second. How long would your password stand if the adversary could guess up to one trillion guesses per second? Some adversaries can guess at password hashes at tens of trillions of times a second and we think the most well-resourced nation states can guess at password hashes at rates approaching a hundred trillion guesses per second. Wow!
Note: Readers should not forget that getting a victim’s password hashes often means the adversary has already acquired top-level access to a victim’s device or network and it is already essentially “game over” for the victim(s). When an attacker has top-level access, there are thousands of malicious things they can do and cracking password hashes is just one attack problem to worry about. However, there are a few attacking techniques where an attacker without any prior access (e.g., man-the-middle-attacks) or only standard user access (e.g., Kerberoasting attacks), where an attacker can sometimes obtain a victim’s access without previous or elevated access. It is because these lesser or unprivileged attacks can obtain victim password hashes that not worrying about password hash attacks is not a reasonable defense.
Assuming an adversary has obtained a victim’s password hash, how long do most victim passwords last?
I think if we look over the whole world of passwords, most (i.e., 80% and above) would fall fairly quickly to any decent password hash cracking attack (let’s say over one trillion guesses per second). Certainly, any human-created password with 10-characters is falling very quickly. Professional password penetration testers routinely report being able to compromise 80% or more of typical user passwords within a few days to weeks of trying (even without trillion-per-second guessing capabilities).
A recent, real-world password hash cracking exercise involving multiple U.S. government agencies revealed that even in networks without required standard complexity (e.g., uppercase and lowercase and number or symbol required), 16% of user passwords fell in the first 90 minutes of cracking. Unfortunately, the report does not reveal their password hash cracking capabilities.
Note: Interesting side note on this U.S. government password (hash) cracking report is that if they did crack your password hash (21% of the total), over three-fourths (76%) were cracked in the first 90 minutes of trying. So, if your password did not fall almost immediately, odds were it would survive without being cracked during the test.
What is interesting to note is that “standard” password complexity (e.g., uppercase and lowercase and number or symbol required) is falling to most password hash cracking attacks. Most of the problem is that “standard” password complexity is not that difficult for adversaries to figure out. In most environments where standard password complexity is enabled, most users will pick a password length that matches (or barely exceeds) the minimum password size required, begin the password with an uppercase character, usually a consonant, followed by a lowercase character, usually a vowel (at least for native English-speakers), and if there are any numbers or symbols, they will be at the end of the password. Usually even the letters, numbers and symbols used are fairly predictable. Even though most users could pick from any of the 94-different keyboard symbols on their keyboard (for English-speakers), most users pick the same 17 characters. Most people do not use the space, q, z or numbers above 2.
For example, in the real-world report linked to above, the following “long and complex” passwords were successfully guessed at:
- Changeme$12345
- Polar_bear65
- Nationalparks2014!
Most other organizations conducting password hash cracking attacks will have similar results.
This is an important point! “Standard” password complexity is NOT going to stop most adversarial password hash cracking attacks. Your existing password complexity requirement might not be good enough. It might stop password guessing attacks, but not password hash cracking attacks. This is a hugely important. If you want to also stop password hash cracking attacks, you need to have stronger passwords: longer and less predictable complexity.
Either encourage users to choose less predictable complexity or somehow enforce it. Tell users to put:
- The capital letter somewhere else other than the beginning
- Use something else other than a lowercase vowel in the second position
- Put the numbers or symbols earlier on in the password
- Do not use years, especially at the end of passwords
- Do not use easily guessed at password “roots” like password, changeme, 123, 12345, qwerty, etc.
What is the best password policy? Do not use a password if you do not have to. Instead, use phishing-resistant multi-factor authentication. If you have to use passwords (and most of us do), use a password manager to create and use perfectly random passwords.
Research has shown that a 12-character PERFECTLY RANDOM password mitigates all known password guessing and cracking attacks even if the adversary has many tens of trillions of guesses per second (which is nearly impossible for adversaries to achieve in online guessing attacks anyway).
In this example exercise shown graphically below, a password hash (NT is the Microsoft Windows password hash default, SHA-2 is the default password hash for most Apple, Linux, and BSD systems) becomes very difficult for even a 45 trillion per second guessing password cracking solver at about 11 characters when using a PERFECTLY RANDOM password.
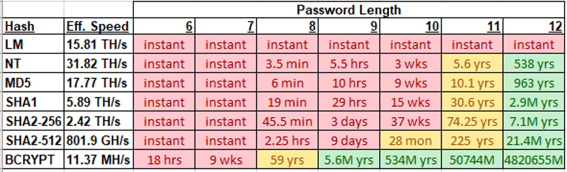
I recommend you use at least 12-character PERFECTLY RANDOM passwords to get extra assurance.
No one likes to create or use PERFECTLY RANDOM passwords, so use a password manager instead. Password managers can easily create and use 12-character and longer perfectly random passwords that protect you against both known password guessing and password hacking attacks.
If you want to create your own passwords out of your head and they contain the traditional, “standard” complexity, they likely need to be 20 characters or longer. I know of password penetration teams that routine (e.g., every day) crack 18-character, human-created passwords if they can obtain their hashes.
If you want more information about password managers and how to select one, consider watching my webinar here.
If you want to read more about why KnowBe4 and I recommend a particular password policy, feel free to read our ebook on the subject here.
You can read more about phishing-resistant MFA.
Password Attack Defense Summary
- Use phishing-resistant MFA when you can to protect valuable data and systems
- Use a password manager to create and use perfectly random passwords
- If humans create passwords, they need to be 20 characters or longer to defeat all known password guessing and cracking attacks
- Do not use commonly used password root words (e.g., password, changeme, 12345, qwerty, etc.)
- Do not put the only capitalized letter as the first character of your password
- Do not put a lowercase vowel as the second character of your password
- Do not only put numbers, symbols, or years, at the end of a password
- Change your password at least once a year
I hope this article has been helpful. Continue to fight the good fight!






