 This is a concerning new "sleeper" ransomware twist.
This is a concerning new "sleeper" ransomware twist.
It's called Locker and has been infecting employee's workstations but sat there silently until midnight May 25, 2015 when it woke up. Locker then started to wreak havoc in a massive way.
Since this strain literally stuck up its ugly head, Reddit has a topic on it with over 600 comments.
Bleepingcomputer has a support topic that is 14 pages long and they received 100s of emails from consultants all over the world. Based on their experience with cryptoware, they stated this strain has a large "installed" base, which does not bode much good. Topics related to this new strain are suddenly posted on all the major support boards, AV forums, etc.
It appears we have a new player in Ransomware City, and this looks like an 800 pound gorilla very similar to CryptoLocker. At the moment, it looks like the infection vector is exploit kits but there are rumors of a compromised MineCraft installer. Here is what it does:
- A series of Windows services are used to install Locker on the computer and encrypt data files.
- During the install process, Locker will check if the computer is virtual machine and terminate if detected.
- Encrypts data files with RSA encryption, and does not change the file extension.
- After the encryption it deletes your c:\ shadow volume copies and displays its ransom interface.
- If your backups failed and you are forced to pay the ransom, once payment has been confirmed the ransomware will download the private key and automatically decrypt your files.
The files that are encrypted are the following types: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf, and again, Locker does not change the file extension so your users will get error messages from their applications that the file is corrupted.
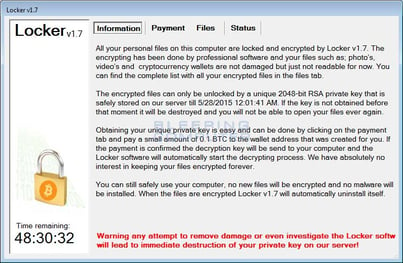
As you see on the screenshot, it has a scary message in red at the bottom of the screen stating: "Warning any attempt to remove damage or even investigate the Locker software will lead to immediate destruction of your private key on our server!" This is just to force you into paying, not something to be too worried about.
At this very early time after the initial discovery, things are still somewhat murky, but we will keep you in the loop about any developments.
UPDATE 1
According to the Bleeping Computer discussion thread started this Sunday, Locker ransomware silently ran on victim's computers until Monday at midnight, when it was activated. Then, the malware employed RSA encryption to lock users' files, and in turn requested 0.1 Bitcoin from victims so they could retrieve their data. Different attacks have displayed warning messages with varying versions of the ransomware, including Locker v1.7, v3.5.3, V2.16, and V5.52, but the version number “does not appear to have any significance,” an admin user on the forum said.
BREAKING NEWS -- UPDATE 2
Now this has never happened before! The author seems to have either made so much money that he's pulling out of this criminal campaign, or has gotten cold feet and is afraid to get caught either by law enforcement or damaged by a local cyber mafia. In either case, he claims the release was a mistake and has uploaded a CSV file with a dump of the encryption keys and states that automatic decryption of all affected computers will start on June 2nd. Here is his admission of guilt:
"I am the author of the Locker ransomware and I'm very sorry about that has happened. It was never my intention to release this. I uploaded the database to mega.co.nz containing "bitcoin address, public key, private key" as CSV. This is a dump of the complete database and most of the keys weren't even used. All distribution of new keys has been stopped."
Now, this seems pretty wishy-washy. If you build code like this, you know very well what you are doing. The fact it was built as a 'sleeper' shows months-long careful planning. The other point is that if he would really have genuine remorse, everyone would get refunded which does not seems to have happened. It is also not clear if current infection vectors have been turned off or not.
What we can assume is that he is a talented coder but not an experienced cyber criminal because a foul-up like this would never have happened with professional Eastern European organized cybercrime. He may have worked as a developer for one of these gangs and decided to start his own outfit which backfired. If you have infected machines, there is a chance you can find the decryption key in a database.
I am looking at the data, and this file does not seem to be malicious based on a brief virustotal analysis. It does contain a large quantity of RSA keys and Bitcoin addresses. Open at your own risk, until further analyses are performed.
BREAKING NEWS -- UPDATE 3
On May 30th, the Locker ransomware developer apologized for his "mistake" and released a list of the all private encryption keys for it's victims. With this release he also apologized for encrypting everyones files and promised to automatically decrypt all infected users on June 2nd.
True to their word, On June 2nd he issued a command to have the Locker ransomware automatically decrypt a victim's files for free. Unfortunately, in order for the decryption to take place, the victim would still have needed to be running the infection.
And as always, stepping employees through effective security awareness training is a must these days. Find out how affordable this is, and be pleasantly surprised.





