 Brian Krebs wrote: "The cybercriminals behind the GandCrab ransomware-as-a-service (RaaS) offering recently announced they were closing up shop and retiring after having allegedly earned more than $2 billion in extortion payments from victims.
Brian Krebs wrote: "The cybercriminals behind the GandCrab ransomware-as-a-service (RaaS) offering recently announced they were closing up shop and retiring after having allegedly earned more than $2 billion in extortion payments from victims. Krebs concluded and I agree with him: "My guess is the GandCrab team has not retired, and has simply regrouped and re-branded due to the significant amount of attention from security researchers and law enforcement investigators. It seems highly unlikely that such a successful group of cybercriminals would just walk away from such an insanely profitable enterprise."
Brand-New Ransomware Simulator Tool Now with Two New Ransomware Scenarios
The bad guys are continuing to evolve their approach to evading detection. That’s why we’ve updated our Ransomware Simulation tool “RanSim” to include two new ransomware scenarios! 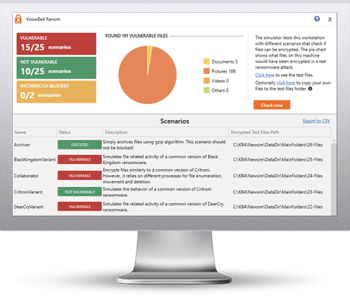
These new scenarios simulate ransomware strains like GandCrab and Rokku that encrypt users’ files and demands a crypto-ransom in exchange for the keys.
GandCrab was a very active ransomware strain all throughout 2018 as well as since the start of 2019, and it is known for requesting up to $3000 from its victims to decode encrypted files. While the creators of GandCrab announced in May they were shutting down their operation, make sure your organization is safe from this type of infection before another group takes it over, or worse, you won’t have an option to decrypt your system!
Try KnowBe4’s NEW Ransomware Simulator version and get a quick look at the effectiveness of your existing network protection against the latest threats. RanSim will simulate 15 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 16 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complimentary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Download the New RanSim Now:
https://www.knowbe4.com/ransomware-simulator




