 Georgia Tech researchers reported that hackers are using a technique identified with a newly coined term "combosquatting" to trick users into visiting malicious websites.
Georgia Tech researchers reported that hackers are using a technique identified with a newly coined term "combosquatting" to trick users into visiting malicious websites.
Sorry to break it to you guys, but this type of social engineering has been done for at least a decade. Perhaps the actual news is the scale and fully automated level it happens at today.
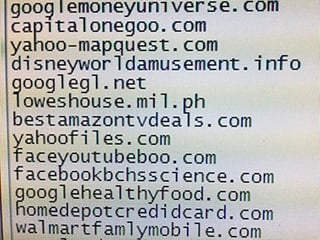
They reported that the attackers buy a domain name that sounds legitimate, but is not related to a trustworthy entity. The malicious domain usually involves a familiar name, such as a popular social networking site or a banking service, with a hyphenated word. Yup, so far nothing new.
For example, if the legitimate url is trademark.com, the malicious url will be trademark-security.com. The technique is similar to, but different from typosquatting, which uses a malicious url that users are likely to key in by mistake, such as trademrak.com.
The malicious website can then be used for credential harvesting, infect machines with botnet code or ransomware and a raft of other criminal mischief.
Millions of malicious domains are set up
The urls are distributed through spam campaigns, advertisements or show up in results of searches. According to a study presented at the 2017 ACM Conference on Computer and Communications Security by researchers from Georgia Tech, combosquatting is a growing attack strategy, with millions of malicious domains set up. The study is believed to be the first large scale scrutiny of combosquatting.
Panagiotis Kintis, first author of the study, says "We have seen combosquatting used in virtually every kind of cyberattack that we know of, from drive-by downloads to phishing attacks by nation-states. These attacks can even fool security people who may be looking at network traffic for malicious activity. When they see a familiar trademark, they may feel a false sense of comfort with it."
The study showed that the practice of combosquatting was more prevalent than the better known typosquatting. Some of the malicious domains identified by the researchers included websites that at one point were owned by legitimate entities, but were allowed to expire. Without an authority to pick up "garbage" domains, the urls are up for grabs to the malicious attackers.
Here is one suggestion
Check all the domains your organization owns, and set them on auto-renew so that you do not lose any of them to the bad guys.
I strongly suggest you get a quote for new-school security awareness training for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP. If you don't, the bad guys will, because your filters never catch all of it. Get a quote now and you will be pleasantly surprised.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO, KnowBe4, Inc






