 Scammers use an “overdue tax bill” along with a sophisticated and obfuscated javascript-based “invoice” attachment to identify targeted victims, validate credentials, and transmit them within seconds.
Scammers use an “overdue tax bill” along with a sophisticated and obfuscated javascript-based “invoice” attachment to identify targeted victims, validate credentials, and transmit them within seconds.
There’s a common theme that runs through just about every phishing scam that has come across my desk – in each case, there is always some element in the theming or communicated message that is designed to both get the attention of the recipient and turn that recipient into a victim by getting them to act in a desired way.
А new scam identified by the Resecurity HUNTER team shows how the simple claim made in an email to be from the Internal Revenue Service with the message that the recipient has monies owed that is overdue.
In the following scam email, you’ll notice the semi-believable “irs [at] service.govdelivery.com” email address, along with the request to view an attached HTML file “to view and pay the invoice”.
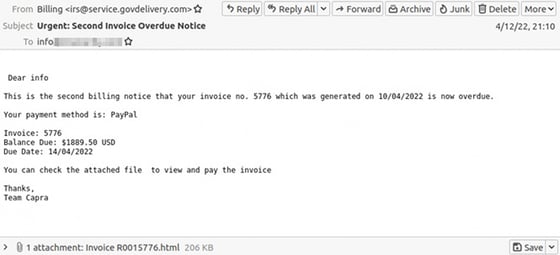
Diving into the attachment, Resecurity identify the HTML file containing obfuscated JavaScript code that does the following:
- Checks the victim’s location based on IP address to selectively target countries or regions
- Presents a spoofed Microsoft 365 logon screen
- If credentials are presented, checks the credentials validity by attempting to logon via IMAP to Microsoft 365
- Transmits the credentials back to a threat actor-controlled server
If you look again at the email initially sent, you can make a pretty easy case for Security Awareness Training; the signs there are obvious to a) someone who knows what to look for and b) someone who is actively on the lookout for malicious emails. This is the kind of employee continual Security Awareness Training will create.
 Here's how it works:
Here's how it works:




