A new phishing attack method shows that even the mighty two-factor authentication can be beaten without needing to possess a user’s mobile device.
We’d like to think that using Multi-Factor Authentication (MFA) surrounds the logon process with such a high level of security that it can’t be broken. But a recent phishing attack shows that simple mix of social engineering and quick backend hacking can successfully work around the most basic of MFA – two-factor, SMS one-time password (OTP) authentication.
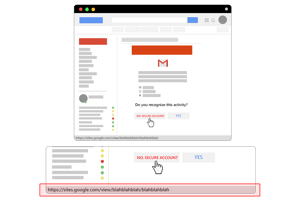
Researchers at Certfa Labs recently identified the attack scheme created by the cybercriminal group Charming Kitten who was responsible for the hacking of HBO back in 2017). The phishing attack uses the Google’s Site Service (which uses the subdomain sites.google.com) to establish credibility and to deceive their potential victims.
Users are initially phished with either fake notifications of unauthorized access, or via bogus file sharing on Google Drive. In either case, the focus is to have the victim thinking they need to interact with Google. Doing so makes the stretch to requiring authentication, and then requiring the second factor, pretty reasonable.
Pages made to look like both Google authentication, as well as emails designed to invoke the use of 2FA to validate the user (shown below) are used in a contextually timely fashion to trick users to believe they are interacting with Google’s 2FA.
The bad guys are getting better and craftier at their art every day. Attacks like these would fool even the savviest of users. What organizations need to fend off attacks like this is a security-minded user who is constantly on-guard – even when the systems they interact with seem legitimate.
Security Awareness Training would teach users about the potential red flags that exist even in this very slick campaign – The initial phish involves files on a Google Drive, or a notification of improper access. It’s at this point that users should be scrutinizing the emails, questioning their legitimacy. Did they request a file from the sender? Does the access notification from Google look completely legitimate? Having a default mindset of asking questions when anything out of the ordinary comes in is one of the byproducts of users who continually go through Security Awareness Training.
 Here's how MASA works:
Here's how MASA works:




