Threat researchers at Intezer have discovered a new string of attacks using an updated TONEDEAF toolset intent on eventually gaining access to U.S. Government research.
Employees and customers of U.S.-based research company Westat (a company that provides research to the U.S. Government) have been receiving satisfaction survey emails that include an Excel spreadsheet.
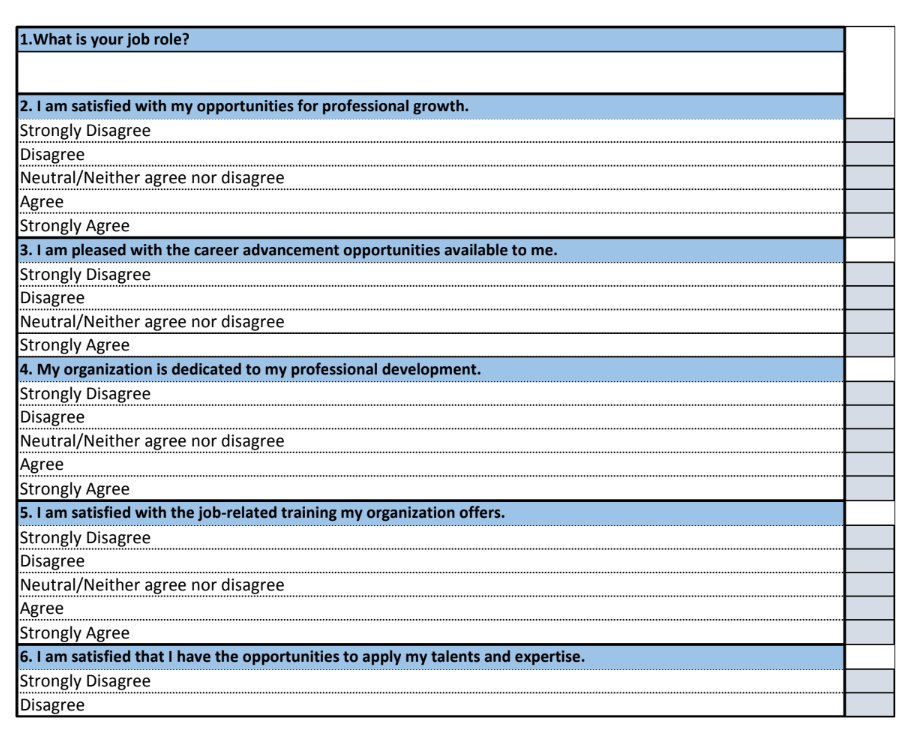
Source: Intezer
According to Intezer, the spreadsheet includes malicious VBA code that executes when macros are enabled. This code works to install updated versions of the TONEDEAF and VALUEVAULT malwares. TONEDEAF is a backdoor malware, while VALUEVAULT is a browser credential stealer.
There is nothing truly novel about this spear phishing scam – an email is sent to specific users, utilizing content designed to make it look authentic. An attachment containing malicious code was attached, all with the intent of installing malware.
If I had a nickel for every time this kind of scam was run, I’d have enough money to own a software company!
It’s important to teach employees about the basic block and tackling of cybersecurity. Suspicious emails, strange email addresses, odd attachments, the need to enable macros – all of these are red flags that users who undergo Security Awareness Training already understand and identify.
We’ve seen espionage targets like this before where the goal is to obtain U.S. secrets. The attacking of companies that do business with them is a nice added touch – it can facilitate island hopping from the partner business to the research firm target pretty easily. Both kinds of companies need to educate their users – otherwise, one of them (or both!) will find themselves a victim.
 Here's how it works:
Here's how it works:




