Ransomware tops the list of attacks for insurers of the food and beverage industry. Outdated software and lax user concern for security controls provide attacker with a way in.
Cyber defense insurer Coalition recently presented to food and beverage industry manufacturers at the recent ProFood Tech conference on current state of cybersecurity. Ransomware was the primary topic, with Coalition citing phishing attacks and social engineering being the normal means of accessing the network.
According to Coalition, the downtime on the plant floor resulting from a ransomware attack, mixed with the recovery time necessary may be far more costly than simply paying the ransom.
The Coalition speaker noted that half of the companies involved in protracted recoveries from attacks go out of business
According to the presentation, the weakest link is the user. It’s no surprise – phishing and social engineering techniques are evolving, but users and their sense of security aren’t. Organizations need to educate users on the importance of corporate security as part of their role in the organization, the types of attacks that exist today, and how to safely utilize email and the web without falling prey to cyberattack.
Security Awareness Training provides all users – whether knowledge workers, plant operators, or anything in between – with continual training designed to promote a vigilant mindset that lowers the risk of successful cyberattacks such as ransomware. It’s far less expensive to prevent ransomware than it is to remediate an attack. Take heed from Coalition’s warning and address your weakest link – the user.
Brand-New Ransomware Simulator Tool Now with Cryptomining Scenario
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
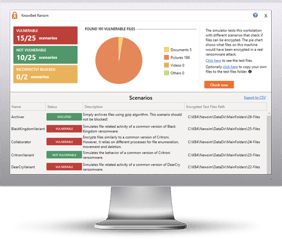
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Don't like to click on redirected buttons? Copy and paste this link into your browser:
https://info.knowbe4.com/ransomware-simulator-tool-1