 Long gone are the days of tacky landing pages that barely impersonate a brand; threat actors are improving their social engineering game well enough to make anyone believe it’s the real thing.
Long gone are the days of tacky landing pages that barely impersonate a brand; threat actors are improving their social engineering game well enough to make anyone believe it’s the real thing.
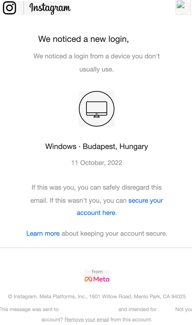
Security researchers at Armorblox provide imperative details into a new Instagram impersonation scam with parts of the attack looking very credible. According to Armorblox, the scam targeted over 22,000 users at a single large educational institution. The scam started with a realistic-looking email claiming to be from Instagram support:
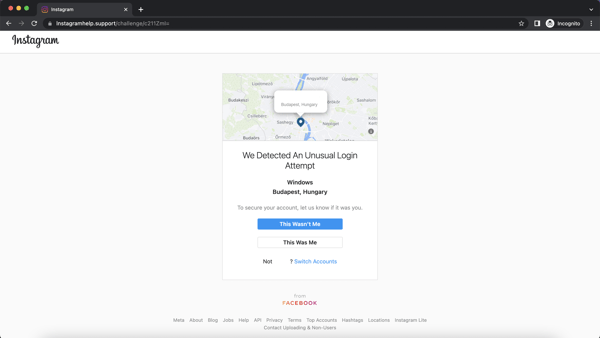
Upon clicking “secure your account here”, users are taken to an impersonated Instagram support page where the victim can assert that the “unusual logon” was or wasn’t them.
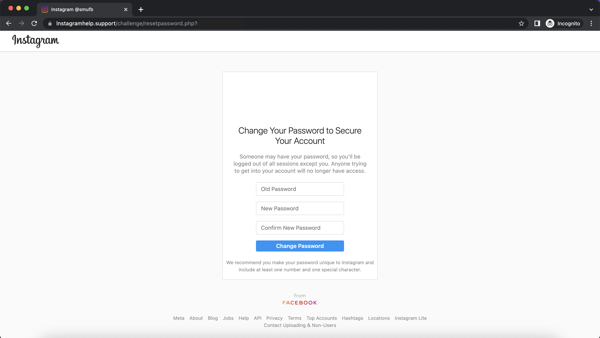
Lastly, victims are taken to a page to “reset” their password. The only think on this page of interest to the scammer is the users “old” (read: current) password, which will be used to logon to the victims Instagram account and leverage it to trick followers in a subsequent scam.
At the end of the day, there’s one part of just about any phishing attack that doesn’t seem to jibe – the email sender’s domain. Because threat actors are often using throwaway domains, the instance of “instagramsupport [dot] net” in the email above – which does align with the branding fairly well – is pretty impressive and unusual.
Corporate users should be taught via Security Awareness Training to be watchful for any unexpected emails and scrutinize the sender’s email address; if it looks wrong, it should be considered suspect and ignored.
 Here's how the Social Media Phishing Test works:
Here's how the Social Media Phishing Test works:




