We’ve blogged before about spammers using publicly accessible databases to help them with large-scale spam campaigns. Here’s what one such recent campaign looks like from the insider.
Security researcher Bob Diachenko discovered a publicly-accessible database containing 11.5 million compromised emails and plain-text passwords which were being used in a massive spam operation. Diachenko and Zach Whittaker at TechCrunch analyzed the server and figured out how the operation worked.
It did this by taking the subject line of the sent email along with the recipient’s email address, making it look like the recipient was replying to the victim’s original email.
This message is first sent through a proxy server made up of several cell phones, and it then goes through the victim’s email provider using the victim’s credentials. This entire process is automated and took place hundreds of times each second.
The emails themselves contained links that directed the victim to a spoofed news website promoting a bitcoin scam or a phony weight loss pill. Users in the US were taken to a spoofed CNN page, while users in the UK would be sent to a fake BBC page.
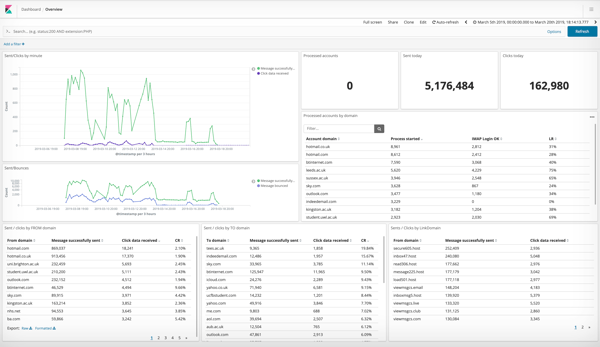
The spammer also left the database’s Kibana user interface exposed, allowing Diachenko and Whittaker to observe the results of the spam campaign in precise detail. Tracking links in each spam email allowed the attacker to determine which email domains were most vulnerable and had the least effective filters.
The campaign ran for ten days between March 8 and March 18, and the attacker sent 5.1 million spam emails during this time. Nearly 163,000 of these emails of these emails were opened by the recipient. Whittaker notes that “it’s not the first time we’ve seen a spam operation in action, but it’s rare to see how successful it is.”
He adds that, while this server has been neutralized, the spammer has most likely shifted operations to another server. The campaign highlights how criminals can combine several different attacks to maximize their success.
Using credential stuffing and email spoofing to launch a widespread, yet personalized, spam campaign was apparently very effective. New-school security awareness training can teach your employees how to avoid falling for phishing emails even if they appear to be sent by someone they know.
TechCrunch has the story: https://techcrunch.com/2019/04/02/inside-a-spam-operation/






