 A threat actor tracked as DEV-0569 appears to be using a combination of Google Ads and impersonated websites to compromise credentials and distribute malware to gain network access.
A threat actor tracked as DEV-0569 appears to be using a combination of Google Ads and impersonated websites to compromise credentials and distribute malware to gain network access.
These days there is plenty of talk about Initial Access Brokers, but often, little is known about their specific actions other than the resulting presence of access to networks and assumptions that they are using the same tactics and techniques as cybercriminals that are responsible for an entire attack.
Recent Twitter posts from cybersecurity researchers like Germán Fernández, DEV-0569 is using Google ads to infect victim machines.
1/ DEV-0569, current distribution via #GoogleAds.
— Germán Fernández (@1ZRR4H) January 21, 2023
1.- #Gozi aka #Ursnif (bot) ↓
2.- #RedLine (stealer) ↓
And if the conditions are right, possibly:
3.- #CobaltStrike (C2) ↓
4.- #Royal Ransomware 💥
(No more BatLoader in the infection chain) pic.twitter.com/mYp8hSU7FH
According to Bleeping Computer, the ads are for software titles including LightShot, Rufus, 7-Zip, FileZilla, LibreOffice, AnyDesk, Awesome Miner, TradingView, WinRAR, and VLC.
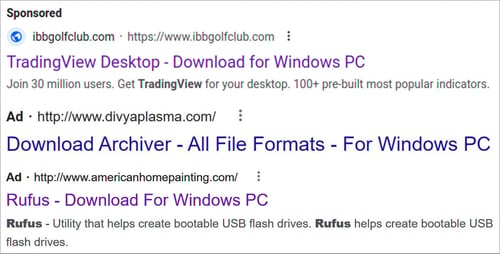
Source: Bleeping Computer
This ad takes victims to a lookalike website where the desired tool (read: malware) can be downloaded and installed. In the end, a foothold is established by DEV-0569 on an endpoint within a victim organization, with its access sold on the dark web.
The use of ads is a smart use of social engineering. When’s the last time you assumed a Google ad was not only illegitimate, but malicious? Right… never.
This kind of simple innovation is why organizations – including and especially members of IT – need to undergo continual Security Awareness Training that keeps them up to date on the latest social engineering tactics and phishing scams. The alternative is, eventually, one of these malicious methods is going to fool just the right person within your organization.
 Here's how it works:
Here's how it works:




