 This new attack is pretty simple to spot on the front, but should it be successful in launching its’ malicious code, it’s going to take its victims for everything of value they have on their computer.
This new attack is pretty simple to spot on the front, but should it be successful in launching its’ malicious code, it’s going to take its victims for everything of value they have on their computer.
The new Mr. Anon infostealer captures much more than just browser caches and passwords. It also uses basic social engineering tactics that prove to be effective enough to make attacks successful.
It begins with a simple hotel booking email seemingly sent to the victim recipient by mistake, using a subject of “December Room Availability Query” and what appears to be a PDF booking attachment.
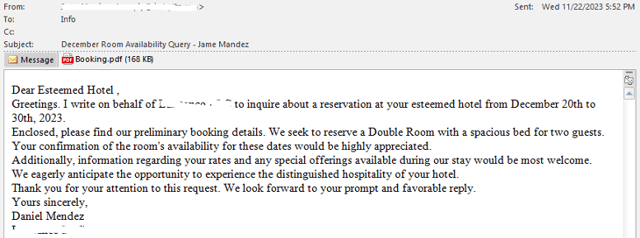
Source: Fortinet
Once opened, the PDF pretends to need a Flash update, requiring the user to interact and launch the malicious attachment, which is a combination of a .NET executable, embedded .zip files, PowerShell scripts, and a downloaded payload – a python script.
This attack has a few interesting aspects to it. First is the social engineering tactics used. There’s the email premise of the room request, but then there’s also a step when the python script is run; the attackers purposely post a window with the title of “File Not Supported” with a status message indicating “Not Run: python.exe.” to make the victim think the script never ran (helping to maintain a state of stealth).
There’s also all the obfuscation done to evade detection. The malicious code is, in essence, the python executable. This file is encoded with cx-freeze, requires being downloaded from code held within a .zip file that is, in turn, embedded within the .exe attachment – all to avoid detection. The use of PowerShell itself is another step in attempting to avoid detection, given it’s a part of the Windows OS.
Lastly, there’s the actual infostealer capabilities of this attack. The Mr. Anon infostealer captures more info that most of its predecessors:
- Browser data
- Desktop-based digital wallets
- Password or connection-related browser extensions
- Messages
- VPN clients
- Browser-based digital wallets
- Data from within 26 different file types
Any data gathered is compressed into a single .zip file and then uploaded to a public file-sharing website.
Because users habitually maintain passwords to cloud-based corporate resources within their browsers, it’s necessary to protect against this attack by educating users through new-school security awareness training on how to spot this attack and avoid engaging with included attachments or links.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.
 Here's how it works:
Here's how it works:




