 It appears that the use of Microsoft CHM files is gaining popularity, and from the way this latest attack works, it’s a rather ingenious and flexible method that could become more prevalent.
It appears that the use of Microsoft CHM files is gaining popularity, and from the way this latest attack works, it’s a rather ingenious and flexible method that could become more prevalent.
What attackers need is some kind of malicious platform or app that can execute code, launch other apps, and perform tasks. We’ve seen a lot of use of Java, PowerShell, etc. But a new attack found by security researchers at Trustwave uses Microsoft Compiled HTML Help (CHM) files. What makes CHM files so powerful is that they can make the Microsoft Help Viewer (a legitimate program) load CHM objects, which can include additional malicious content or code. While CHM files are most definitely not a scripting language, it does provide threat actors with a powerful way to live off the land.
In the case of the most recent attack, the initial attack uses a phishing email with an ISO file. Once opened, the ISO file contains a java snippet that launches an included executable that loads the CHM files. The CHM file is used to load Vidar, a nasty information stealer that can harvest data, online and cryptocurrency account credentials, credit card information, and more. We also have seen CHM files used in a recent CryptoWall attack, showing that there is potential to see more of CHM in future initial attacks.
The good news is that this latest Vidar attack uses a pretty rudimentary phishing attack to be launched in the form of a simple email with an attachment:
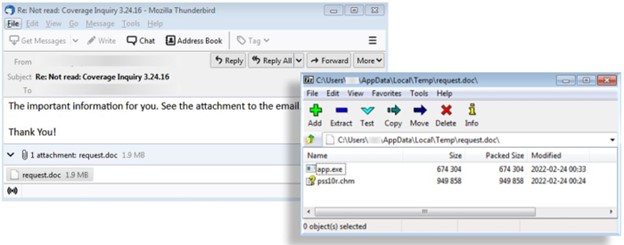
Users that have taken Security Awareness Training will be able to spot this type of attack a mile away and simply delete the email, rather than engage with its malicious content.
 Here's how it works:
Here's how it works:




