 Using the simplest tactic of not including a single piece of content that can be considered malicious, these types of scams are making their way to inboxes every single time.
Using the simplest tactic of not including a single piece of content that can be considered malicious, these types of scams are making their way to inboxes every single time.
What happens if the malicious bit of a phishing scam is nothing more than a phone number – and it’s embedded within an image to boot? We’ve covered these kinds of scams before – particularly those pretending to be Amazon. It’s a brilliantly simple technique used to get past security scanners; by not having any known-malicious content (remember, it’s just an email with an image in it), it gets through to the users Inbox.
But security company Inky detected a recent example of these attacks impersonating Geek Squad by using optical character recognition (OCR) within the embedded images.
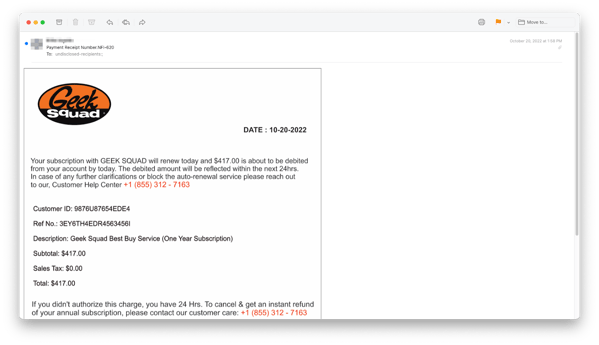
Because many email clients automatically display attached images, this scam is enabled and requires the victim to call the phone number displayed in the image (as there is no link to click and the sender email addresses are often indicated to be a “no-reply” type of email account.
Victims call the number and criminal call centers use social engineering to trick the victim into giving up their credit card details. It’s a scam that is going to require that every email scanning security solution to offer OCR as a means of detection which is extremely hard to scale due to the CPU required.
Until then, users need to play a role in their organization’s security – something taught through continual Security Awareness Training – and see the scam for what it is, and ignore it appropriately.
 Here's how it works:
Here's how it works:




