 As executables and scripts are unable to bypass security solutions as attachments, cybercriminals turn to HTML as a means of obfuscation and malicious execution.
As executables and scripts are unable to bypass security solutions as attachments, cybercriminals turn to HTML as a means of obfuscation and malicious execution.
According to analysis from security vendor Avanan, executables and Office documents as malicious attachments are almost non-existent – thanks to the solid efforts on the part of security companies and Microsoft. But cybercriminals are still succeeding in harvesting credentials as made evident by their use as the top threat action in data breaches, which makes HTML files a perfect tool. According to Avanan, 53% of malicious attachments today are HTML files.
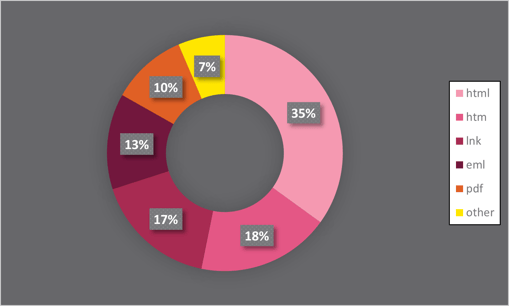
Source: Avanan
Beyond their ability to host links, JavaScript, embedded images, HTML entities, and customized CSS to escape detection, they also create a completely threat actor-controlled environment in which to impersonate legitimate websites to convince victims to provide their username and password. Additionally, by not needing to point the victim to a malicious website (that can be flagged as being suspicious by security solutions), there’s a better chance of a successful attack.
Those of us that are more technically-minded already know there’s no real reason an HTML file ever needs to be sent as an attachment, but users still are falling for this technique, making it necessary to educate them with Security Awareness Training on how these attacks work and how to identify them, reducing organizational risk.
 Here's how it works:
Here's how it works:




