 In my recent comment on the Solarwinds’ cyber attack, I made the claim that using multifactor authentication (MFA) can sometimes make you more at risk than using a simple login name and password. I wrote this:
In my recent comment on the Solarwinds’ cyber attack, I made the claim that using multifactor authentication (MFA) can sometimes make you more at risk than using a simple login name and password. I wrote this:
“As many MFA users and administrators are finding out, using MFA can make some targeted hacks against you far more likely if they are attempted. I’ve had a credit union security officer tell me that he/she has suffered more successful hacks since his organization implemented MFA and he wished they would go back to login names and passwords. They wouldn’t be the first to reverse course. Many multi-millionaire cryptocurrency traders that got exploited explicitly because they were using MFA then went back to simple login names and password security years ago. Using MFA was just too much risk out of their control.”
First, I want to state on the outset that I like MFA and I think MFA significantly…significantly…reduces many types of cybersecurity risk. For example, you can’t be phished out of your password if you don’t have or know your password. But, there is a big difference between saying and believing that and believing that you are significantly less likely to be compromised because you use MFA. As many new companies which converted to MFA for authentication learned, it doesn’t stop all hacking. And none of the individuals I know who went back to simple login names and passwords after being hacked because of MFA regret their reversals. Here are reasons why MFA may increase the risk of some forms of hacking:
A Lot of Dependencies
When I was writing my latest book, Hacking Multifactor Authentication, I created a dependencies list for MFA as seen in the figure below:
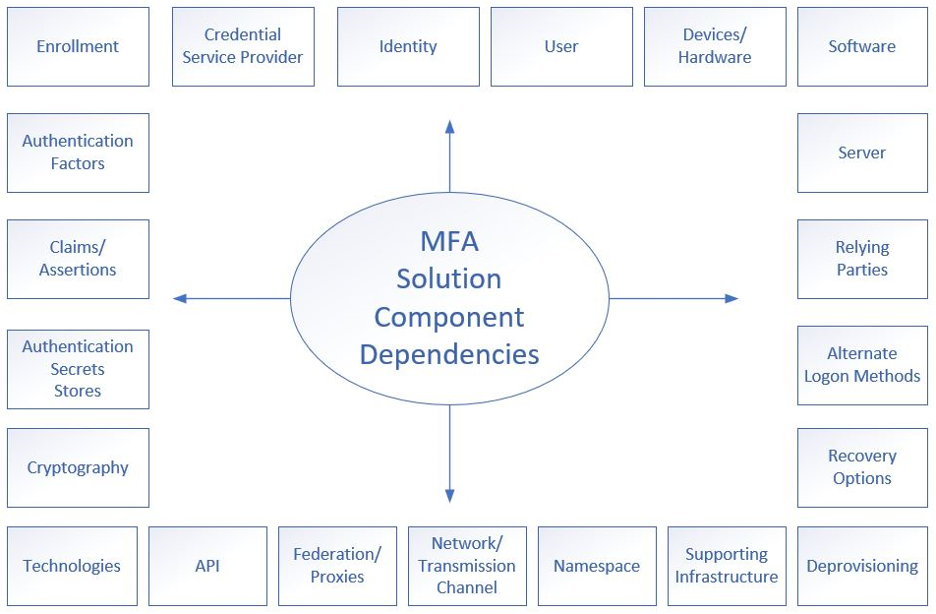
It includes over 20 components and each of those dependencies creates a potential avenue for an attack. To be fair, logon name/password systems, depending on how complex they are, can have nearly as many dependencies. But most logon name/password systems running on most websites have far less dependencies. Many are as simple as a logon screen and password database repository along with a few lines of scripting.
Increased Complexity
Any MFA system is more complex and harder to learn than using a login name and password. I’ve listened or viewed nearly a dozen reports of studies on MFA usability and all of them have concluded that a significant percentage of the participants involved could not use the MFA device correctly. Even the simplest, single-factor (1FA), USB plug-in devices are harder for people to learn to use than a login name and password. In one 1FA study, the participants gave or threw away their 1FA devices after the study was over, not realizing that whoever plugged them in would now be logged on in their security context. None of the participants, when given the choice to keep their free MFA device kept using it after the study was over. Compare that to the easy and use of password security. I’ve seen two-year-olds and ninety-year-old Alzheimer’s patients use login names and passwords to login to whatever they were trying to get to.
If you want to read more about MFA and usability, try these sources:
- A Usability Study of Five Two-Factor Authentication Methods
- Assessing Usable Security of Multifactor Authentication
- Exploring Adoption of Two-Factor Authentication at a University
The reason why usability is important is that as authentication solution complexity goes up, the more likely the end user is to make a mistake, use it incorrectly, or for a hacker to take advantage of that naivety. In one study I read, many of the users of a 1FA USB plug-in device, where all they had to do is insert the device and press on a button located on the device, thought the device was a fingerprint reader or inserted it upside down, therefore invalidating or damaging the device. If users can’t insert a USB device correctly and press on a button to authenticate, how can we expect the masses to handle anything more sophisticated?
Much of the Control Is Out of Your Control
Most password hacking is due to theft and most of that theft happens because a user is tricked into providing their login credentials or running a Trojan Horse program in response to a phishing email or website. This is to say that if a user is good at avoiding phishing, he/she will be at far less risk of password theft.
Many of the MFA hacks are hacks that had nothing to do with the owner’s behavior. For example, the vast majority of MFA on the Internet (used by banks, hotels, credit card companies, etc.) involves Short Messaging Service (SMS) text messages. SMS text messages are tied to a user’s cell phone number. And that number can be moved from the victim’s legitimate phone to the hacker’s cell phone without any involvement by the end user (using a hacking method called SIM Swapping). The user made no mistake other than relying on an SMS-based MFA method to protect him/her and it ended up hurting him/her in the end.
Biometrics Are Easy To Steal and Fool
Biometrics (e.g., fingerprints, palm veins, hand geometry, iris prints, retina vein prints, etc.) are not secrets. For example, your fingerprints are everywhere, in public, for anyone to copy. Your retina vein prints may not be publicly everywhere, but if they are stored, like all biometrics, they can be stolen. And once stolen, how can they be prevented from being used on any system that relies on them by the party who stole them?
For example, in June 2015, every person who had ever applied for a U.S. government security clearance up until that point had their fingerprints stolen by Chinese hackers. My fingerprints were in that attack, so were my wife’s, and she gave her fingerprints in 1982 when she was a teenager working at a shipyard.
It still happens all the time. In August 2019, over one million fingerprints were publicly exposed on a popular mobile biometric platform. When the breached company was notified by researchers of the exposure, they didn’t even bother to reply to the researchers and didn’t immediately fix the problem.
How is anyone going to fix this problem once your biometric attributes are stolen? You can’t change fingerprints (at least easily), and even less so for retina scans and iris prints. But with passwords, anyone can quickly and easily update their password.
On top of that, most biometric readers are fairly easy to fool. Your biometric attribute may be unique in the world, but the way they are read by the biometric scanner and digitally compared is far less accurate than biometric vendors want to publicly admit. Every time a biometric solution vendor says their solution can’t be fooled, there’s video of a 15-year-old kid fooling it on YouTube using $2 worth of materials. The dirty little secret of biometrics is that they can be much more accurate, but most of the users would not put up with the sheer amount of resulting false-negatives (known as Type 1 False Rejection errors).
MFA Often Does Not Have Traditional Protections
Most passwords have expiration dates, but many types of MFA do not. Many hardware-based MFA devices never expire. Mere possession is enough, no matter how many years away from their issue. For example, Google Authenticator initialization codes, often presented in Quick Response (QR) code form, never expire. Many Google Authenticator users have had their authentication compromised because a hacker found their related QR code in their email trash. Many MFA solutions involving PINs don’t have traditional bad login limitations; so attackers can guess thousands to millions of times without the MFA login locking them out. And so on. Many of the protections we often take for granted in the password world are not implemented in the MFA world.
MFA Can Be Used Against You
I’ve had dozens of people write to me asking how they can recover their social media account (e.g., Facebook, Twitter, Instagram, etc.) that was taken over by hackers. But the key new problem is that although the victim did not use MFA, the attacker, after taking over his/her account, enables MFA. This change absolutely prevents the victim from getting control and access to his/her account ever again. Everything that the victim had stored in their long-time social media account…pictures, video, etc., which was stored nowhere else (another problem) becomes unreachable forever. I’ve yet to find a victim of these types of takeovers scams that has been able to recover his/her account. Everything gone forever, because of MFA.
Easy Recovery
All the big MFA vendors (e.g., Google, Microsoft, etc.) give users the ability to recover around their MFA solutions. They understand that MFA users often lose their MFA devices or have to install new instances. They don’t have the money to have a human handle the recovery, so they give users, usually, multiple ways to access their account, all of which are much less secure than the MFA solution it is bypassing. Hackers love this fact.
For example, anyone who simply knows the user’s email address can usually get a “recovery code” sent to the user’s previously registered alternate email address (which the attacker has usually previously compromised using phishing). Or the user can be asked a series of predefined and answered personal knowledge questions, such as “Your mother’s maiden name” or “Your favorite car”, all of which are far easier to guess or find on the Internet than the victim’s password.
This is despite the fact that in 2015, Google did a study which revealed that 20% of some recovery questions could be guessed in the FIRST TRY by hackers! And 16% of the time, the answers could be found in someone’s social media profile. There have been decades of account takeovers due to hackers guessing or finding someone’s personal knowledge questions, and yet they are still often a requirement to be used on thousands of the world’s most popular websites, including banks and stock trading sites.
Why Should We Still Use MFA?
I could go on and on with examples of how easy MFA is to hack. I could write a book on the subject. I did write a 500+ page book on the subject. With that said, I don’t want to say that MFA is completely bad. MFA does significantly prevent some forms of hacking and for that reason alone, should be considered and used by everyone (until something else better comes along).
But it is dangerous for management, IT security people, and users to think that using MFA makes them significantly less likely to be hacked, because that simply isn’t true. It does make them less likely to be hacked, but only on a small portion of the things that MFA protects, and every MFA solution itself can be hacked many different ways. And not understanding that fact can lead to very negative outcomes. Just ask the cryptocurrency traders who went back to simple login names and passwords or the business entities suffering under INCREASED successful hacking after they implemented MFA. Most MFA users don’t think they can be compromised by a regular-looking phishing email. And that belief is dangerous.
If you use or manage MFA, make sure all stakeholders understand what the MFA solution does and doesn’t protect against. Make users aware of all the ways their authentication protection can be compromised and bypassed, and educate them to prevent phishing attempts and malicious attacks, especially for the types that specifically target their MFA solution.
Anything can be hacked, including MFA. That means your security awareness training shouldn’t lessen just because you use MFA. And I’m not saying this as just an employee of KnowBe4, the world’s most popular security awareness training platform. I’m saying this as a 33-year computer security veteran. Knowledge is power. Don’t let using MFA lessen the knowledge transfer.






