.jpg?width=300&name=iStock-1176438482%20(2).jpg) You did it - your organization has finally decided to take the first step in implementing security awareness training. But with starting something new there tends to be a 'deer in the headlights' moment wand you ask yourself common questions - What now? Where do I begin?
You did it - your organization has finally decided to take the first step in implementing security awareness training. But with starting something new there tends to be a 'deer in the headlights' moment wand you ask yourself common questions - What now? Where do I begin?
One of the most important starting factors in a security awareness training program is a framework or checklist to ensure your users are on the right track to avoid any potential attacks in the near future.
The most critical components for a good security awareness training program are:
- Content - Content is king! As humans, we all gravitate toward different types and styles of content. Approaching content as one size fits all would be a mistake. Think through the different employee types/roles you have and match different groups in your organization to the content that would likely resonate with them the most.
- Executive Support & Planning - Reporting materials that will help you continue to prove the value of the program to your executive team are needed to maintain the time and budget you need to run a successful program. This can also be used to show auditors/regulators that you are doing the right thing.
- Campaign Support Materials - A successful program shouldn’t be ‘one and done’, treat it as a marketing endeavor. Once-a-year, ‘check the box’ training just to satisfy compliance requirements will not help to change user behavior. Presenting the information in different ways, when it coincides with the context of their life, is what will influence users' decisions and make it EASIER for them to make smarter choices.
- Testing - People need to be put in a situation where they will have to make a decision that will determine if the organization gets breached or not. Phishing simulations prompt users to either click a link, report the phish, or do nothing. You want to give them an opportunity to report phishing attempts and help the organization increase resilience. If they do fall for the phish, you want the ability to do training then and there to create a learning moment. Doing nothing isn't ideal as it leaves the potential threat out there and there's an opportunity for others in the organization to click.
- Metrics & Reporting - You need to be able to show you are closing security gaps. Reporting is also useful for optimizing campaigns based on past results. You want insight on what is working well and what can be improved upon.
- Surveys/Assessments - These types of tools can help you understand the attitudes of your organization and how well your program is resonating with your people so you can adapt. Think of it as a pulse check of subtle nuances that are different than metrics/reporting such as opinions, frame of mind, etc.
Your awareness program and content are the ‘face’ of your department to the rest of the organization. Especially if you are in a larger organization, a good portion of your coworkers don't know you, they only know what your department produces. For that reason, it HAS to be as good or better than anything else the organization is doing. Otherwise, security is seen as 'other', unimportant, an afterthought.
Program development - Don't rely on formal training alone
Learning doesn't just happen at one point in time, think about the entire context of user experience. Consider this 70:20:10 model for learning and development:
- 10% Formal - Structured learning, LMS courses, training days, etc. This is about the maximum amount of time you can allot per user for formal training. You need to be thinking about ways to address the other 90% of someone's experience in the organization.
- 20% Informal - This would include asking others, collaborating, webinars, watching videos, reading, etc. Think about how to build an informal community for users to know where to go to get the information they need when they are actually seeking it out.
- 70% Experiential - On-the-job, social, in the workflow, corporate and departmental culture. From a security aspect, ignoring that 70% social/cultural component, puts you at a great disadvantage. Think about ways to address that entire 100%. Vendor support systems can be helpful here.
The four stages of competence:
- Lack of Awareness - Unconscious Incompetence or "I don't know that I don't know something." They are blissfully unaware and their behavior will reflect that.
- Awareness - Conscious Incompetence or "I know that I don't know something." They now realize they don't have all the knowledge and tools they need. We can hope that will move them to the next stage.
- Step-by-step - Conscious Competence or "I know something, but I have to think about it as I do it." They either need to access stored information or really intentionally weigh all the options then come to the right conclusion.
- Skilled Stage - Unconscious Competence or "I know something so well that I don't have to think about it." This is where most of us are with pattern-based behaviors like driving, brushing our teeth, etc. At some point these things were difficult, but we build up to this stage.
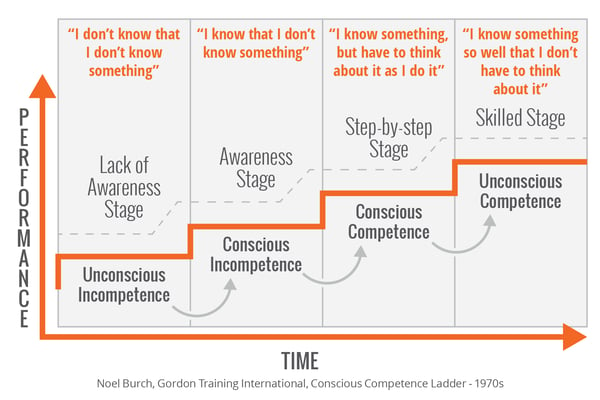
The problem with most traditional security awareness training programs is that they let users linger in stages 1 and 2. Design your program to push users all the way through to stage 4. Getting users to stage 4 with constant training and simulation is ideal and cultivates the kind of behavior you want, that may protect your organization from a breach.
Plan like a marketer. Test like an attacker.
Think of your program like a multi-channel marketing campaign - delivering different types of content at different times targeting different audiences going through different channels so you have a constant barrage of information and working within the context that those different people are in. You need to be constantly building reflexes and building muscle memory for your people, which is where the testing component comes in. No matter which tool you use, even if you are using a homegrown program, you need to send a social engineering test like a phishing test to users at least every 30 days. By doing both training and testing, you are running a hearts and minds campaign like a marketer would. Over a period of time through different channels/mediums you can start building influence in the mind. Supplementing that with frequent phishing attacks means you are building muscle memory so users naturally react in the right way.
Make your content interesting and relevant to your users
If content isn’t appealing to the audience it’s in front of, it doesn’t feel relevant to them and won’t stick with them. Relevance is key. The human mind learns through storytelling, and security awareness training is no different. A story contains contextual information that a written policy simply cannot. People learn in many different ways and naturally gravitate toward different types of content, so it makes sense that if you use a one-dimensional approach in training, you are going to lose a huge part of your audience. You want to come to the learner with content suited for them rather than try to make them learn in one certain way.
Don’t just add more content for the sake of having more content. A diverse portfolio of different types of content will get the message to resonate. Repetition is key for knowledge to stick, and you need to have variety to go along with a repetitive message. Showing the same exact course over and over isn’t going to make much of a difference. If you're not sure where to begin, you're not alone. Many vendors can provide recommendations and best practices. Start there and adjust over time according to what works for your environment.
With the bad guys knowing your untrained users are the weakest link into your network, it is more important than ever to add security awareness training and strengthen that people layer. Today’s email filters have an average 7-10 percent failure rate; and about 30 percent of data breaches are caused by repeat offenders from within the organization. You need a strong human firewall as your last line of defense.
 Here's how it works:
Here's how it works:




