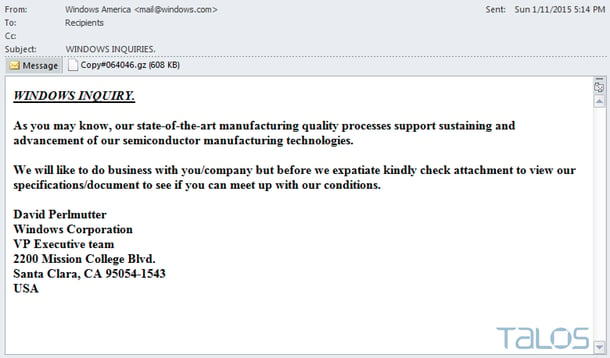
InfoSec researchers at Cisco's TALOS group discovered a strain of malware that spreads through phishing. Attackers use social engineering tactics to entice users to download, unzip, and open the attachments that ultimately result in the user’s compromise. The strain is dubbed Rombertik, monitors everything that happens inside an infected machine's browser and exfiltrates it to a server controlled by the attacker, similar to Dyre. However, when it detects that it is being analyzed, it takes extreme evasive action; it wipes the Master Boot Record (MBR) and home directories, trapping the machine in an infinite boot loop. Here is an example phishing attack (screenshot courtesy Cisco).
The MBR is the first sector of a computer’s hard drive that the machine reads before loading the operating system. However, deleting or destroying MBR involves re-installing of operating system, which almost always means data is lost. In what is likely a bit of sick humor from the crims, in case it cannot get acccess to the MBR, Rombertik works just like ransomware and starts encypting all files in the user’s home folder (e.g. C:\Documents and Settings\Administrator\).
The malware chooses a random 256-byte encryption key for each file, but none of the keys is saved anywhere, so you end up with what is effectively random, shredded bits instead of your files. After the MBR is overwritten, or the home folder has been encrypted, the computer is restarted. Only files with the extensions .EXE, .DLL, .VXD and .DRV will survive.
After further analysis of the threat, Blue Coat shared in a Thursday blog post that Rombertik was “not standalone malware,” but an additional layer around existing crimeware. Rombertik samples it analyzed, for instance, appeared to be used as an obfuscating wrapper for the DarkComet RAT, a password stealer (potentially Pony Loader) and Andromeda malware.
The upshot: Rombertik begins to behave like a wiper malware sample, trashing the user’s computer if it detects it’s being analyzed. While the Cisco Talos team has observed anti-analysis and anti-debugging techniques in malware samples in the past, Rombertik is unique in that it actively attempts to destroy the computer’s data if it detects certain attributes associated with malware analysis.
What To Do About It:
Ultimately, you need to practice defense-in-depth which protects your entire attack surface, but here are two tips that will mitigate attacks like this with the best bang for your IT security budget:
1) Have multiple layers (and different AV engines) of malware scanning in place; the firewall, your mail server/email gateway, and the desktop. That means a different vendor, using a different AV engine for your firewall, your mail server/email gateway and your endpoint AV.
Then filter out almost all email attachment types except a few essential ones. Check out which AV engines your vendors use, because there is a lot of OEM-ing going on in the AV space, which might result in you using the same engine, but with a different label. Not good.
2) Step your users through effective security awareness training and follow up with regular simulated phishing attacks which will keep them on their toes with security top of mind. Find out how affordable Kevin Mitnick Security Awareness Training is for your own organization. Get a quote now and be pleasantly surprised:





