 OK, here is a new spear phishing scheme that attacks your development team. Cyber criminals with IPs resolving to Russia hijacked an extension for Google Chrome and abused their illegal access to push out spam to unsuspecting users.
OK, here is a new spear phishing scheme that attacks your development team. Cyber criminals with IPs resolving to Russia hijacked an extension for Google Chrome and abused their illegal access to push out spam to unsuspecting users. The security incident happened to Copyfish, a type of Optical Character Recognition software which allows users to extract text from images, video, and/or PDF documents. Only the program’s Chrome extension suffered as a result of the attack, the Firefox component was not affected.
Copyfish’s developer, a company known known as a9t9 software, revealed it traced the trouble back to a phishing attack that occurred on 28 July:
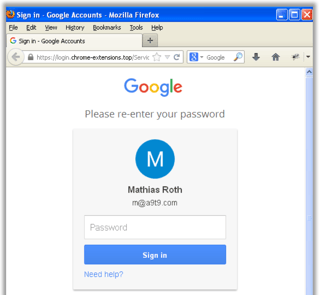
“A team member received an email from Google’ saying that we need to update our Chrome extension (Copyfish) otherwise it would be removed from the store. “Click here to read more details” the email said. The click opened the ‘Google’ password dialog, and the unlucky team member entered the password for our developer account. This looked all legit to the team member, so we did not notice the phishing attack as such at this point. Phishing for Chrome extensions was simply not on our radar screen. [sic]”
Tripwire has all the details.
The upshot?
Enable 2-factor authentication on all your critical accounts. Oh, and get some security awareness training.




