 Rudy Friederich, a KnowBe4 friend at Marshal Security LLC sent me the following interesting tips related to finding out if you are the victim of Business Email Compromise. He wrote:
Rudy Friederich, a KnowBe4 friend at Marshal Security LLC sent me the following interesting tips related to finding out if you are the victim of Business Email Compromise. He wrote:
"Any business which hasn't developed a formal policy on double checking/'checks and balances' of the validity of financial transactions—both coming and going—is just asking for trouble. Email account security should be a section of this policy. Things like:
- Regularly checking account activity
- Regularly checking 'Trash' folder to see if attacker has set up a rule directing certain emails to go into 'Trash.'
- Regularly checking the list of all your folders to see if a folder has been created by an attacker so he could set up a rule directing certain emails to go into this folder. (For example, if you created your own folder called 'Junk' in Gmail and then used the 'Hide' feature, would its existence really jump out at you - even if you saw it on a list?)
- Regularly checking the list of all your folders to see if a sub-folder has been created by an attacker within one of your legitimate folders so he could set up a rule directing certain emails to go into this sub-folder.
- Regularly checking 'Settings' to see if emails are being forwarded to an attacker's account
- And enforce a multi-factor authentication system
Train your critical staff to go over the extent of the problem and the policy and the countermeasures you have developed.
To illustrate the critical level of the problem, Friederich commented: "The problem is so severe that I would even consider requiring all employees to change their passwords on Monday morning. Start afresh. Know for sure - or at least for better sure - that nobody can continue to get into your email accounts."
We all know the practicality of that measure is low, but how about some additional features in email clients that look for points 1-5 above, and alert the end-user or admin that something is amiss? That sounds like a great new security feature. Anyone at the software side, you guys listening?
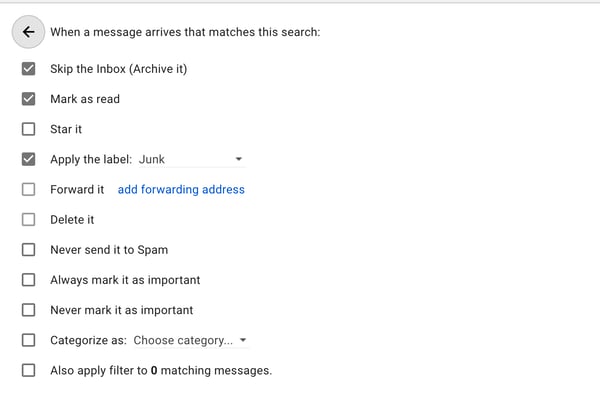
Here is an example, this rule totally works. Coupled with first creating a folder called 'Junk' and then 'hiding' it, an email from a specified email address will appear deep down in your Gmail folders and not show any indication it is a new email. There is no doubt if you had chosen to forward the email to another address that would have worked to.
When we tried to make one such rule work simultaneously for multiple incoming email addresses, however, the rule then did not work for any of the those specified email addresses. So apparently it's something you would have to do for each and every email address you want to set up the rule for.
 Here's how it works:
Here's how it works:




