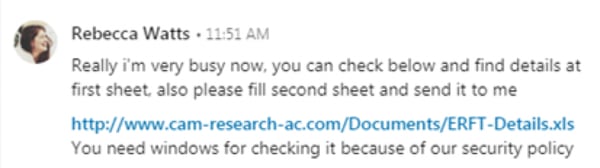
Iranian state-sponsored hackers are increasing their targeting of civilian targets amid escalating tensions between the US and Iran, according to Zak Doffman at Forbes. Doffman cites a report released by FireEye last week, which revealed that the Iran-linked threat actor APT34 is spreading malicious documents on LinkedIn to deliver three new strains of malware.
FireEye describes one case in which the attackers used a LinkedIn profile that posed as a researcher at the University of Cambridge. They used this profile to send messages concerning job opportunities to people on LinkedIn. At some point in the conversation, they would send the victim a download link for a Microsoft Excel file. This file would install a backdoor which could perform data exfiltration and arbitrary command execution on the victim’s system.
FireEye notes that social media platforms in general provide an avenue for attack that can bypass an organization’s email defenses. LinkedIn in particular is a popular target for nation-state espionage operations, and Iranian threat actors have been active on the site before. LinkedIn users tend to have a higher level of trust for unsolicited messages, and the structure of the professional networking site encourages users to connect and converse with people they don’t know personally.
Iran isn’t solely interested in espionage, however. Doffman points to warning from CISA last month which warned that Iranian APTs could turn their more destructive cyber capabilities toward the US.
“Iranian regime actors and proxies are increasingly using destructive ‘wiper’ attacks, looking to do much more than just steal data and money,” CISA’s statement said. “These efforts are often enabled through common tactics like spear phishing, password spraying, and credential stuffing. What might start as an account compromise, where you think you might just lose data, can quickly become a situation where you’ve lost your whole network.”
The vast majority of these attacks succeed due to a security lapse by an employee, such as falling for a phishing attack or using weak or recycled passwords. However, employees can’t be expected to follow security best practices if they don’t know what to do or which threats to watch out for. New-school security awareness training is crucial to train your employees how to protect themselves in an evolving threat landscape. Forbes has the story: https://www.forbes.com/sites/zakdoffman/2019/07/22/critical-linkedin-warning-as-irans-hackers-send-fake-invites-laced-with-malware/






