Researchers at AdaptiveMobile Security, a firm that specializes in cyber telecoms security, have disclosed a new SIM card attack method that could work against over 1 billion mobile phones, and they claim it has already been exploited by a surveillance company to track users.
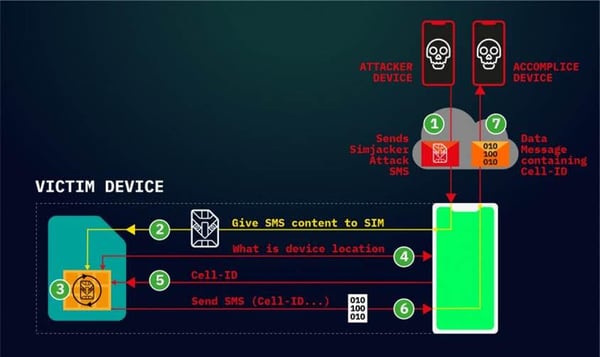
Dubbed Simjacker, the attack involves sending a specially crafted SMS message to the targeted phone. The message contains SIM Toolkit (STK) instructions and it’s processed by the SIM card (the universal integrated circuit card, or UICC), specifically the S@T Browser present on the SIM.
An attacker could use this method to send a wide range of STK commands to the targeted device, including for playing a tone, sending SMS messages, making phone calls, collecting information about the device (location, IMEI, battery, language), launching a web browser, powering off the card, requesting geographical location, and exfiltrating data.
These commands can allow the attacker to track a user’s location, send arbitrary messages on a victim’s behalf (including to premium-rate numbers for fraud purposes), spy on users, deliver malware by instructing the device’s web browser to access a malicious website, and cause a denial-of-service (DoS) condition.
- Turning off cellular connectivity when not actually using the phone and use wireless instead
- Using a non-cellular iPad like an iPad Mini 5, so you can use email more and SMS text messages less
- Using burner phones more and change frequently so perhaps the number you are using is not one as generally known to the outside world
- Turning off SMS messaging (if that's possible) whenever it's not absolutely needed to be on
Yikes. Here is the full article at SecurityWeek:
https://www.securityweek.com/simjacker-sim-card-attack-used-spy-mobile-phone-users






