 Midstride in this year’s holiday shopping, it’s important to realize just how many websites exist that impersonate legitimate online retailers. More importantly, your users need to know how to spot these types of attacks before falling victim.
Midstride in this year’s holiday shopping, it’s important to realize just how many websites exist that impersonate legitimate online retailers. More importantly, your users need to know how to spot these types of attacks before falling victim.
According to threat intelligence vendor SOCRadar’s 2023 E-Commerce Threat Landscape Report: Black Friday to Cyber Monday, the 2023 holiday *scam* season is on par with last year; brands like Amazon, Walmart, Rakuten and Alibaba all have between 4000 and 5000 phishing domains.
These domains (to varying degrees of success) host lookalike e-commerce sites intent on stealing credit card details, login credentials and personal information.
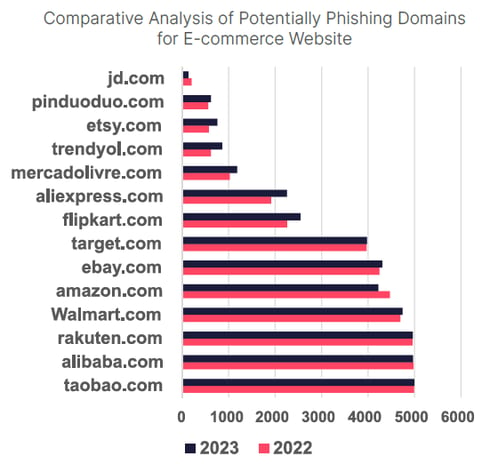
Source: SOCRadar
These sites make it easy for scammers to use social media and the web to advertise their “too good to be true” deals at a known online retailer’s website to get the attention of potential victims.
And if you think you can rely on that green checkbox in your web browser as some indication that the domain being visited is legitimate, that’s a misnomer; that checkbox means the site is using a secure HTTPS session – something now used by cybercriminals in nearly 80% of phishing domains.
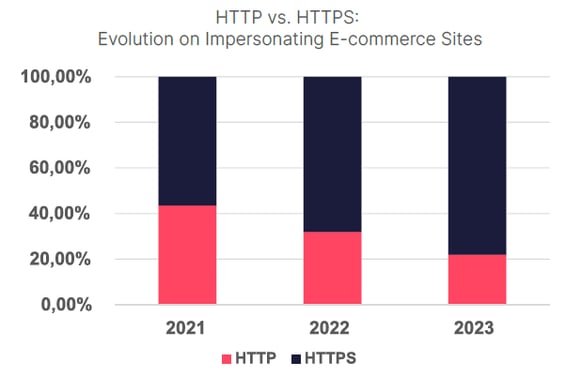
Source: SOCRadar
So, what’s a savvy online shopper to do when saving money is the name of the game?
For organizations, it’s a matter of educating employees through new-school security awareness training to verify the validity of a link prior to clicking it. By doing so, you reduce the risk of enabling a cyberattack with far more malicious intent than just stealing your credit card details.
KnowBe4 enables your workforce to make smarter security decisions every day. Over 65,000 organizations worldwide trust the KnowBe4 platform to strengthen their security culture and reduce human risk.






