 Security experts detected and analyzed a new threat, the Hitler ransomware, that doesn’t encrypt files but simply deletes them.
Security experts detected and analyzed a new threat, the Hitler ransomware, that doesn’t encrypt files but simply deletes them.
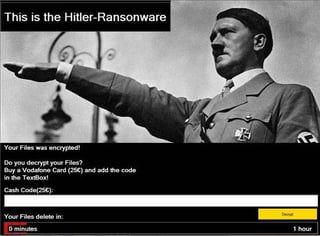
Larry Abrams at Bleepingcomputer commented: " It looks like file deletion is becoming a standard tactic in new ransomware applications created by less skilled ransomware developers. This is shown in a new ransomware called Hitler-Ransomware, or misspelled in the lock screen as 'Hitler-Ransonware', that has been discovered by AVG malware analyst Jakub Kroustek.
This ransomware shows a lock screen displaying Hitler and then states that your files were encrypted. It then prompts you enter a cash code for a 25 Euro Vodafone Card as a ransom payment to decrypt your files."
The developer also appears to be German based on the text found within an embedded batch file. In the batch file is the following German text:
Das ist ein Test
besser gesagt ein HalloWelt
copyright HalloWelt 2016
:d by CoolNass
Ich bin ein Pro
fuer Tools für WindowsThis translates to English as:
This is a test
rather a Hello World
copyright Hello World 2016
: D by Cool Wet
I am a Pro
for Tools for WindowsThis strain looks like a test as it doesn't actually encrypt any files. Rather it removes the extensions on certain directory files then displays a lock screen with an hour countdown timer. After that hour the victim's computer crashes, and upon reboot the ransomware starts deleting those directory files. The technical background of this strain can be found in more detail at Bleepingcomputer.
Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. (Updated March 2016).





