
Rebecca Wynn at securitycurrent.com wrote a great article on how not to become a ransomware statistic in health care:
"In 2017, six of the top ten HIPAA breaches reported to the U.S. Department of Health and Human Services (HHS) stemmed from ransomware.[1] In a typical ransomware attack, important data is encrypted and “held for ransom” until the victim pays a designated amount in exchange for gaining access to the keys to decrypt the data once again. In addition, the cyber-criminal might steal important data before encrypting it and deleting potential backups.
Threats due to ransomware and other types of malware have become commonplace as cyber-criminals become stealthier, more skilled, and zealous in their desire to breach corporate security defenses. The healthcare industry is a prime target for ransomware attacks because organizations with health data, including third parties, often have less mature security postures compared with other companies such as financial firms. What’s more, the enduring data of people’s health records tends to be more valuable than transient data like credit card numbers.
Ransomware attacks of medical facilities are particularly onerous. When critical patient records and imaging files like x-rays and MRIs are unavailable, lives can be at stake, so restoring access to data at all costs is paramount.
Following ransomware attacks in 2017, some hospitals were forced to cancel planned patient procedures due to vital information being unavailable. For any industry – not just healthcare – the aftermath of a single attack can be enormous, including the loss of sensitive data, clients, brand and reputation, intellectual property, trade secrets, and finances.
Here are just a few examples of the many significant breaches involving ransomware/malware reported to HHS in 2017.
500,000 individuals affected – Airway Oxygen, Inc, learned that unidentified criminal(s) had gained access to their technical infrastructure and installed ransomware in order to deny Purity Cylinder and Airway Oxygen, two affiliated companies, access to their own data. The types of protected health information that were involved in the breach include some or all of the following data regarding their customer/end users and payment sources: full name, home address, birth date, telephone number, diagnosis, the type of service being provided, and health insurance policy numbers.
300,000 individuals affected – Women’s Health Care Group of PA discovered a virus/ransomware was installed on a server/workstation, preventing the hospital from accessing patient data. The types of data exposed – and potentially stolen – included names, addresses, dates of birth, lab test orders, lab test results, blood types, race, gender, pregnancy status, medical record numbers, employer information, insurance details, medical diagnoses, physicians’ names and Social Security numbers.
279,663 individuals affected – Urology Austin was the victim of a ransomware attack that encrypted the data stored on their servers. The investigation indicated that personal information may have been impacted by the ransomware, including name, address, date of birth, Social Security number, and medical information.
There are many steps that a CISO can take to minimize the likelihood/impact of a malware/ransomware breach.
- Ensure anti-virus/anti-malware software is installed and up to date across all endpoints within the business.
- Backup the data and store it off your network. Create the backups as frequently as you can afford and test to ensure that a full restore can be done using the backups.
- Use Group Policy Objects (GPO) restrictions.
- Patch your systems and keep them as current as you can.
- Restrict administrative rights on endpoints.
- Remember that reducing privileges will reduce the attack surface.
- Use the local user account as your primary account.
- Use a Secure Internet Gateway on and off the company network.
- Block users from install anything themselves.
- Go through a helpdesk system (with change control) and have a system administrator only install software that is on the approval list.
- Use a Data Loss Prevention solution and actively monitor it for incidents.
- Use Endpoint Protection and actively monitor it.
- Invest in your Information Security program.
- Tools are great but it takes a team to properly manage and monitor them.
- Establish security awareness campaigns.
- Stress the avoidance of clicking on unknown or unexpected links and attachments in email messages.
- Train often and in a variety of methods (e.g., in person, emails, newsletter, training classes, posters, swag, brown bag lunches, etc.).
Ransomware attacks have caused serious damage worldwide. All organizations should take steps now to avoid becoming the next victim company. Don’t let your company become part of the statistics!"
We could not agree more.
The only thing to add is that email is still the No. 1 attack vector of the organized crime gangs that run ransomware extortion schemes. This graph shows the most important threat vectors over the last 10 years.
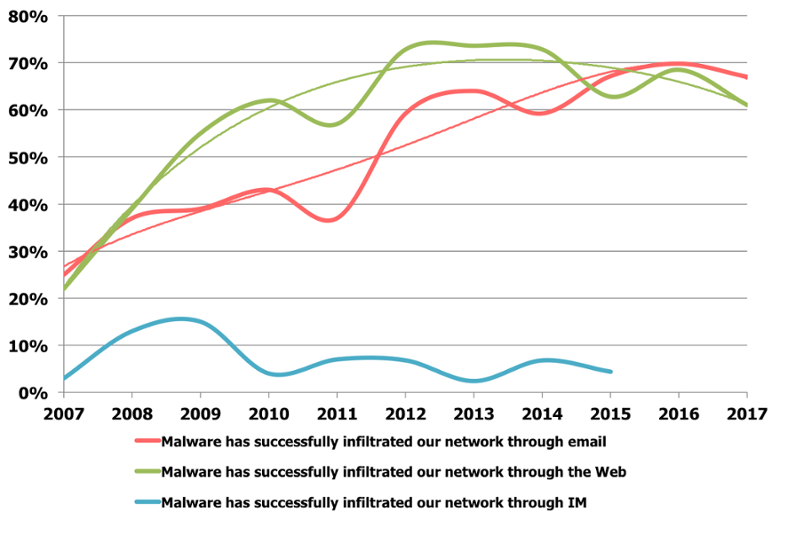
This means that the relative importance of security awareness training is actually top priority and will provide the fastest and often most effective results in preventing ransomware infections.
I strongly suggest you get a quote for new-school security awareness training for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP. If you don't, the bad guys will, because your filters never catch all of it. Get a quote now and you will be pleasantly surprised.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat_get_a_quote_now
Let's stay safe out there.
Warm regards,
Stu Sjouwerman,
Founder and CEO, KnowBe4, Inc






