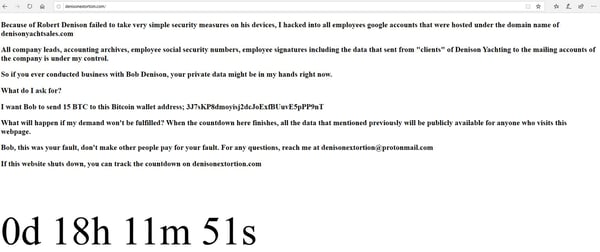
Take a look at that screen. Let it sink in a moment. Imagine if it were your company.
What you are looking at is a screen capture of a ransomware gang’s latest victim. This screenshot was taken in real time while the extortion was still ongoing. Here’s what happened.
The ransomware gang got into a company, in this case it was Denison Yachts. The gang took their time and looked around the company’s network. It determine what the company’s digital crown jewels were…the data that if they copied it and locked it up would cause the most pain.
 Then they went further and stole all the logon credentials of not only the company’s regular network accounts, but the logons of their employees and customers. Then they replaced the company’s main website page with their own ransomware notice. And they made a new website page that anyone could look at when the current website was taken down. And they put a countdown timer that the company and its customers could watch tick down until D-Day.
Then they went further and stole all the logon credentials of not only the company’s regular network accounts, but the logons of their employees and customers. Then they replaced the company’s main website page with their own ransomware notice. And they made a new website page that anyone could look at when the current website was taken down. And they put a countdown timer that the company and its customers could watch tick down until D-Day.
The Evil New Normal
For nearly its entire existence, ransomware used to just lock up data and ask for a ransom. The gang would spend their time, sometimes months, figuring out what data and systems were most important to the victim. That was bad enough. They brought entire systems to their knees. They made most of their victim’s say “uncle” and pay the ransom.
But the savviest companies started to ensure that they had very good, offline backups that the bad guys couldn’t access. There were still some companies not paying the ransom. And this made the ransomware gangs pretty upset.
Then they realized that encrypting some company’s data wasn’t the worst thing they could do. They could do things that a backup wasn’t going to fix. They realized that with the high level of admin access they had they could do anything. And that’s when they started getting smarter…and meaner.
They realized that by copying the data first, and threatening to release it to the company’s competitors and the public in general, that a tape backup wasn’t going to help the victim. Imagine every email you and your employees have ever written out there on the Internet.
Imagine every time some frustrated employee venting about a customer or partner in an email, it got thrown out into the public for everyone to read. This isn’t hyperbole. Ask Sony Pictures. In 2014, hackers (purportedly under North Korean direction) tried to kill a pending movie release that was critical of the current North Korean leader. Sony Pictures did not give into the demand. They likely now wish they had responded differently.
The hackers released emails that showed company executives not talking so fondly of their biggest superstars, including Kevin Hart and Angelina Jolie. It was embarrassing for all involved and likely damaged business relationships permanently.
Let’s face it! Sony Pictures is probably not unique. There’s probably a bunch of emails in any company that if they saw the light of day in public would at least strain relationships if not destroy them. At the very least the media would have a field day with them and your competitors would swoop in to try and pick off emotionally angry customers and partners.
We’re all human. We love our spouses, kids, and parents, but that doesn’t mean that we always talk to them with grace 100% of the time. Sometimes our initial gut reactions to something would be better left off the Internet. Oh, and the Sony Pictures hackers stole the social security numbers and financial information of 47,000 employees. This was the first time I read of not only a massive data theft, but an attack against company employees and their customers.
They want to inflict the most amount of pain and risk immediately.
Now in 2020 this is the new normal for all companies. Ransomware isn’t here to let you take time to decide if your supposedly good backups are really good. They want to inflict the most amount of pain and risk immediately. They want to get paid and they will do anything it takes to make that get happen, including make your company an example of what happens if you don’t pay.
I don’t say this to scare you. I don’t need to do that. The reality all by itself is scary enough. I’m writing to say that everyone needs to wake up and realize that this is the new normal. There was a before…when all ransomware did was encrypt your data and now…where all ransomware is going to start to be this evil and devious all of the time.
We started to see the new pattern emerge in November and December of last year, where after a single ransomware gang started to deploy the new tactics of steal, encrypt, and threaten employees and customers the other gangs saw the greater likelihood of success.
By the end of December 2019 and going into January 2020, the new normal for more and more ransomware is being set. Pretty soon all ransomware will be doing this. We need to shout this new normal from the rooftops because it changes everything. A good backup will not save you, and your cyber insurance policy just became outdated.
Defending Against the New Normal
First and foremost, you need to communicate the new normal to senior management. They need to know the game has changed. If your company has decided they will never pay any ransom, ask them if they are prepared to accept the new reality of what it means to lose control of your data, emails, and the personal information of employees and customers?
You can use this article as part of your business case for budget. KnowBe4 has a new webinar on this subject taught by me which you can share within your organization. Then your defense breaks into four main areas: prevention, detection, response, and communications.
Prevention
Your first line of defense is to stop the bad guys from breaking in in the first place. I know that is a statement that is much harder to do than to say. But if we look at how ransomware is breaking in, the two common attack vectors are social engineering and phishing. which account for 70% to 90% of all malicious data breaches. Nothing else comes close. The exploitation of unpatched software is second with 20% to 40%, and everything else added up all together comes in at 1% to 10%.
You minimize social engineering and phishing by deploying every possible technical control, including content filtering, anti-spam, anti-malware, endpoint protection, reputation services, quarantine/sandboxing services, and email filters, to stop them from getting into your organization – usually through email and web browsers, but it’s expanding to include SMS messages and phone calls.
No matter what technical controls you put in place, some phishing and social engineering will make it past your defenses and your organization’s employees will be tested to see if they can spot it and respond appropriately. You need good security awareness training to accomplish that. Use a combination of training and simulated phishing attacks, on at least a monthly basis to make the education stick.
I cover all the needed policy, technical controls, and security awareness training controls in my webinar entitled Stay Out of the Net: Your Ultimate Guide to Phishing Mitigation. If you are interested in cutting down phishing and social engineering you won’t find a better resource than our list of webinars and whitepapers at: https://www.knowbe4.com/resources
Second, make sure all your critical patches are applied in a timely manner, including operating system, browsers, browser-add-ons, web server software, database software, and remote management software – as the key things you focus on first and best. Those are the software programs that will be attacked the most.
Third, ransomware often attacks remote management software and in particular Microsoft’s Remote Desktop Protocol (RDP). The main way they attack it is by password guessing. Make sure you patch RDP so it can’t be exploited. Then enable RDP only to accept connections from computers with approved digital certificates.
If the attacker’s machine doesn’t have the right digital certificate they won’t be able to connect to even begin password guessing. And of course, don’t use very easy to guess passwords. Your RDP passwords do not have to be super long and complex. Eight-characters long without complexity will work, as long as they are not real words or any of the common password lists (e.g. password, password123, qwerty, etc.).
Longer is better, but it’s more important to make sure they aren’t easily guessable. Plus, turn on account logons to lock out an account after more than X number of guesses. In Windows, make sure you rename your Administrator account to something the hacker can’t easily learn or guess. The built-in Administrator account can never be locked out, but if you rename it the hacker can’t even begin to guess against it.
Then do all the other defense-in-depth things you know you need to do to secure your computing environment. There is way too much to cover in this short article. Get started by putting down social engineering and phishing using a combination of technical controls and training. Patch your software. Make sure your passwords are not guessable. And then everything else.
Detection
You have to assume that at some point in your career that badness will get by all your preventative controls. If that is true, the next best thing is early warning. You need a combination of detection controls including:
- Intrusion Detection Systems (host and network)
- Endpoint Detection
- Crowdstrike-like Monitoring Client-side Tools
- Ability to detect massive number of suddenly changing files (from encryption)
- Data Leak Prevention Tools
- Network Traffic analysis
- Outgoing flows, computer-to-computer, server-to-client, client-to-client, server-to-server
- Honeypots
I’m a big believer in the last recommendation, honeypots. Take a system you are getting ready to decommission and turn it into a honeypot. Secure it like you do every other computer that you already have and place it around your big database servers, preferably with a name and IP address similar to the other servers.
Then just monitor it for any unexpected connections. This means you’ll need to figure out all the normal connections from things like your antivirus update servers, patch management services, etc. But once you figure out what should be trying to connect to the honeypot legitimately, any other connections are malicious by definition.
I’ve yet to meet the hacker, in a ransomware gang or not, that didn’t explore the network first and they don’t know the difference between a real, live system and a honeypot that looks like a real live system. And when they touch it or try to logon to it, alert and investigate.
Response
If the worst happens, and your data and credentials are stolen (and data encrypted), you need to stop the damage the best you can, find out how the hackers got in, shut off their continued access, and then plot a recovery plan. How good is your incident response? What can you do once your data and credentials are stolen? How can you best protect and defend your organization, customers, and employees based on the current set of facts. Does your incident response scenarios include the new reality of ransomware? If not, time to get busy.
Communications
Lastly, when your company’s data and credentials are stolen and are possibly going to be posted publicly, and all your employees and customer data and logon credentials are compromised, you’re going to have to address it to all parties involved.
As part of your incident response planning I would get senior management and a specialist communications team involved ahead of time, before the pain happens. You and everyone else involved needs to understand what to do when and what can be shared when. You don’t want to be considering these decisions for the first time in the middle of battle.
Make sure that the "new evil normal" of ransomware are communicated to everyone top to bottom of your organization. Your security awareness training needs to be updated to make everyone aware of the new reality, what the risks are, and how you plan to respond.
You can begin by using this article and inviting people to view the related webinar and use any available resources you can find. If you have any questions or need clarification feel free to contact me at rogerg@knowbe4.com. We will help you fight the good fight.
If there is nothing else that you take away from this article it is this: Ransomware is now stealing your data, stealing your own and your customer’s data and credentials, and publicly posting all of it to shame you on public-facing websites. It used to be fairly rare, but it’s now the new norm. Are you prepared?




