 A number of high-profile Twitter accounts were hacked including those of Elon Musk, Bill Gates, Kanye West, Joe Biden and Barack Obama. This is clearly the worst hacking incident in Twitter’s history. It began 7/15/2020 when compromised accounts began posting a bitcoin scam.
A number of high-profile Twitter accounts were hacked including those of Elon Musk, Bill Gates, Kanye West, Joe Biden and Barack Obama. This is clearly the worst hacking incident in Twitter’s history. It began 7/15/2020 when compromised accounts began posting a bitcoin scam.
In a series of tweets posted under its support channel, Twitter said that its internal systems were compromised, confirming theories that the attack could not have been conducted without access to the company’s own tools and employee privileges. In the industry it's called God Mode and Facebook has had trouble with this in the past too.
Employees Fell For Social Engineering Attack
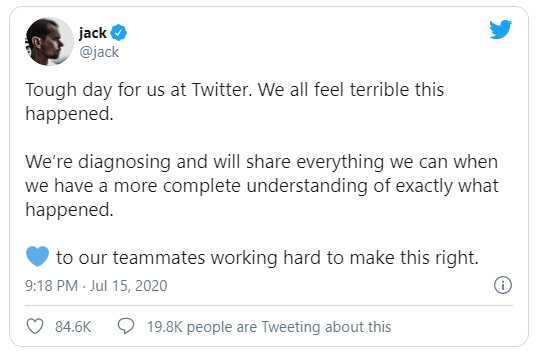
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools,” the first tweet in a multi-tweet explainer thread reads. “We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf.” Looks like Twitter found out that more than one person appears to have been involved in the hacks, not just one individual, and also that numerous employees were compromised, too. Twitter CEO Jack Dorsey said:
Teresa Payton, a former White House chief information officer and current CEO of Fortalice Solutions, said that she expects Twitter to provide a full report detailing how and why these accounts were hacked. She also warned that information such as direct messages may have been stolen from the affected accounts and could be released or used in the future.
“They’re going to need to apologize to the VIPs and to the individuals who were defrauded and fell for the scam,” Payton told CNBC. “The next thing they’re going to need to do is to conduct a thorough and transparent investigation, and they’re going to need to share what they can about who the attackers were and how they pulled this off.”
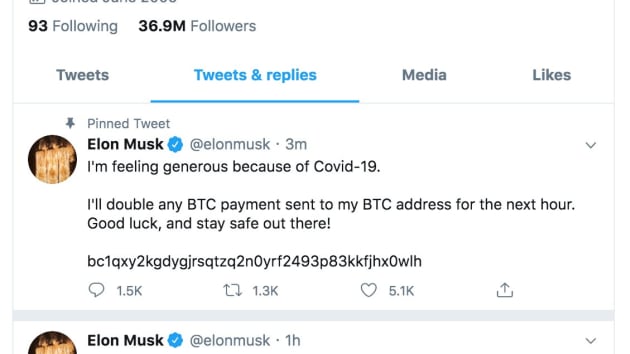
Here is an example screenshot, many have been deleted.
Twitter says that once it became aware of the unfolding situation, it “immediately locked down the affected accounts and removed Tweets posted by the attackers.” It also took the unprecedented step of disabling the ability for verified accounts to send new tweets.
“This was disruptive, but it was an important step to reduce risk. Most functionality has been restored but we may take further actions and will update you if we do,” the update reads. “We have locked accounts that were compromised and will restore access to the original account owner only when we are certain we can do so securely.” Twitter also says that it’s taken steps internally to “limit access to internal systems and tools while our investigation is ongoing.”
Problem is, what --else-- did the bad guys get theirs hands on? Direct Messages in Twitter could be used for a variety of nefarious purposes. Now, undoubtedly you will immediately see everyone come up with "use MFA" to protect your accounts, but MFA is not going to save you from social engineering angle.
Step your high-risk employees through new-school security awareness training and test, test, test them with simulated social engineering attacks so that they are inoculated against this kind of compromise.
UPDATE, Brian Krebs has an interesting post who might be behind this attack.
UPDATE: Twitter Says Hackers Downloaded Some Users’ Personal Data in Recent Attack. Article at Wall Street Journal: https://www.wsj.com/articles/
UPDATE: NY TIMES has interview with the hackers who social engineered Twitter: https://www.nytimes.com/2020/07/17/technology/twitter-hackers-interview.html
UPDATE: Twitter Hijackers Used Well-Honed Fraudster Playbook: https://www.inforisktoday.com/twitter-hijackers-used-well-honed-fraudster-playbook-a-14655?
UPDATE: Florida (Tampa) teen arrested, [case number PDF], charged with being “mastermind” of Twitter hack: https://arstechnica.com/tech-
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!




