Oh my. Bad guys have come up with a sinister new strain of blackmail/sextortion. Just when you thought things couldn't get worse, the bad guys sink lower.
Eric Howes, KnowBe4's Principal Lab Researcher sent me a screenshot of an attack now live out there in the wild. It claims the CIA will bust you for child porn unless you pay 5,000 dollars and only then "your records will be deleted". Here is a screenshot:
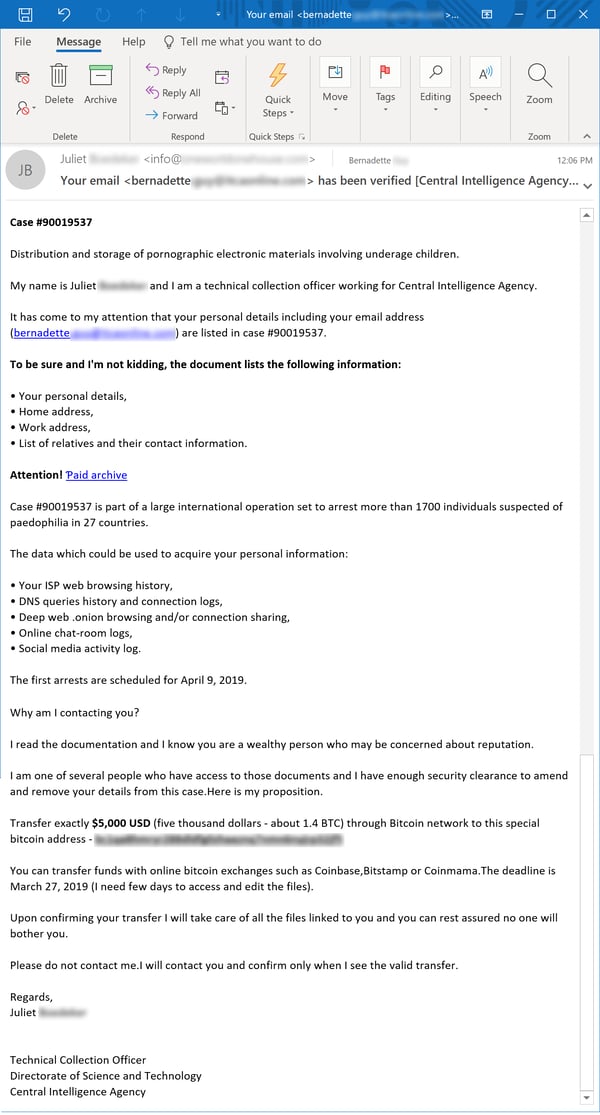
Apart from the very scary and expensive extortion, it also contains a malicious link. What lies behind that link (credentials phish or malware download) we don't know, as the target web page for that link has been taken down. But it sure looks like the bad guys have two attack vectors and are also trying to infect the workstation.
It will become more serious
KnowBe4 is seeing a rise in this blackmail-type phishing... and it will become more serious. With the capabilities of recent destructive malware and ransomware the following scenario becomes highly probable: If you don't pay the ransom—but click on the link, worried to death—they will put actual child pornography on the users' machine, and/or they stuff your users' search history with fake searches. Then they will anonymously notify the FBI or other Law Enforcement. It's a setup and the intent is to actually cause the person to get arrested and massively disrupt your organization at the same time.
This could absolutely ruin someone's life
Unfortunately, technically this is not that difficult to do and we see the potential this develops into highly targeted spear phishing attacks on CEOs, politicians, high-net-worth individuals, celebrities, etc. This could absolutely ruin someone's life.
Child porn would be a gruesomely effective setup. Law enforcement accepts absolutely no excuses when they encounter it on a device, as malware researchers and investigative journalists have discovered to their horror. Even law enforcement officers who deal with it are monitored and supervised carefully.
The bad guys here have two attack scenarios and would have to make a critical decision. If you’ve compromised the devices/accounts of a high value target, what’s the most productive way to extract value from that target?
- Lie low and exploit the compromised devices and accounts for long-term gain (information, money, etc.), or
- Go the extortion route, which would inevitably bring scrutiny from law enforcement, IT specialists, and others with a stake/interest in investigating those devices and accounts.
Different cyber crime gangs could be operating with divergent “business models.” Something similar to this was all over the news recently. The recent dust-up between Jeff Bezos and AMI (parent company of the National Enquirer) comes close to the above attack model if Bezos' phone would have been compromised. Think of the potential value of getting super-sophisticated backdoor Trojans on the devices of Mr. Bezos.
What kind of world are we living in?
It would be important for the cyber criminals to set a precedent like ransomware did: pay the ransom and get your files back. A few famous people being made an example of with a repulsive attack like this, and we bet people will start paying.
This could even be developed into a criminal extortion subscription, modeling the old "protection money" the mob used to run. What kind of world are we living in?
One thing is for sure
We absolutely have to get our users aware of these horrible scams, and make sure they stay cool, calm and collected when they suddenly see "something all claws" that made it through the filters, and instead of panic, click on the Phish Alert Button.
Do your users know what to do when they receive a suspicious email?
Should they call the help desk, or forward it? Should they forward to IT including all headers? Delete and not report it, forfeiting a possible early warning?
KnowBe4’s Phish Alert button now also works with Outlook Mobile for iOS and Android. This enables your users to report suspicious emails from not only their computer but from their mobile inbox as well.
(If you’re running Office 365 and want to give your end-users the ability to report suspicious emails from from their mobile inbox, you can enable the official Outlook Mobile app for iOS or Android directly from the KnowBe4 console. )
The Phish Alert Button gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user's inbox to prevent future exposure. All with just one click!
Best of all, there is no charge!
- Reinforces your organization's security culture
- Incident Response gets early phishing alerts from users, creating a network of “sensors”
- Email is deleted from the user's inbox to prevent future exposure
- Easy deployment via MSI file for Outlook, G Suite deployment for Gmail (Chrome)
This is a great way to better manage the problem of social engineering. Compliments of KnowBe4!
Get your Phish Alert Button:
https://www.knowbe4.com/free-cybersecurity-tools/phish-alert-button




