 Intrepid investigative Reporter Brian Krebs had the news first. "The criminal group behind the REvil ransomware enterprise has begun auctioning off sensitive data stolen from companies hit by its malicious software. The move marks an escalation in tactics aimed at coercing victims to pay up — and publicly shaming those don’t. But it may also signal that ransomware purveyors are searching for new ways to profit from their crimes as victim businesses struggle just to keep the lights on during the unprecedented economic slowdown caused by the COVID-19 pandemic."
Intrepid investigative Reporter Brian Krebs had the news first. "The criminal group behind the REvil ransomware enterprise has begun auctioning off sensitive data stolen from companies hit by its malicious software. The move marks an escalation in tactics aimed at coercing victims to pay up — and publicly shaming those don’t. But it may also signal that ransomware purveyors are searching for new ways to profit from their crimes as victim businesses struggle just to keep the lights on during the unprecedented economic slowdown caused by the COVID-19 pandemic."
You can count on other cyber organized crime gangs to follow this "innovation".
Krebs continued with: "Over the past 24 hours, the crooks responsible for spreading the ransom malware “REvil” (a.k.a. “Sodin” and “Sodinokibi“) used their Dark Web “Happy Blog” to announce its first ever stolen data auction, allegedly selling files taken from a Canadian agricultural production company that REvil says has so far declined its extortion demands.
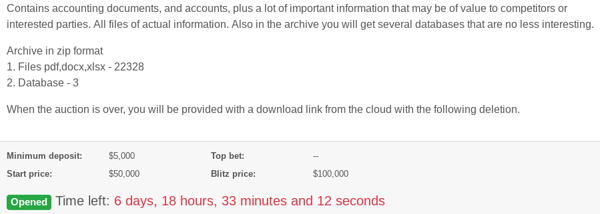
The victim firm’s auction page says a successful bidder will get three databases and more than 22,000 files stolen from the agricultural company. It sets the minimum deposit at $5,000 in virtual currency, with the starting price of $50,000.
Prior to this auction, REvil — like many other ransomware gangs — has sought to pressure victim companies into paying up mainly by publishing a handful of sensitive files stolen from their extortion targets, and threatening to release more data unless and until the ransom demand is met.
Experts say the auction is a sign that ransomware groups may be feeling the financial pinch from the current economic crisis, and are looking for new ways to extract value from victims who are now less likely or able to pay a ransom demand.
Lawrence Abrams, editor of the computer help and news Web site BleepingComputer, said while some ransomware groups have a history of selling victim data on cybercrime forums, this latest move by REvil may be just another tactic used by criminals to force victims to negotiate a ransom payment." Continued at KrebsOnSecurity
It goes without saying that stepping your users through new-school security awareness training, which includes frequent simulated social engineering tests, will go a long way to mitigate against ransomware infections like this which more and more require you to file a data breach notification. Story continues at:
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!




