Sophos has discovered a scary new strain of very sophisticated ransomware called MegaCortex. It was purpose-built to target corporate networks, and once penetrated, the attackers infect your entire network by rolling out the ransomware to all servers and workstations, using your own Windows domain controllers.
Sophos have detected infections in the United States, Italy, Canada, France, the Netherlands, and Ireland.
This is a fairly new strain, so not all that much is known yet about how the encryption works, how they are getting in, or if ransom payments are being honored.
How Megacortex Strikes
Sophos made an interesting additional discovery: if the Emotet or Qakbot Trojans have been present on networks that have also been infected with MegaCortex, that suggest that the attackers are paying Trojan operators for access to infected systems just like the RYUK strain.
"Right now, we can’t say for certain whether the MegaCortex attacks are being aided and abetted by the Emotet malware, but so far in our investigation (which is still ongoing as this post goes live), there seems to be a correlation between the MegaCortex attacks and the presence on the same network of both Emotet and Qbot (aka Qakbot) malware."
MegaCortex Uses Your Own Windows Domain Controllers
It is not 100% clear yet how the bad guys are gaining access to your network, but victims have reported to Sophos that the attacks originate from a compromised domain controller. On the DC, Cobolt Strike is being dropped and executed to create a reverse shell back to an attacker's host.
Using that shell, the attackers take over your DC and configure it to distribute a copy of PsExec, the main malware executable, and a batch file to all of the computers on the network. It then executes the batch file remotely via PsExec. The batch files seen by Sophos will terminate 44 different processes, stop 199 Windows services, and disable 194 services.
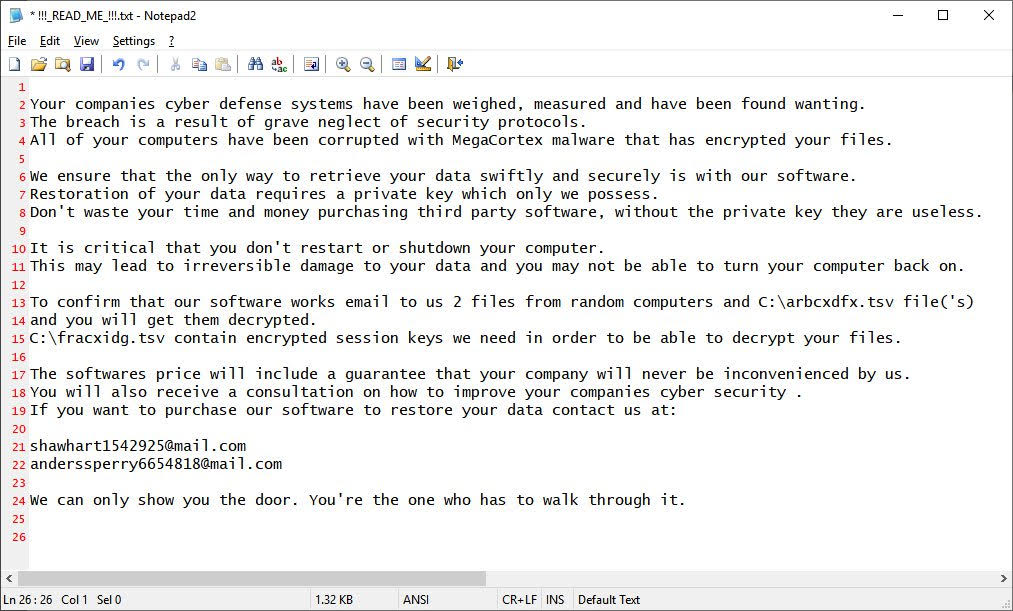
During the encrypting of a system, the ransomware will append an extension to file names, which in one case is .aes128ctr. This means that a file named marketing.doc would be encrypted and renamed to marketing.doc.aes128ctr. It is not known yet if these extensions are static or created dynamic with each infection. Here is a screenshot of the ransomware note:
Secondary Payloads Present
In addition to the the MegaCortex Ransomware payload, Sophos has found what they call "secondary main components" on the computer. Hashes of some of these payloads are listed at the end of Sophos' report.
Security researcher Vitali Kremez examined some of these secondary payloads and in a conversation with BleepingComputer explained that these files are Rietspoof.
Rietspoof is a multi-stage delivery system that is used to drop multiple malware payloads on a computer. Because of that it's not known yet if this is the malware dropping MegaCortex or if it is being installed as a secondary payload along with it.
How To Block Megacortex Infections
Have weapons-grade backups, off-site, not made accessible to ransomware which often targets all the backups it can see.
Make sure that your network does not make any RDP Services publicly accessible via the Internet. Put any machine that runs RDP behind a firewall and make it only accessible through a VPN.
While this ransomware is not being spread via spam, it is possible that it is being installed by Trojans that are coming in through email. That's why it is important that you train your users to identify phishing attacks and not fall for social engineering attacks, tricking them into opening malicious attachments they did not ask for.
New-school security awareness training for your whole organization is as important as ever.
Brand-New Ransomware Simulator Tool Now with Cryptomining Scenario
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
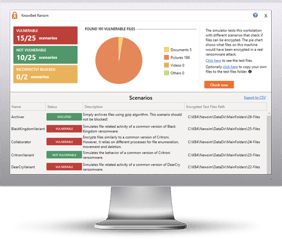
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Download the new Ransim here:
https://info.knowbe4.com/ransomware-simulator-tool-1